![]()
If you are interested in Wi-Fi hacking using NetHunter, you need to have a supported Wi-Fi adapter by your system that can supports various wireless modes and features. In this blogpost, we will explain what the different types of Wi-Fi adapters are, how to check their compatibility and support, and what are the different Wi-Fi modes that can be used for penetration testing.
Wi-fi modes
As a starter, it is necessary to explain that Wi-Fi adapters can support several different modes, which are used for different purposes in wireless penetration testing. Here are a few of the most common modes and their purposes:
- Client mode: It is also known as managed or station mode. This mode allows the adapter to function as a wireless client, which can be used to connect to a wireless network and perform reconnaissance and other types of attacks.
- Monitor mode: This mode allows the adapter to listen to all wireless network traffic within range, regardless of whether the adapter is connected to a network or not. It is used to capture wireless network traffic and analyze it further.
- Injection mode: This mode allows the adapter to inject wireless network packets, which can be used to perform various types of wireless attacks, such as deauthentication attacks, which can be used to disconnect devices from a wireless network.
- Access point mode: This mode allows the adapter to function as a wireless access point, which can be used to create a rogue access point and perform man-in-the-middle attacks.
- Ad-hoc mode: This mode allows two or more wireless devices to connect directly to each other without the need for a wireless access point. It is used to set up a peer-to-peer wireless network, which can be useful for penetration testing in scenarios where a wireless access point is not present.
If you want to perform wireless attacks, you need to have a OTG adapter and external Wi-Fi adapter that supports above mentioned modes, since not every Wi-Fi chipset can switch to monitor mode or is capable of injecting packets. Besides the hardware, we need a rooted Android smartphone flashed with custom NetHunter kernel, that includes drivers support for external wireless adapters, and NetHunter itself. In further section, we will explain how to enable these necessary modes.
Internal vs external adapters
In some cases, enabling monitor mode and packet injection is possible even on internal Wi-Fi adapter for devices such as Nexus 5 or OnePlus 7. Other devices might support it natively, but after flashing custom supported drivers it might work as well. If your device doesn’t have support for internal wireless adapter, you need an external Wi-Fi adapter. To make sure adapter will work correctly, it is necessary to root your device and install custom kernel that includes these Wi-Fi drivers. Lucky for us, NetHunter kernel images supports by default the most popular adapters. Additionally, if your adapter is still not recognized correctly by the system, you can install Wireless Firmware for Nethunter available as module in Magisk that support various chipsets.
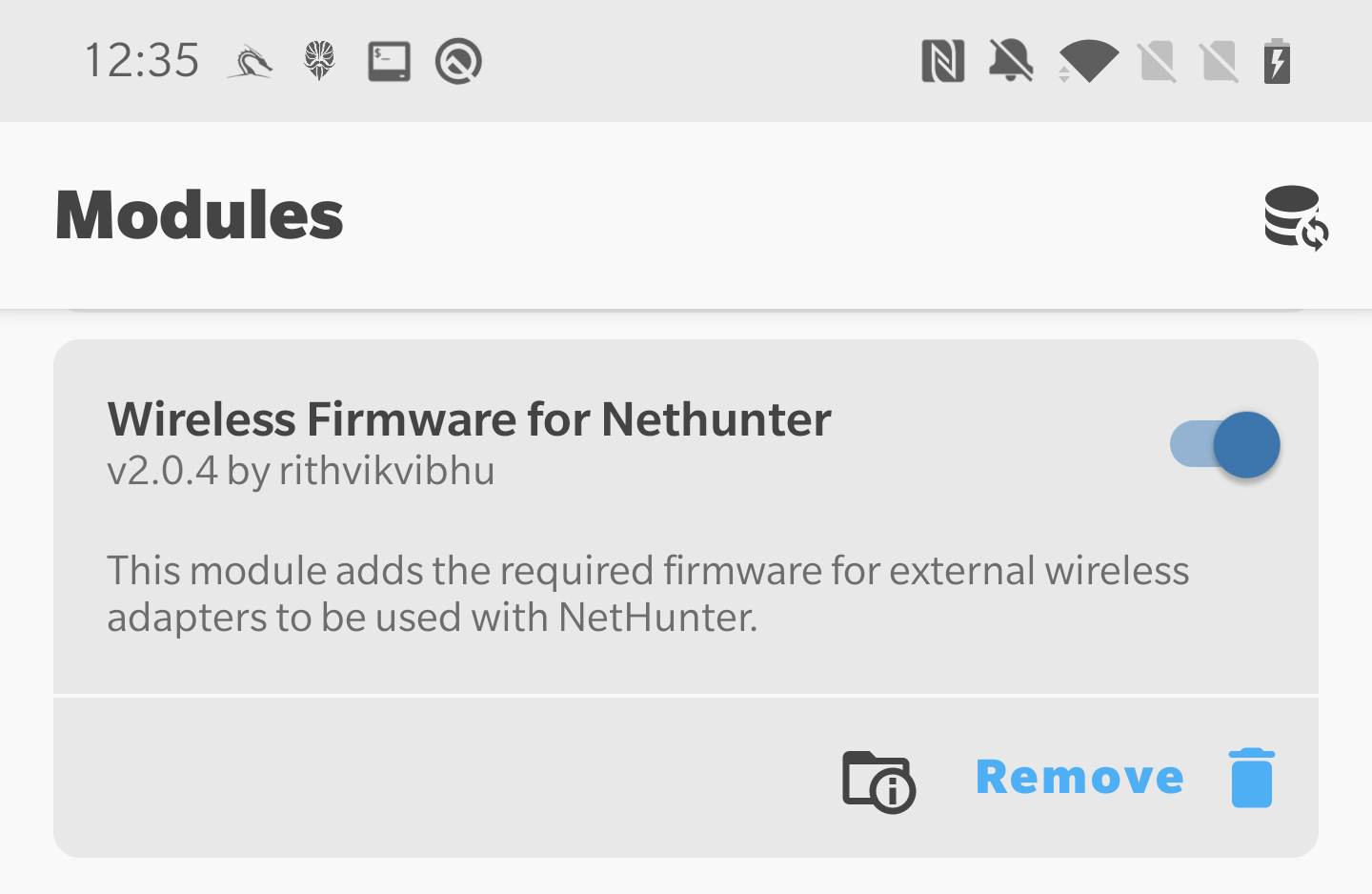
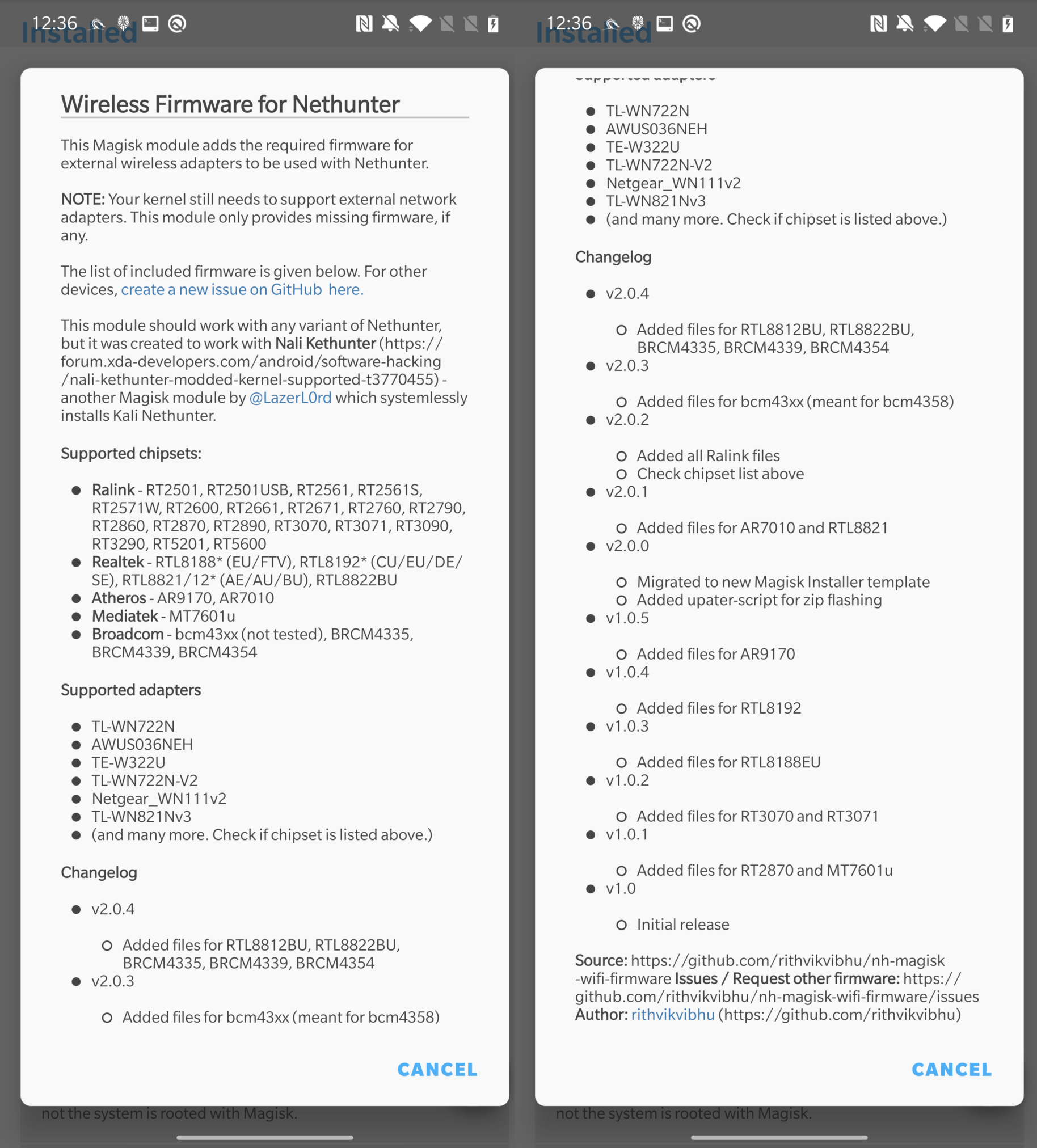
If your chipset is not in the list, then I am afraid you must either buy supported one or find, compile and install firmware manually.
How to identify external Wi-Fi adapter chipset
If you already have a Wi-Fi adapter at home and you don’t know its chipset name and support for Wi-Fi hacking, this section should guide you to identify as much as possible about your external device. Connect your Wi-Fi adapter using OTG to your device. Open terminal app such as NetHunter Terminal or Termux and use command lsusb to display the information about USB connected devices.
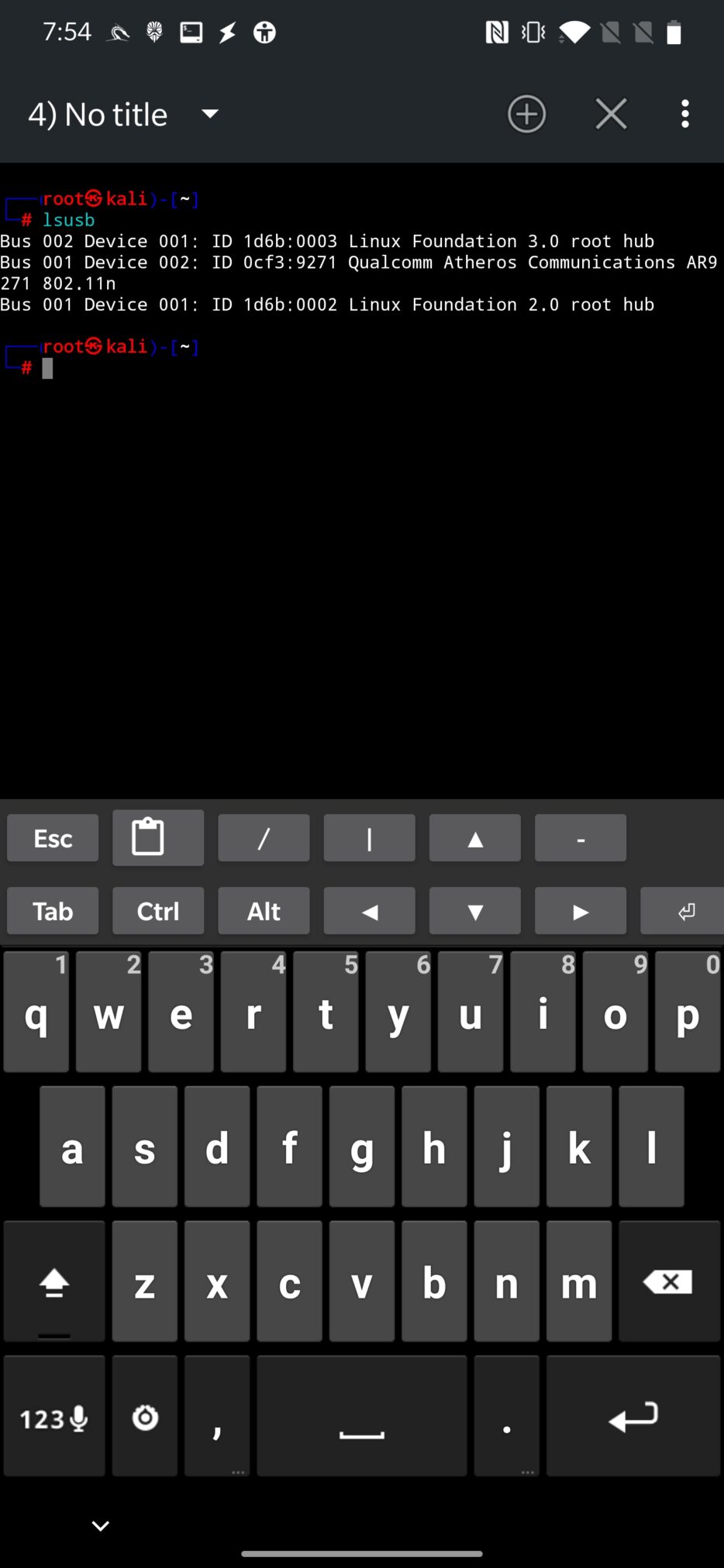
From the screenshot above, you can see that lsusb command returns name and chipset of connected Wi-Fi adapter. For detailed information that includes description, additional vv argument can be used, as you can see in Figure 4.
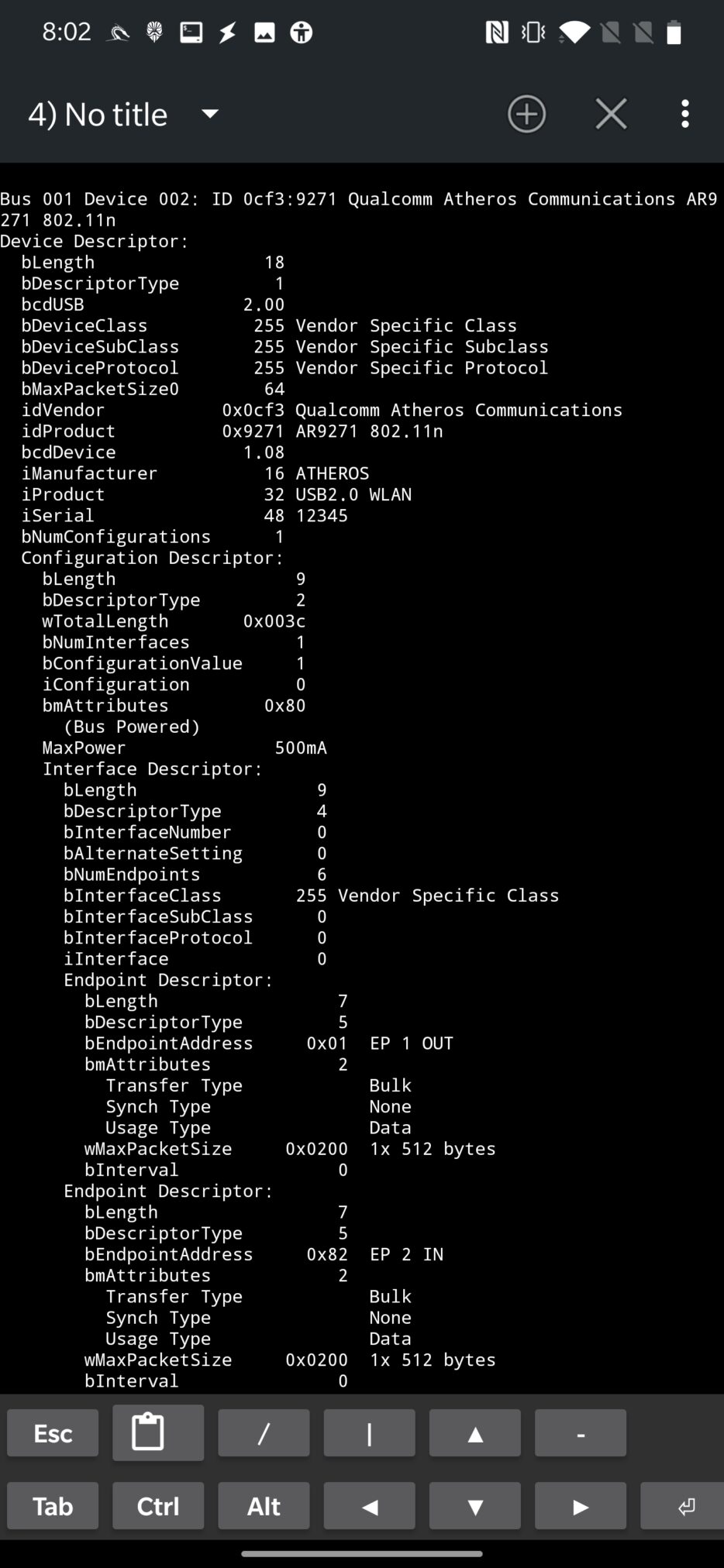
As an alternative, you can use airmon-ng to retrieve chipset, driver name and interface that is provided for it as can be seen in Figure 5.
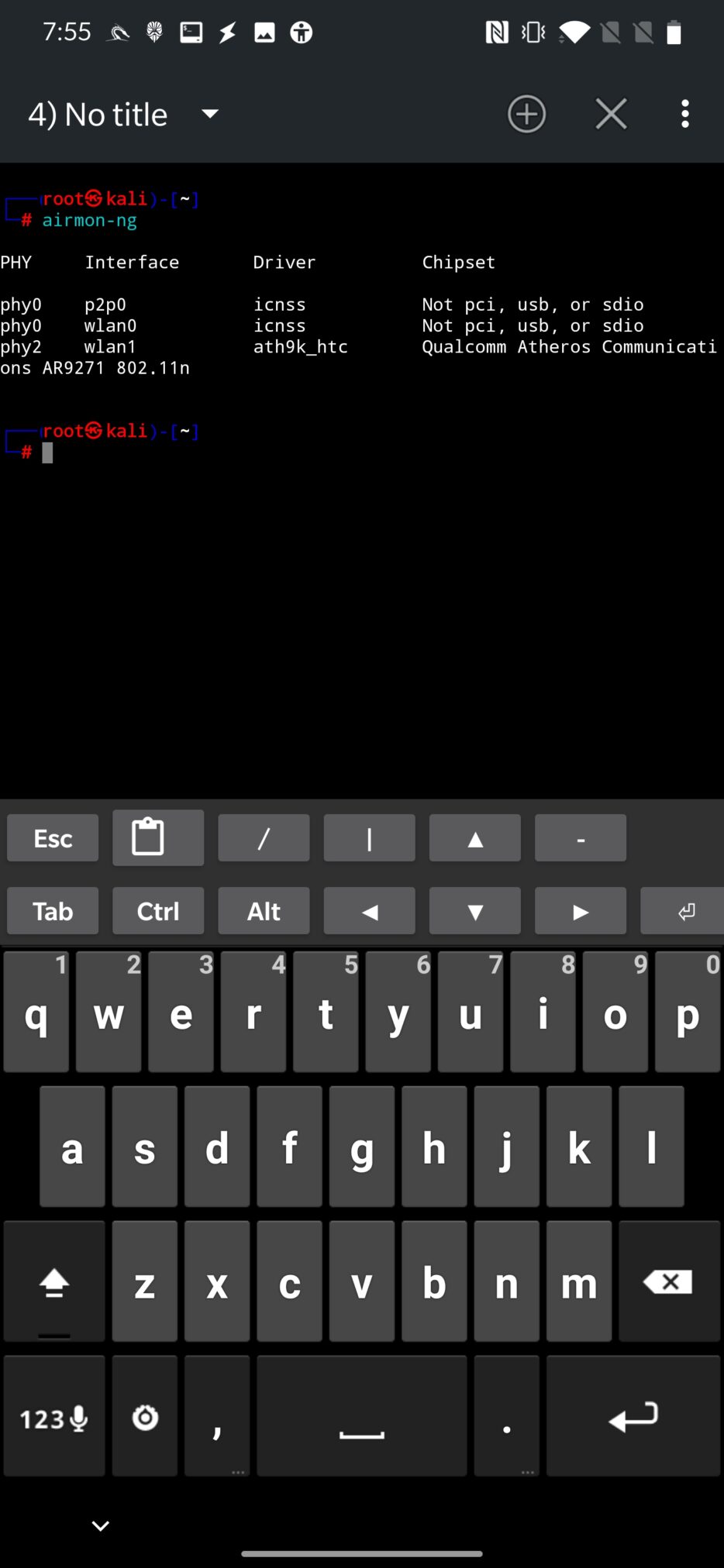
When we know our hardware, we need to find out if it supports monitor mode, wireless packet injection and access point mode.
Identify if your adapter supports packet injection, monitor and access point mode
This might be an important step before purchasing a Wi-Fi adapter to find out if it supports all necessary modes. A comprehensive list of wireless adapters that support monitor mode and packet injection that should be compatible with Kali Linux can be found at deviviki.
Additionally, all supported modes of your adapter can be verified using command iw list.
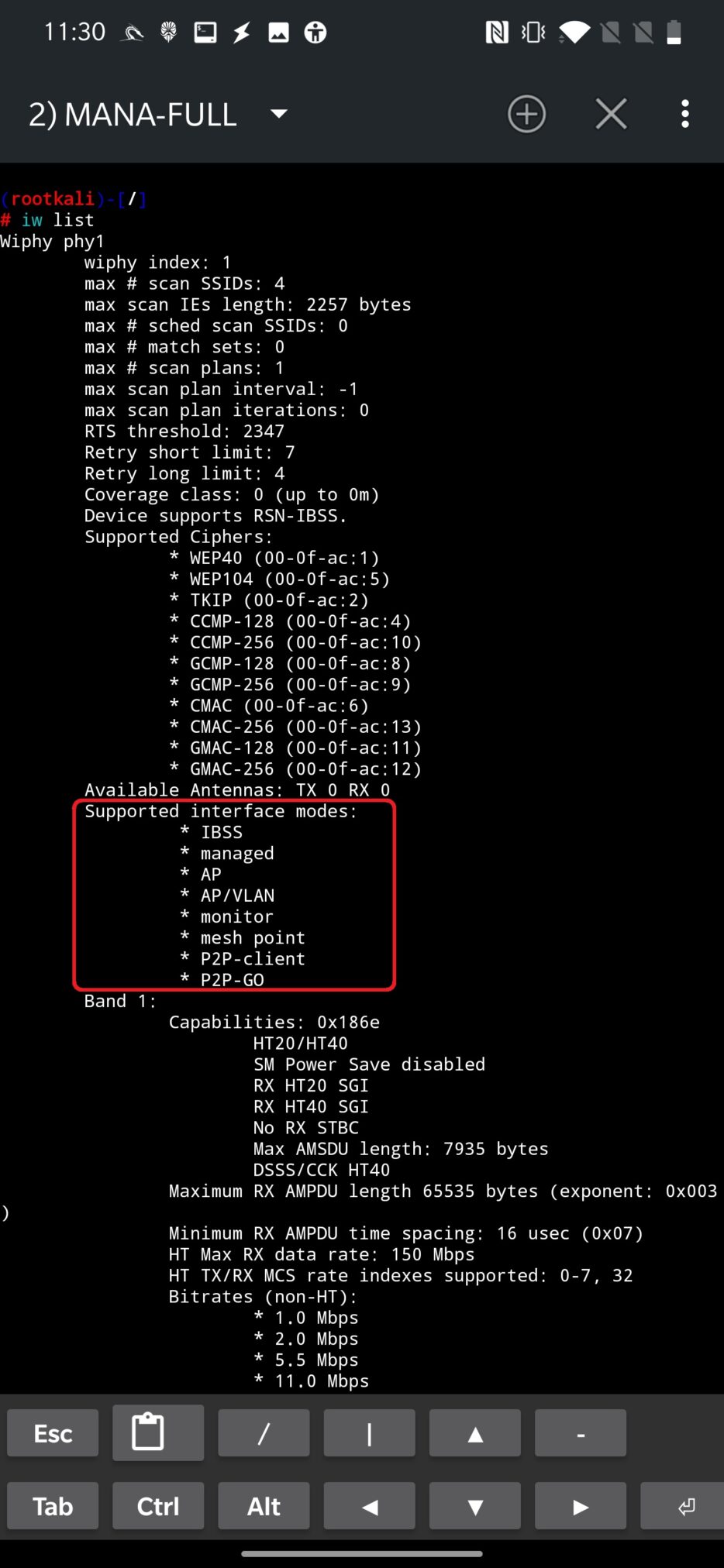
From the output above, what is important for us, we can state that it supports creating an access point (* AP) and monitor mode (* monitor).
For further details about supported interface modes, see mode documentation of iw command.
The output also contains information about valid interface combinations as you can see in the Figure 7.
From the screenshot bellow, my adapter supports only one interface combinations. Number of combinations is based on the lines starting with “*”.
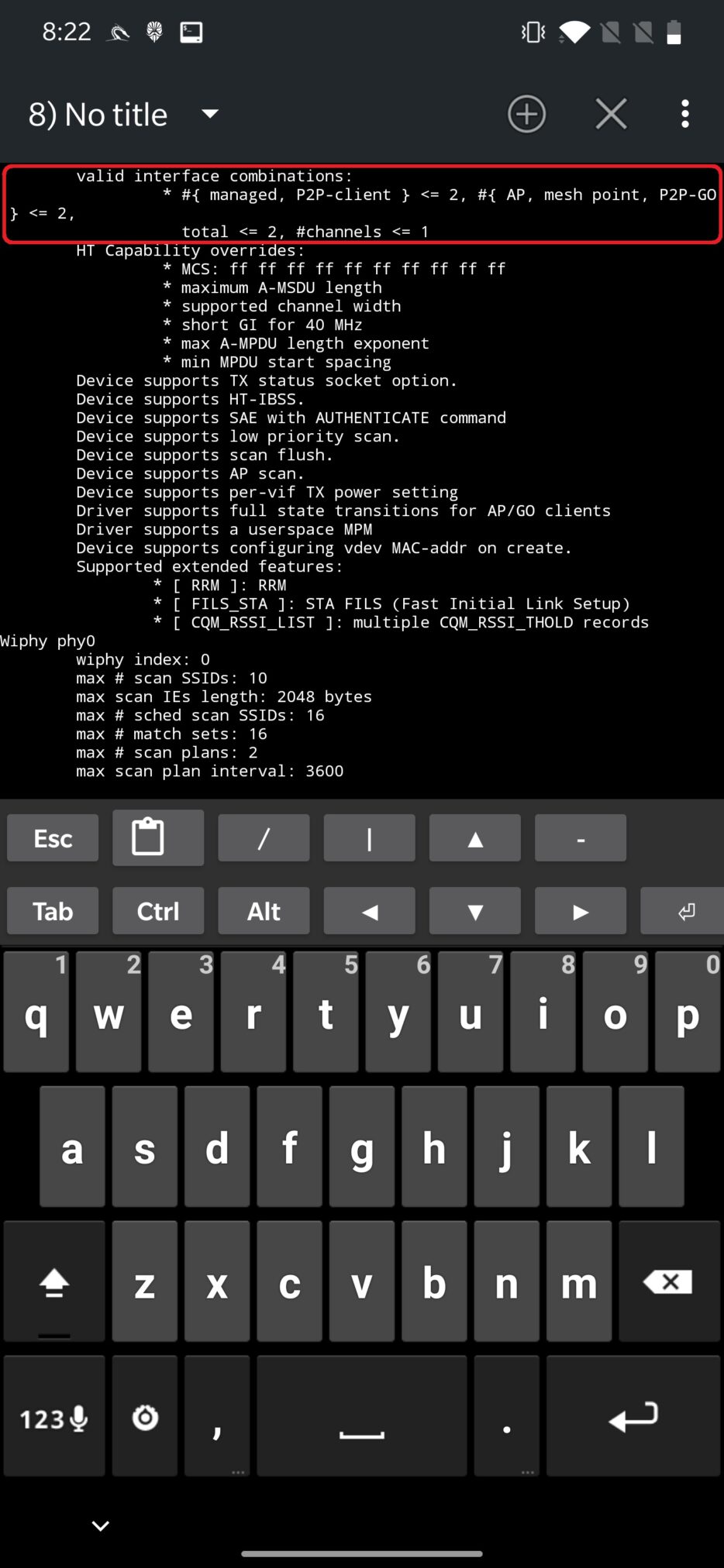
Explaining the above output, the adapter can have up to two network interfaces in managed, P2P-client mode, up to two interfaces in AP (access point), mesh point, P2P-go and their total number can’t be more than two, where they must be on one channel.
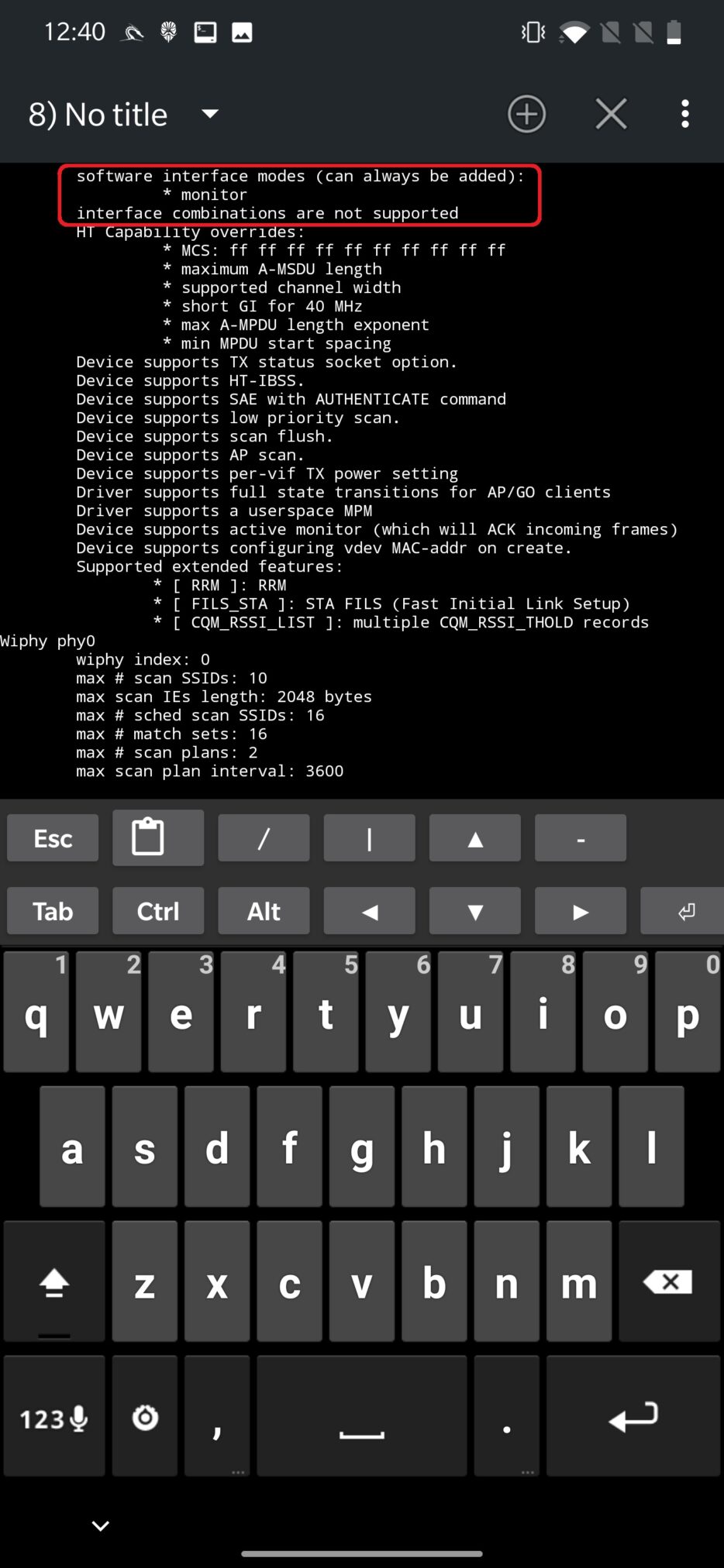
In worse case, your adapter supports monitor mode (software interface modes) but doesn’t support interface combinations as you can see in Figure 8.
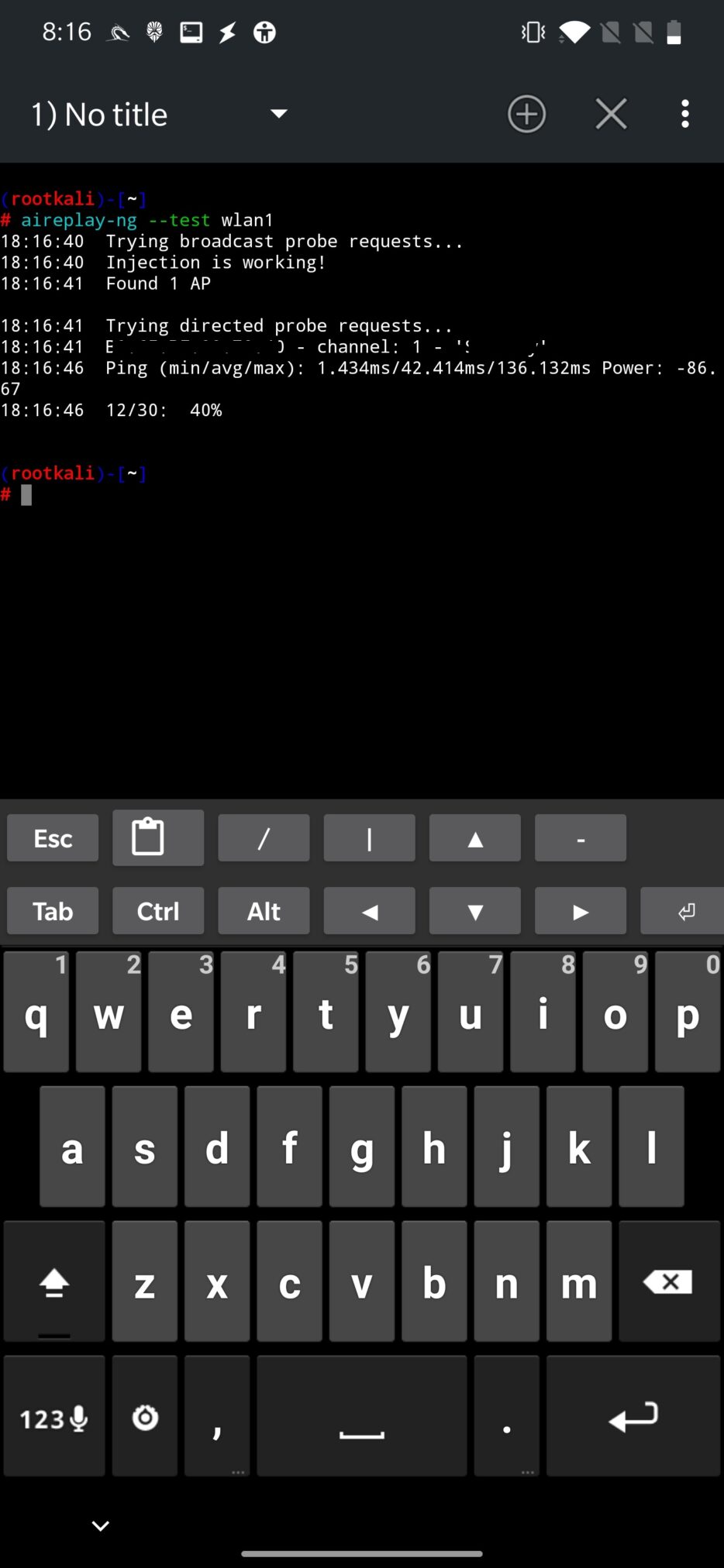
Using aireplay-ng toolkit we can test our wireless adapter if it supports packet injection, precisely using aireplay-ng –test wlan1 command, where wlan1 is our wireless external interface. Successful output from the command can be seen in Figure 9.
Enable monitor mode
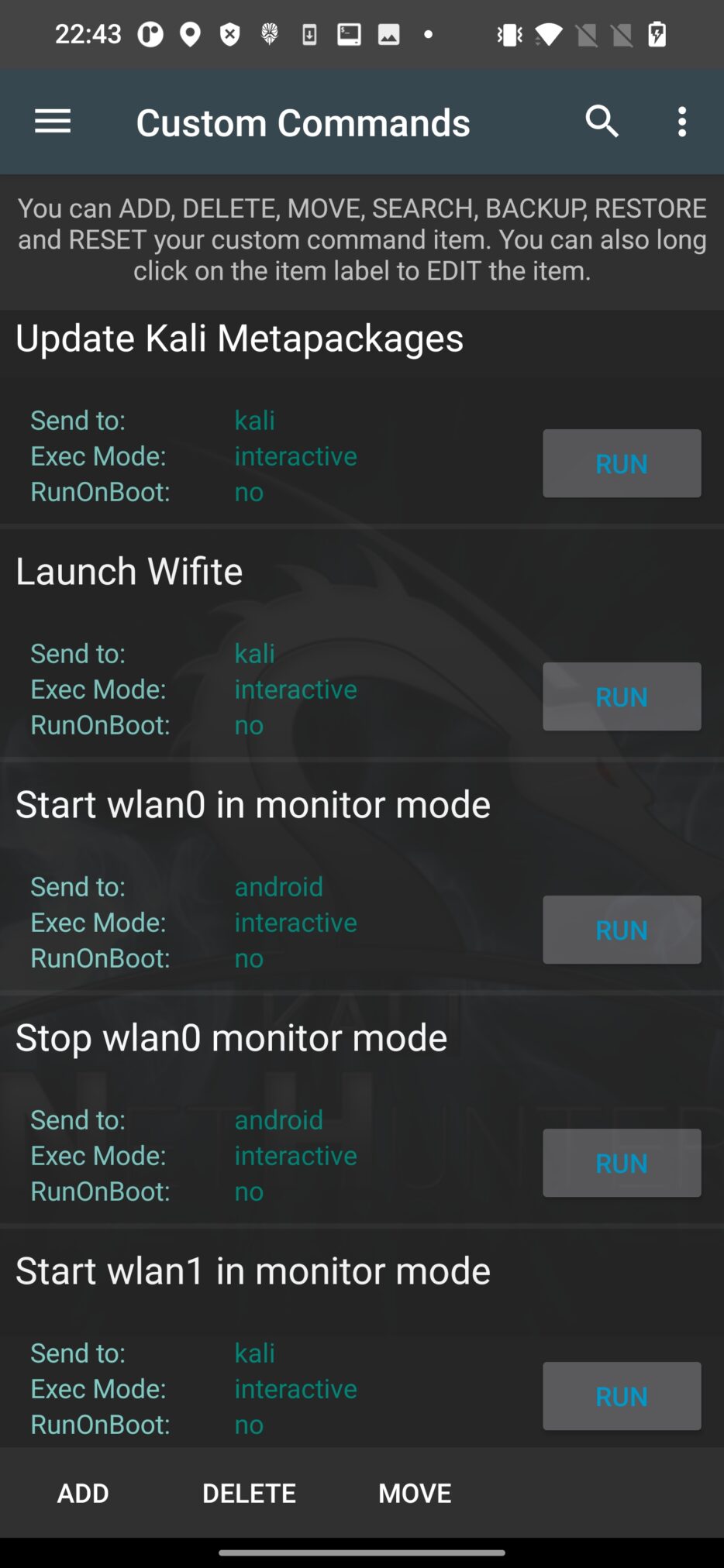
You can start and stop monitor mode for your external (wlan1) or internal (wlan0) Wi-Fi adapter directly from Custom Commands menu in NetHunter as you can see on Figure 10.
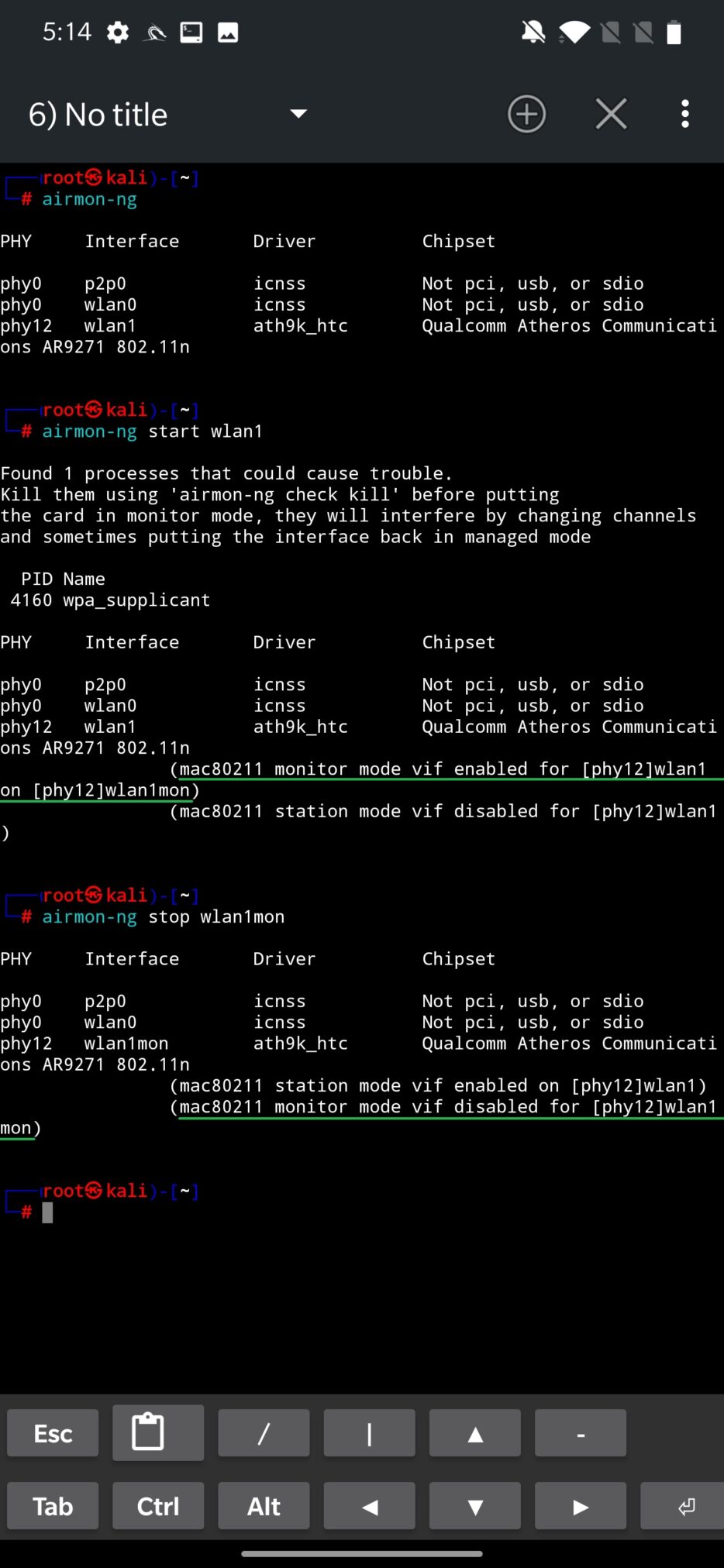
Alternative, you can perform the same task using NetHunter Terminal. To start monitoring mode on wlan1 interface, you can use command airmon-ng start wlan1. To stop monitoring mode and return adapter back to client mode use airmon-ng stop wlan1mon. Make sure to disable the same interface that is in monitoring mode as you can see in Figure 11.
For some tools, you don’t have to worry about starting monitor mode, the tools will take care of it itself, such as wifite, however this topic will be discussed in another blog.
Which Wi-Fi adapter to buy?
Buying adapter that supports all the modes will save you lot of nerves.
To be more specific and even visual, here are two lists of USB wireless adapters, their photos, chipset names, monitor and injection support, specifications and for some even max TX power that can be set. Based on the chipset name, you can find and buy them from your local shop or online from Amazon, AliExpress, eBay etc.
List of usb wireless adapters (monitor mode)
USB Wi-Fi Adapters with monitor mode and wireless injection (100% compatible with Kali Linux) 2022
When choosing between adapters, I advise to pick the one based on their chipsets and their support by NetHunter kernel. Official Kali documentation provides a list of supported adapters with default NetHunter kernel support.
Conclusion
We went through initial setup of Android device before starting with Wi-Fi hacking. To recap, your device needs to be rooted and ideally flashed with NetHunter with kernel support for supported wireless chipsets.
If your device is ready, you need OTG adapter to connect your wi-fi dongle to your smartphone. If you have some adapters at home already, you can simply detect what chipset they are running and their support for monitoring mode, capability to create access point and option to inject wireless packets.
If your current adapter doesn’t support these modes, I provided two links that will help you to find and buy your future wireless adapter.
Make sure not to miss next weeks post, we will taste the wireless waters by playing around with wifite, testing deauthentication and understanding wardrive.


Hello mobile-hacker 👋
I want to buy a oneplus 7 pro but i don’t know if it has internal injection/monitor mode because i wanne try deauth attacks…
Please write a blog about how to convert rubber ducky scripts to nethunter hid attack scripts
In this publication it indicates that the oneplus 7 has support for monitor mode with the internal Wi-Fi card, could you teach us how to configure or activate it? I have the oneplus 7 pro and I can’t activate it