![]()
So far, it was possible to spam through proximity paring messages only iOS devices, either using Flipper Zero, Arduino board or any Android as explained in my previous blog here. However, recently developers of Xtreme firmware for Flipper Zero pushed and update of BLE Spam application that besides spamming iPhones can also spam Android and Windows devices. This update is not available in officially released version of Xtreme firmware, however you can download it as dev release. This dev updates are available on XFW Discord or you can download it easily from here.
In this blog I will test it using Flipper Zero against iOS, Android and Windows at once and show you how to send these Bluetooth Low Energy (BLE) spam messages from any Android smartphone and even customize them.
How it works?
Similar technology as uses Apple to pair BLE devices with iPhone or iPad is used by Windows and Android systems. Apple calls it proximity pairing. Windows Swift Pair and Google’s Fast Pair service. All of them works the same. If in the vicinity of a devices is a BLE gadget such as headphones that are ready to pair, they start to broadcast advertising beacons to notify these devices.
If these beacons are intercepted, they could be replayed by other BLE device to spoof the gadget or even advertise custom messages.
Spam iOS, Android, and Windows at once
This is another level; you can locally spam three major operating systems at once using Flipper Zero. It is a local attack, however, based on my tests, for long distance BLE messages it is around 50 meters when targeting iOS and Android. For Windows, the range is less than a meter.
If you want to spam each system separately, you can do so as well. Since iOS is already covered in my previous blog, I will continue with Android a Windows.
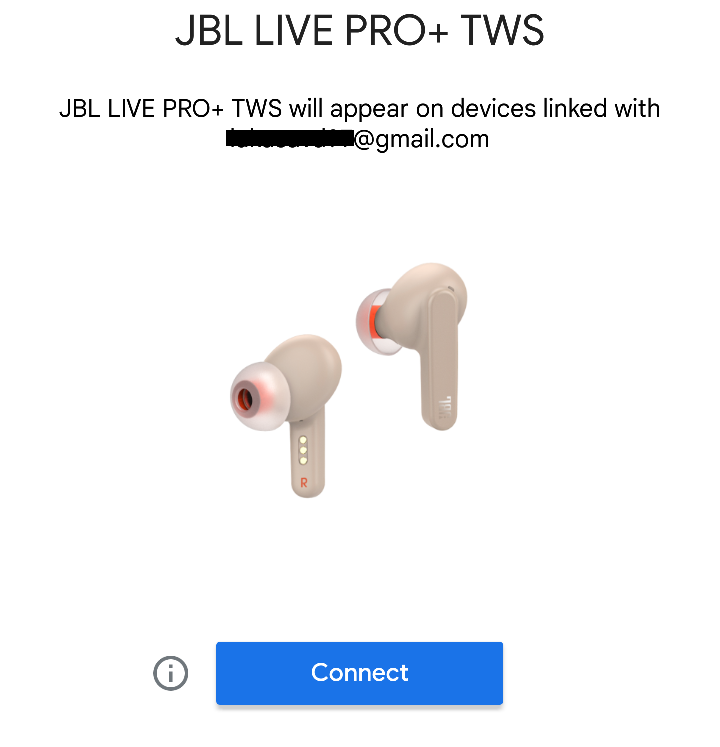
Starting with Android, in Flipper go to Apps -> Bluetooth -> BLE Spam and search for Android Device Pair, see Figure 1.

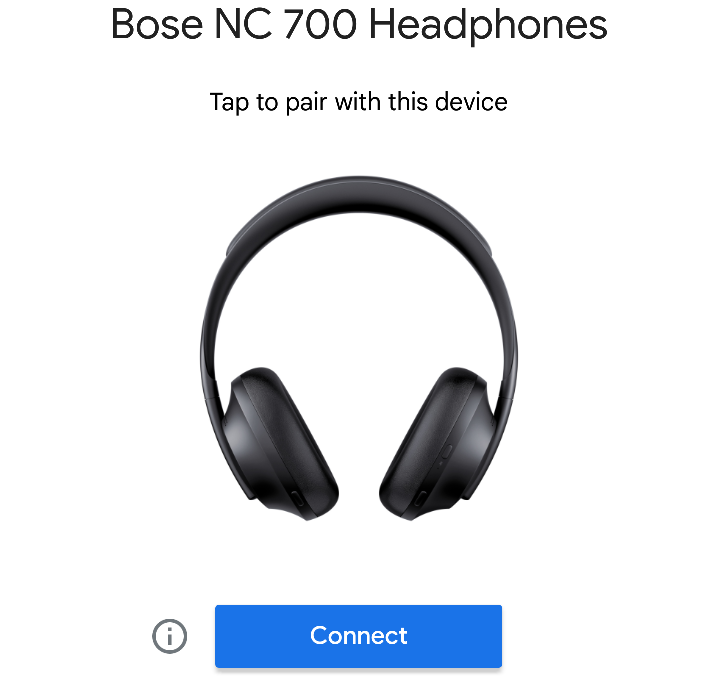
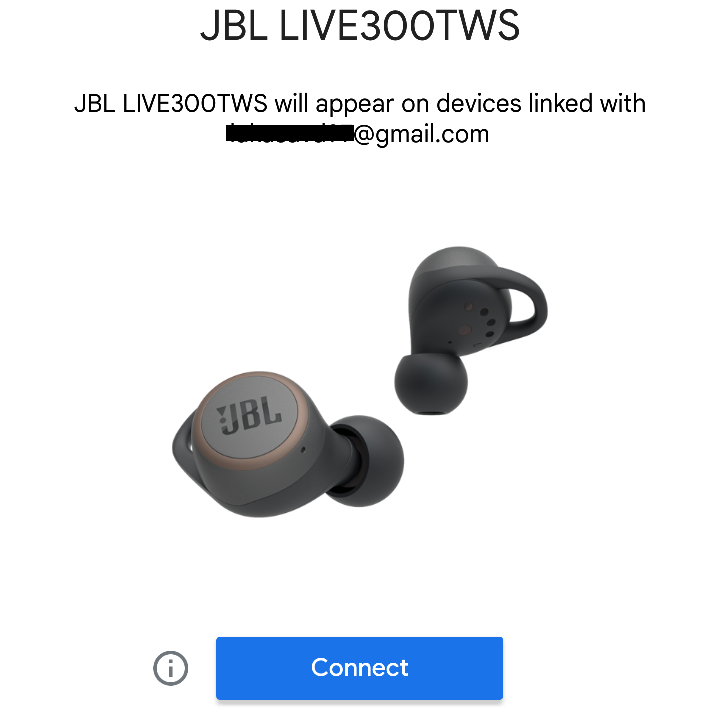
Once user taps on Start, Flipper starts to send advertisement beacons simulating connection requests from five defined devices such as Bose NC 700, JBL Buds Pro, JBL Live 300TWS, JBL Flip 6, and Pixel Buds. You can see the notifications below. These notifications are displayed only if user has enabled Scan for nearby devices option, which is enabled by default.
Based on the source code, these notifications are send randomly, so you can’t use only one type. If you would like to use only one, I will show how in Trigger Android and Windows BLE spam from Android section below.
To target Windows, these notifications are displayed if Windows has enabled Show notifications to connect using Swift Pair, which is enabled by default on Windows 10. From BLE Spam menu select Windows Device Found and one of the hard-coded messages will be displayed on the right bottom of Windows machine, see Figure 7.
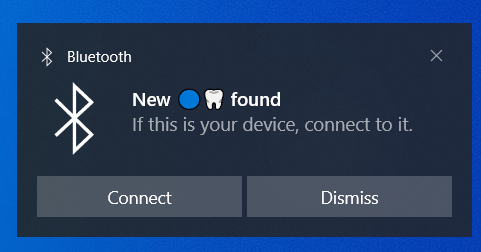
Flipper randomly selects one of the six messages and displayed them to user. Text of messages is below and found in the source code:
- Assquach💦
- Flipper 🐬
- iOS 17 🍎
- Kink💦
- 👉👌
- 🔵🦷
On of the new option in BLE Spam app is Kitchen Sink. This attack randomly triggers popping notifications on iOS, Android and Windows at the same time as you can see in the video below.
Custom spam messages
Thanks to Willy-JL and Spooks4576, it is possible to even send custom notification BLE messages to Android and Windows. To send these messages to Windows machine doesn’t requires any special settings being enabled on the computer, since they are enabled by default. In this case it is notifications using Swift Pairing. However, there is a one time notification to enable or disable showing these notifications, see Figure 8.
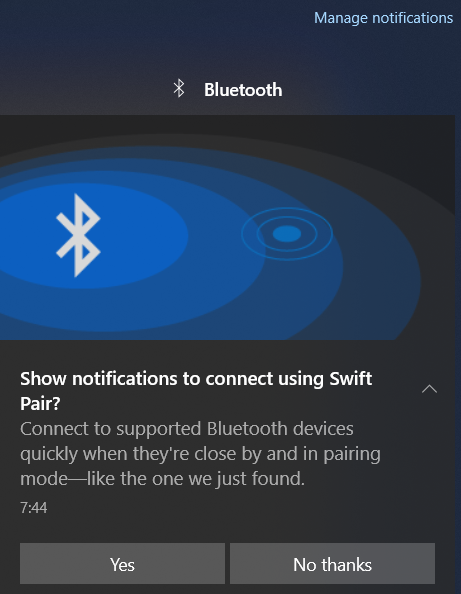
This popup is displayed only the first when user pairs new BLE device.
If displaying notifications are enabled, we can make and push our own messages. User will define a text, and advertises it. I will explain how, in the section below.
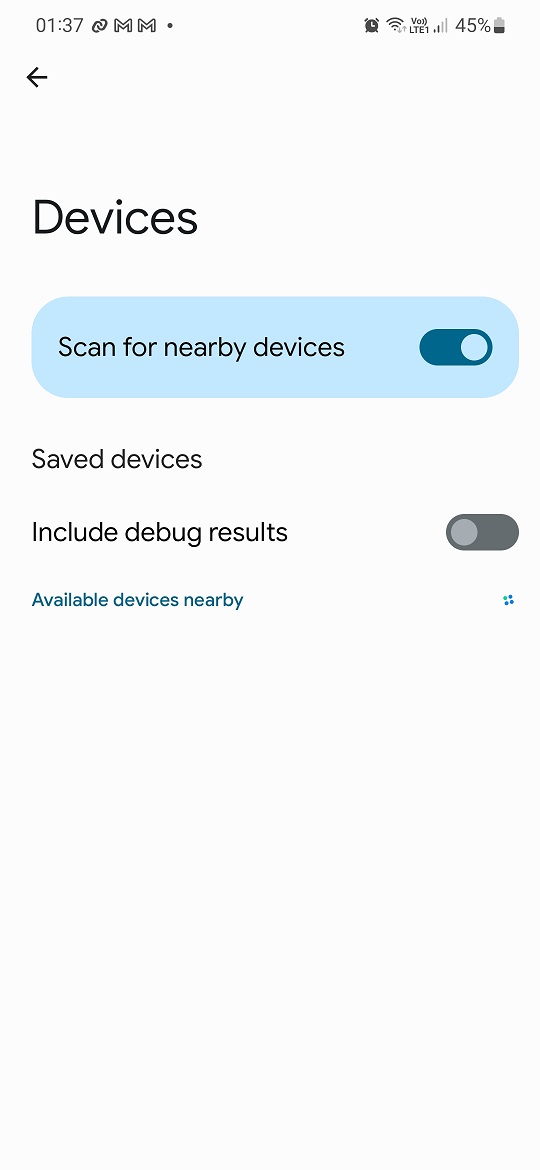
To send custom notifications to Android device, it is necessary to first enable Include debug results from Settings -> Google -> Devices & sharing -> Devices. This is disabled by default.
If you enable it, Flipper Zero using the same option as before – Android Devices Pair – will besides already mentioned five notifications randomly roll through five more, you can see them below.

Can you recognize who is in the last notification? It is Talking Sasquach. This custom pop-up was built specifically for him, since he is cooperating and consulting new BLE Spam features with Spooks4576 developer. If you would like to know more, I advise you to check his recent YouTube video about Flipper Zero Custom BLE Spam for Android & Windows.
Trigger Android and Windows BLE spam from Android
To push these notifications, you don’t need to have Flipper Zero. Android smartphone is enough.
As we were able to port and trigger BLE spam messages from any Android running nRF Connect app for iOS in previous blog, now we will do the same for Android and Windows spam pop-ups.
Let’s start with Windows. In nRF Connect and ADVERTISER tab, you need to create a New advertising packet by tapping on plus symbol in right bottom corner. Click on ADD RECORD, select Manufacturer Data. In the first row enter 0006 and in the second 030008 prefix. After the prefix, enter your notification message in HEX format. See Figure 10. For example, to display Hack the planet, enter value 030008224861636B2074686520706C616E657422. To display custom message, you can use ASCII to HEX convertor.
To impersonate one of five defined devices that would pair with Android, you need to create a new advertising packet and add three records. Starting with Service Data. In the first row define FE2C as UUID which represents Fast Pair service. In the second row, enter HEX value that represents a device to impersonate. The list of five devices is available on Flipper Xtreme Firmware Github and for convenience I copied it below:
- 0xCD8256, // Bose NC 700
- 0xF52494, // JBL Buds Pro
- 0x718FA4, // JBL Live 300TWS
- 0x821F66, // JBL Flip 6
- 0x92BBBD, // Pixel Buds
- 0xAA1FE1, // ClownMaster
- 0xAA187F, // VBucks
- 0xF38C02, // Boykisser
- 0x1448C9, // BLM
- 0xD5AB33, // Xtreme
- 0x13B39D, // Talking Sasquach
- 0x3D45DC, // Mobile Hacker
For the second record, add Tx Power. For the third one select Service UUID. In the edit box input value FE2C. You can see all values in the Figure 11.
In Figure 12. you can see successful demonstration of popping Pixel Buds on a smartphone.
It is also possible to create custom messages, as visible in the Figure 13. However, I decided not to publish full tutorial since it might be easily missed.
Prevention
To prevent these spam messages on iOS, you can only disable Bluetooth when you don’t need it. On Windows it is easier, since you have to disable Swift Pairing notifications in Bluetooth & other devices and disable Show notifications to connect using Swift Pair, as visible in Figure 14.
Android uses a model where the same device can send only few paring (around five) notifications in a row, and then it will be ignored by the system. If Android users would like to prevent even these notifications, they can disable them in Settings -> Google -> Devices & sharing -> Devices -> Scan for nearby devices as you can see in Figure 15. or by disabling Bluetooth.


how to do with kali linux it
I made a whole video on how to do this, that’s me in the last custom Android Spam! Check it out on my YouTube! https://www.youtube.com/watch?v=d8cSKNmBwX4
Hello Talking Sasquach! Thanks for letting me know, I updated the blog with this information and included a link to your video. Best!
Hello, is it possible to spam multiple times for windows on the same attack ? I need to disable/enable the “packet” on NRFConnect for each “attack”
If you mean to send them in the loop, then I dont think nRF app allows that
I’d really like to see the kitchen sink attack come to nethunter
I can ping one of NH developers to ask, but it would be necessary to implement the whole BLE advertisement beacons functionality which might take a lot of time.
Avoid Rough Master! Skid just ripping code!
Like it
I’m trying to follow on my Pixel 8 Pro, however in your screenshots it shows the Tx Power as 1dBm, but when I set the packets up they only show as -7 dBm for me – any ideas?
This is a power of your signal. It is the strongest if set to 1dBm. You can easily change it in Options menu when editing Advertising packet. I explained this steps in my previous blog: https://www.mobile-hacker.com/2023/09/07/spoof-ios-devices-with-bluetooth-pairing-messages-using-android/ Feel free to check it out.
Can i spam iPhone from iphone
Yes, I believe it could be possible.
Why doesn’t it work for me like you, I have installed the nrf application on android but it doesn’t show me the application like you, in the options part it shows me only Connectable and Scannable while when I click the button to release it (Advertisement duration) it does not show me like you do. Do I need to arrange something in advance?
You don’t need to arrange anything in advance. Make sure to download “nRF Connect for Mobile” from Google Play store, since there are more apps with nRF in their app name.
Guys does anyone know how to set up a custom Android popup? I’m curious on how it’s supposed to work. I have a private account on Google with all my data, I won’t do shit.
how to send custom messages i tried to convert a image to hex but not possible
Hi first of all, thanks for this article ! Inspired by your Guide i created an Android App to play around with that stuff. Currently it supports the Google Fast Pairing (Android Nearby) Popups by just clicking one Button in the App. I plan to take a look at iOs and Windows Spoofing next. Maybe some people are interested in it:
https://github.com/simondankelmann/Bluetooth-LE-Spam
Thanks for sharing and creating the app! I already tested it and it works really well. Great job. I guess the next thing is to update it with the Kitchen Sink 🙂
Yes Kitchen Sink is one thing on my mind. also the iOS spam
Thanks for your tweet 🙂
Hi, i added iOs spamming and Kitchen Sink today 🙂
https://github.com/simondankelmann/Bluetooth-LE-Spam
Hey can you teach how to do Custom Messages Via Nrf Connect App?
Hey checkout I have a code which works with esp32 and displays Pixel Buds
https://github.com/MaazSk/AppleJuiceEsp32
Hi! Great project, I haven’t seen anyone porting Fast Pairing into esp32 yet. By any chance, do you also have a .ino sketch since it is more convenient? Thanks
This is a great post! I have been using Flipper Zero to spam Bluetooth pairing messages on my Android smartphone and it works great!
Can you teach how to do Custom Messages Via Nrf Connect App?
When can we expect BLE airtag spammers, that will trigger those “an airtag is following you” messages?
Hello! Can this be used effectively to annoy people who listen to shitty music on the beach, expecially through bluetooth audio speakers?