![]()
This is a third time I have seen FBI posting warnings on X about risks of using free public charging stations in airports, hotels, or shopping centers ([1], [2], [3]). Unfortunately, they haven’t provided any evidence, victim reports or specific scenario that occurred and would help to identify specific attackers’ tactics. They summarized that threat actors found a way to compromise such stations and plant a malware to charging devices. In this post I will briefly introduce juice jacking attack, demonstrate how it works and share with you prevention tips.
What is juice jacking
Juice jacking occurs when an attacker compromises a public charging station or a seemingly harmless USB port to install malware on your device and exfiltrate sensitive data. Here’s how it works:
- The Trap: You’re at an airport, café, or any public place, and your phone battery is running low. Desperate for a charge, you plug your device into a conveniently available USB port. Little do you know that this seemingly harmless act could lead to trouble.
- The Attack: The attacker has tampered with the charging station or USB port. As soon as you connect your device, it becomes vulnerable. The same cable that’s charging your phone can also transfer malicious software or steal your personal information.
- The Consequences: Once compromised, your device could be infected with malware that can allow an attacker to remotely control device and steal your files.
How it works
You can simply imagine it as a charging cable that you plug in your smartphone but can’t see the other end because it is behind the wall. Problem is that you don’t know if there is something connected on the other end or not. To my knowledge, there are three possible scenarios of how juice jacking attack can be performed – screen mirroring, Human Interface Device (HID) attack, and USB debugging. Let’s briefly go through each one of them.
Screen mirroring
The example of what is seems like iPhone screen mirroring via lightning cable is shown the video below.
To mirror the screen of connected device it is necessary to have a lightning or USB-C to HDMI cable. If such cable supports OTG, then it is possible to connect additional peripherals such as mouse or keyboard to interact with mirrored screen. It is important to mention that not all devices support screen mirroring using USB cable.
HID attack
If smartphone doesn’t support mirroring through cable, then juice jacking can be done without seeing the smartphone screen. Because of that, it is not possible to see the device response to clicks. To do the trick without the seeing screen, the attacker can use OTG charging cable plugged in smartphone that behaves as Human Interface Device (HID). Such cable can emulate a keyboard or mouse to make device input. You can think of it as a physical keyboard connected to a smartphone. Once connected, it doesn’t request any approvals, you can immediately type text and interact with it. There are some devices that could behave as HID such as Flipper Zero, Rubber Ducky USB, OMG cable, Digispark, Raspberry Pi, smartwatches, or customized Android smartphone. If you would like to know more about this topic, feel free to check Ultimate guide to HID attacks using Rubber Ducky scripts and Bad USB MITM attack blog.
USB debugging
This applies only to Android devices. There is a change that juice jacking can be performed via ADB commands, but it’s very improbable. This attack requires prerequisites such as manually enable Developers settings and explicitly allow USB debugging in device menu. After cable is plugged in to device, user needs to manually allow authorization of another connected device such as computer, see Figure 1.
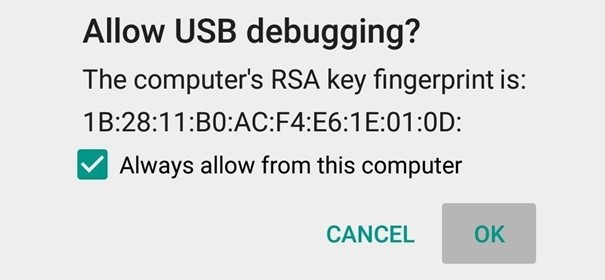
Once device is authorized, it can execute ADB commands that would allow it to interact with device, install and launch malware.
In my opinion, this scenario is unlikely, however, enabling Developers settings and enabling ADB debugging before sending ADB commands could be done using previously mentioned HID attack.
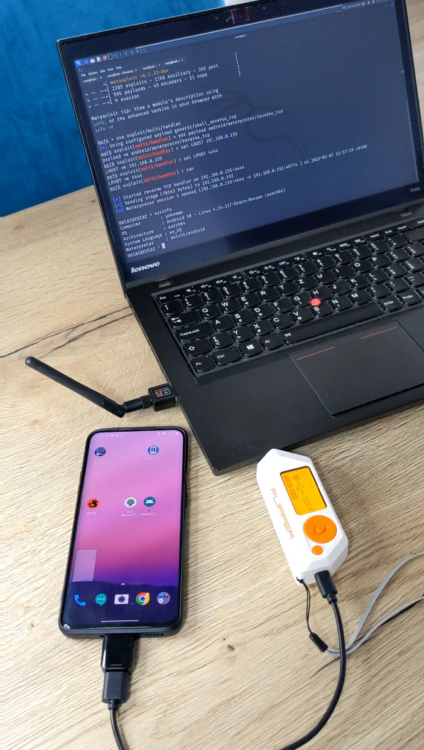
Juice jacking demonstration
In the demo below I have used a Flipper Zero connected to Android smartphone using charging cable with OTG adapter. Instead of OTG adapter can be used OTG cable so a user might not seem it as suspicious. After connecting cable to smartphone, I executed custom Bad USB script using Flipper Zero. This script downloaded Metasploit payload, installed and launched it without any user interaction within a few seconds. On the laptop in the background, I received an open meterpreter which indicates remote access to compromised Android device.
My device didn’t have enabled any lock screen protection. Because of that, I was able to interact with it. If the device would have a PIN, pattern or password protection, then we would first need to know it and unlock the smartphone to control it. This technique can’t bypass lock screen protection.
Prevention
To prevent juice jacking attacks, I would advise users to:
- Charge smartphone using your own cable and adapter when possible.
- Use device lock screen protection.
- Disable OTG support and USB debugging in if not needed and device supports it.
- Use mobile security software that might detect malware being automatically installed.
- Don’t leave device unattended.
- Use USB data blocker adapter while charging.
Conclusion
To conclude, this scenario is possible but with standard user security habits, such as having lock screen security enabled and using own cables, it is easily avoidable.