![]()
On June 13, 2025 was disclosed vulnerability in the iOS version of the Air Keyboard app that exposes users to remote input injection over Wi-Fi. The flaw, documented in CXSecurity Report, allows an attacker on the same local network to send keystrokes to a target iOS device without authentication. As of this writing, the app remains available on the App Store and is still affected by the vulnerability. With the report is also published prove of concept python script. In this blog I will test the exploit, have a look on their Android version of Air Keyboard app and conclude with security tips.
Remote Input Injection vulnerability in Air Keyboard #iOS App Still Unpatchedhttps://t.co/aMbcHZMcw3 pic.twitter.com/vm8O2LmtPk
— Mobile Hacker (@androidmalware2) July 17, 2025
What is Air Keyboard?
According to its official information, Air Keyboard is an app that turns your mobile device into a wireless keyboard and mouse for your computer. It connects over the local network and sends or receives input to or from a companion desktop application installed on Windows or macOS. The app’s goal is to offer convenient remote control for presentations, media playback, or general PC use, all from your smartphone or tablet.
Exploiting the Vulnerability: Input Injection on iOS
The vulnerability stems from the iOS app listening on TCP port 8888 for incoming input — without any form of authentication or encryption. A proof-of-concept Python script included in the advisory demonstrates how an attacker can craft data and remotely inject arbitrary keystrokes to the victim’s device. A video demonstration further confirms how trivial the attack is to execute. Because the iOS app does not verify the origin or integrity of the incoming commands, any device on the same Wi-Fi network can send input as if it were the user.
The app remains available on the App Store in this vulnerable state, with no fix or warning issued to users.
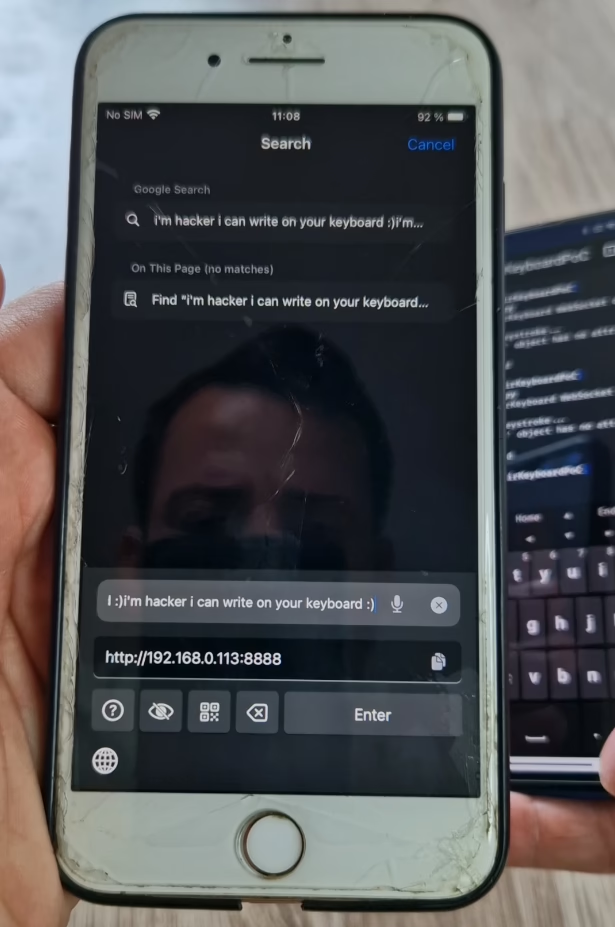
Android Version: Safer, But Not Immune
The Android version of Air Keyboard is architecturally different. It requires an initial handshake where the mobile checks a 4-character password — randomly generated on first launch — encrypted using a hardcoded AES key. This provides a basic layer of security that blocks unauthorized connections from injecting input.
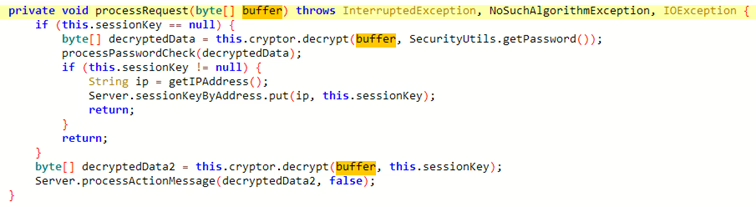
However, when the same PoC script designed for iOS is run against the Android app (which listens on port 55535), the app fails to handle the unexpected payload and crashes. While this doesn’t allow input injection, it does enable a basic form of denial-of-service (DoS), temporarily knocking out the app until it’s restarted.
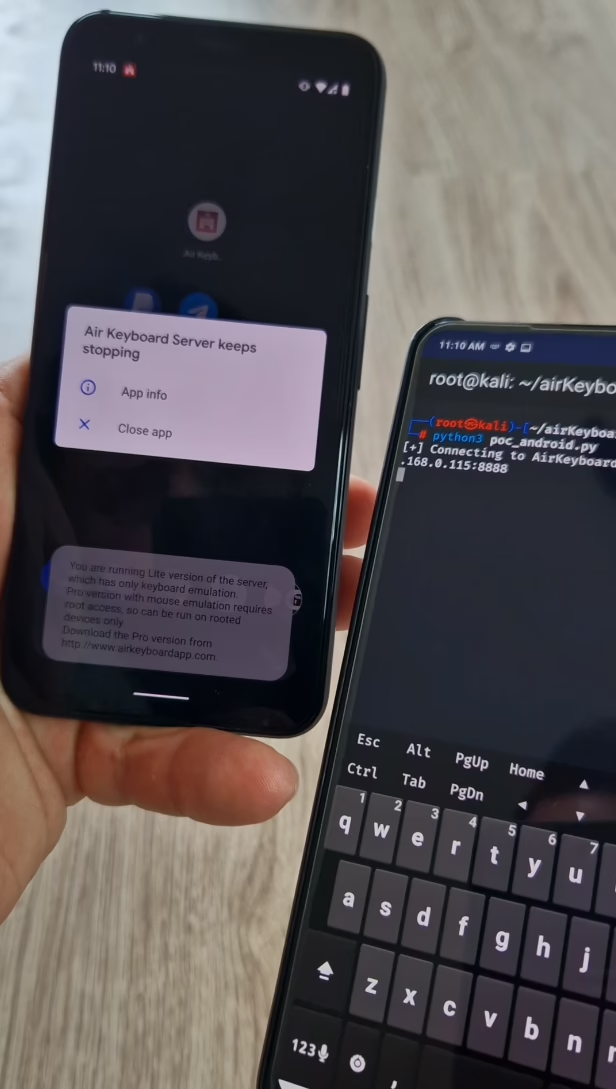
Open Ports Can Be Hidden Risks
For the average smartphone user, identifying whether an app is listening on a network port is nearly impossible. Mobile operating systems don’t typically expose this kind of network activity, and malicious or poorly designed apps can quietly open ports without the user’s knowledge. This lack of transparency was recently highlighted by research on Meta’s Instagram and Facebook Android apps, which were found to open a local port and use it to communicate with the browsers, allowing user fingerprinting across visited websites.
To detect open ports manually, Android users with developer tools can use ADB and run the command:
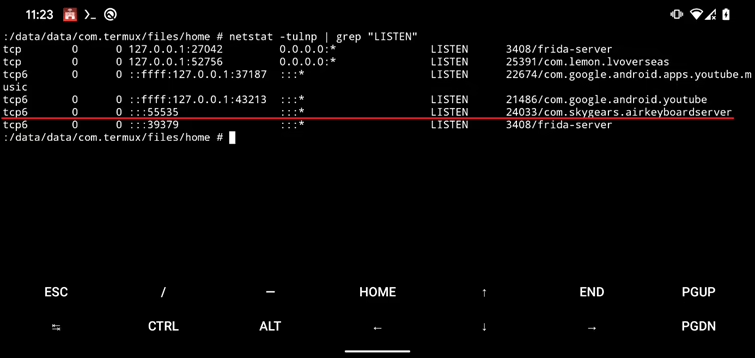
netstat -tulp | grep LISTENThis shows which ports are listening for incoming connections. On rooted devices, you can also identify which app (by package name) is responsible for the port. Unfortunately, iOS users have no such visibility unless jailbroken.
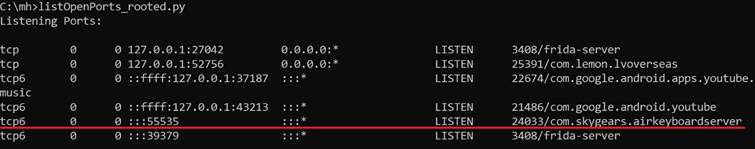
You can do the same check even on the rooted Android itself, without needing to run ADB command.
Attack Surface and Network Scanning Risks
Because both the iOS and Android versions of Air Keyboard listen on fixed ports (8888 for iOS, 55535 for Android), an attacker on the same LAN can easily scan for active services using tools like nmap. To learn more about on how to use nmap on Android check NetHunter Hacker XV: Use Nmap for network scanning blog.
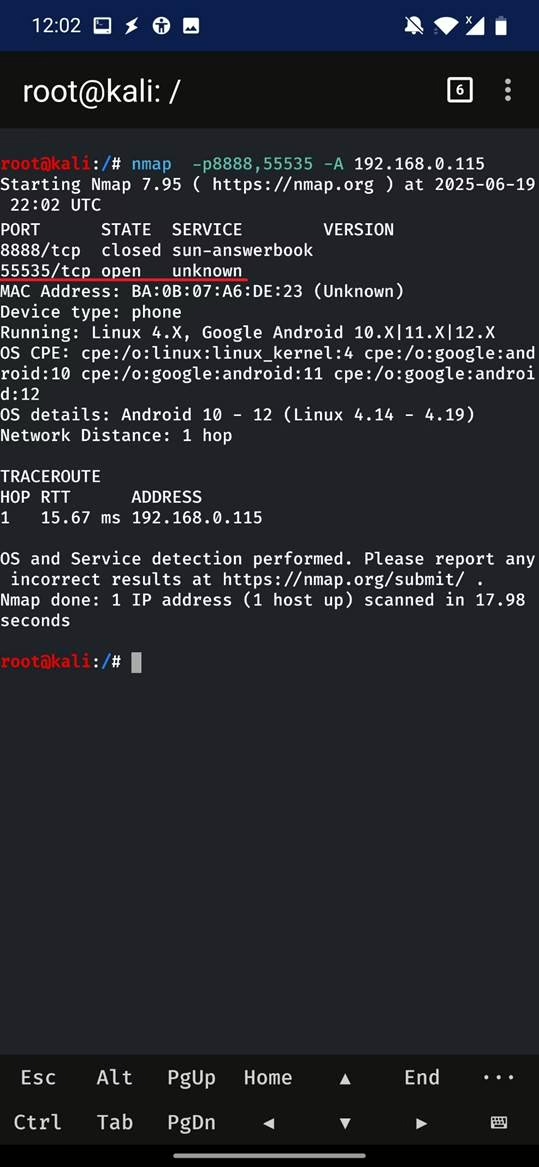
Once a target is identified, the attacker can exploit the iOS app to inject input or crash the Android app. This makes the vulnerability particularly concerning for public or shared networks — such as those in offices, schools, or cafes — where multiple devices connect to the same subnet.
How to Protect Yourself
If you’re using Air Keyboard, here are a few steps you should take:
- Stop using the iOS app immediately until the developer releases a fix.
- Restrict your device to trusted Wi-Fi networks only.
- Monitor open ports on your device, if possible, to detect unauthorized services.
- Keep your apps and operating system up to date for security updates.
- For Android users, although the vulnerability is less severe, consider the crash potential and whether the app is critical for your workflow.
Final Thoughts
This vulnerability in Air Keyboard for iOS highlights how seemingly convenient tools can pose significant security risks when not properly secured. The lack of authentication for remote input opens the door to input hijacking, which could lead to privacy breaches, accidental system changes, or even malicious commands being run on the target machine. With the app still unpatched, users should take immediate action to mitigate risk — and developers should treat network-facing functionality with far greater scrutiny.