![]()
Welcome to the exciting world of NetHunter! In this blog post, we will dive into the powerful toolkit designed specifically for mobile penetration testing and ethical hacking. Kali NetHunter brings the full arsenal of Kali Linux tools to your mobile device, allowing you to assess and secure networks on the go.
Whether you are a security professional, an enthusiast, or simply curious about the capabilities of mobile hacking, Kali NetHunter opens up plenty of possibilities. From performing network scans to exploiting vulnerabilities, NetHunter provides a comprehensive suite of tools that can be accessed right from your smartphone or tablet.
Since it wouldn’t be possible to fit all the information within one post, I decided to write a complete NetHunter Hacker blogpost series. Across this series, I will cover various aspects of Kali NetHunter, providing detailed insights, tutorials, and practical examples to help you harness its capabilities to their fullest potential.
Each blog post in this series will focus on a specific topic, delving into the complexity of Kali NetHunter and its vast array of tools. We will guide you through the installation process, share tips for customization, and demonstrate how to perform different types of network assessments and security testing on mobile devices.
As we progress through the series, you can expect to learn about advanced techniques, exploit development, wireless network assessments, and much more. We’ll equip you with the knowledge and skills to conduct thorough security assessments, identify vulnerabilities, and fortify your systems against potential threats.
To make navigation easier, each blog post in this series will have a unique name that reflects its specific focus. These names will provide a quick overview of the topics covered, making it convenient for you to find the information you need. Here is a list of 17 blogs that will be published each week on this website:
- NetHunter Hacker: Introduction to Kali NetHunter hacker series
- NetHunter Hacker I: Installation of rootless Kali NetHunter
- NetHunter Hacker II: Install Kali NetHunter on rooted OnePlus 7 Pro
- NetHunter Hacker III: How to build Kali NetHunter for OnePlus 7 Pro
- NetHunter Hacker IV: Introduction to NetHunter system
- NetHunter Hacker V: How to use MAC Changer, KeX and setup USB Arsenal
- NetHunter Hacker VI: Ultimate guide to HID attacks using Rubber Ducky scripts and Bad USB MITM attack
- NetHunter Hacker VII: Wi-Fi compatibility check and setup on Android
- NetHunter Hacker VIII: Wi-Fi hacking with wifite, deauthentication and wardriving
- NetHunter Hacker IX: Use MANA Toolkit to create Wi-Fi rogue access point and intercept traffic
- NetHunter Hacker X: WPS attacks
- NetHunter Hacker XI: Bluetooth arsenal
- NetHunter Hacker XII: Master Social Engineering using SET
- NetHunter Hacker XIII: Overall guide to MITM framework
- NetHunter Hacker XIV: Find exploits using SearchSploit and setup Wi-Fi Pineapple connector
- NetHunter Hacker XV: Use Nmap for network scanning
- NetHunter Hacker XVI: Metasploit payload generator in your pocket
Nothing of that wouldn’t be possible without great team that is behind the Kali NetHunter development and support, huge thanks belong to great Kali and NetHunter community.
Starting easy, to continue in introduction section we briefly go through basics that are necessary to understand, before we start with installation, building a kernel, testing tools, using additional hardware and continue with actual hacking.
The NetHunter system is typically installed within the internal storage of an Android device. When you install NetHunter, it sets up a chroot environment, essentially creating a separate Linux file system hierarchy within the designated directory or partition. This chroot environment contains the necessary files, libraries, and dependencies to run the Kali Linux tools.
NetHunter is not an Android ROM, where is it installed?
Chroot, also known as the root file system (rootfs), is a concept used in the context of Kali NetHunter and other Linux-based systems. It allows you to change the apparent root directory of a process to create a restricted environment with its own file system hierarchy. The chrooted environment coexists with the Android system.
In the case of Kali NetHunter, chroot or rootfs is used to provide a controlled environment for running the Kali Linux tools on an Android device. By utilizing chroot, the Kali NetHunter team has created a way to bring the power of Kali Linux to Android devices without the need for a full Linux installation.
When you launch Kali NetHunter, it sets up a chroot environment on your Android device, where a minimal Linux file system is installed. This chroot environment acts as a separate root directory, isolating the Kali Linux tools and their dependencies from the underlying Android system. The specific location of the NetHunter installation may vary, however, it is typically stored in a dedicated directory within the internal storage, such as /data/local/nhsystem.
This allows NetHunter to function effectively on device without interfering with the Android operating system. Simply put, NetHunter is installed and running on top of the Android system without changing its integrity.
Choose NetHunter based on your needs
Kali NetHunter is an open-source mobile penetration testing platform for Android devices, based on Kali Linux that also provides its own NetHunter App Store with a couple of useful apps. What is important for you, there are three different versions of NetHunter for Android devices:
- NetHunter Rootless
- NetHunter Lite
- NetHunter
NetHunter Rootless
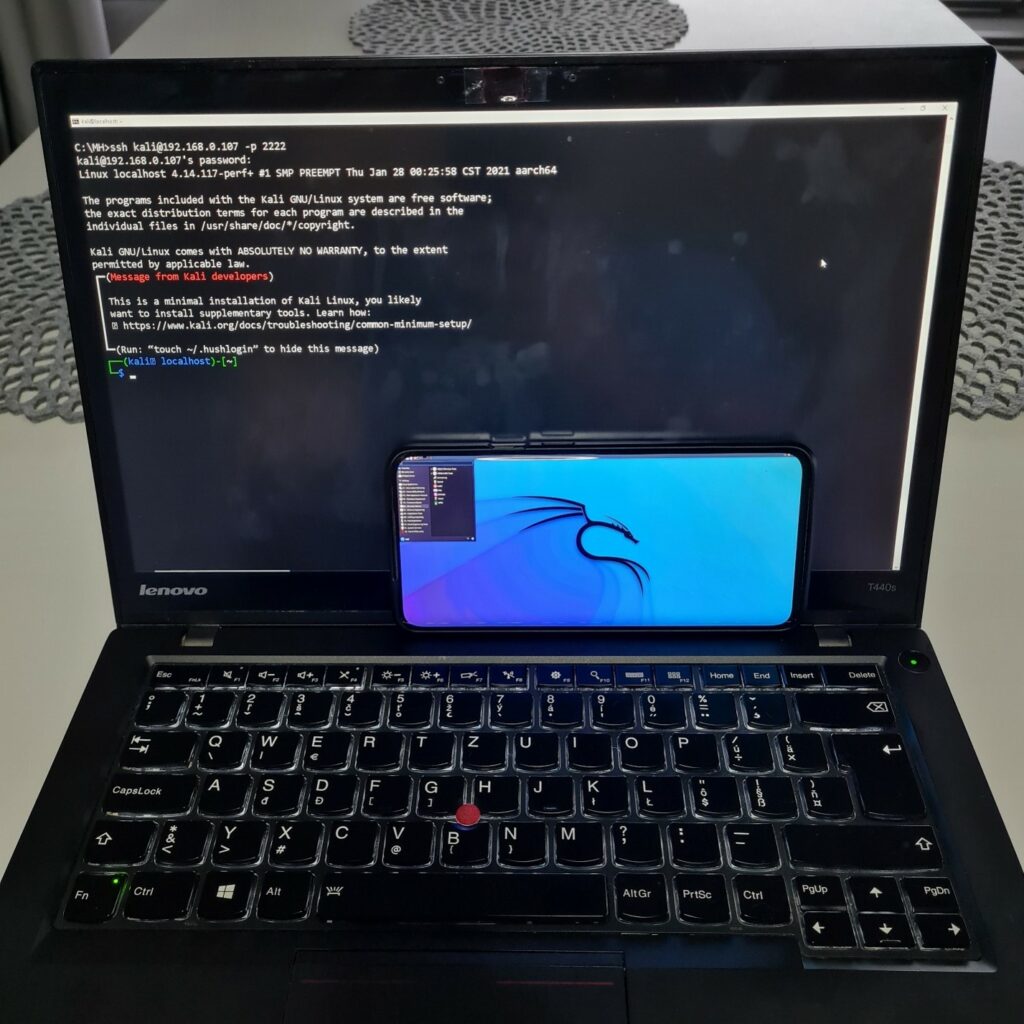
The rootless version doesn’t require a device to be rooted, which means it can be installed almost on any Android device. Installation process is easy and fast where user achieves a portable desktop version of Kali Linux running on the device in a pocket. Here are quick pros and cons that come with rootless edition that users should know about.
Pros:
- Doesn’t require rooting a device that would void device warranty
- Easy installation process
- Portable full Kali Linux environment accessible on device, also locally accessible via HDMI cable, VNC or SSH from a computer
Cons:
- Missing kernel drivers for internal and external Wi-Fi, Bluetooth, SDR, HID devices
NetHunter Lite
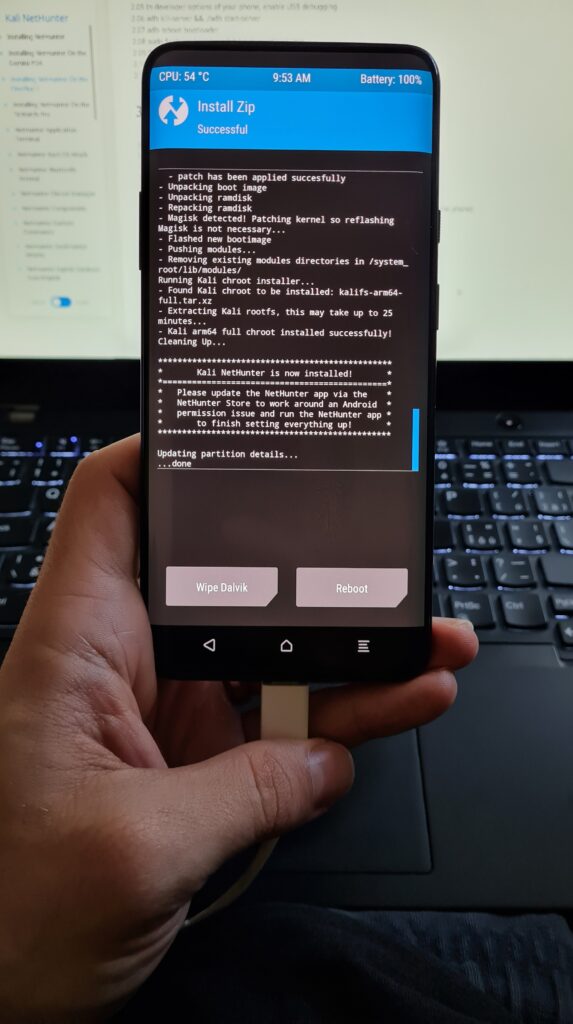
Lite version requires rooting a device and serves for users without a custom kernel. This means, that there is not an available custom kernel with all the drivers for a particular smartphone. Because of that, it might not be possible to perform some attack scenarios with stock kernel.
Pros:
- Portable full Kali Linux environment accessible on device, also locally accessible via HDMI cable, VNC or SSH from a computer
Cons:
- Require rooting device that would void device warranty
- Missing kernel drivers for internal and external Wi-fi, Bluetooth, SDR, HID devices
NetHunter
Full modular version with root access and custom kernel drivers. It supports popular external devices necessary for wireless penetration testing and recon, such as Wi-Fi, Bluetooth, HID, SDR gadgets. This is the most powerful variant of NetHunter.
So far, the NetHunter GitLab repository contains over 164 kernels for over 65 devices. However, for download are published 25 compiled images for the most popular devices. This means, that if a user has other than one of the 25 images, it is necessary to compile it by itself.
Pros:
- Portable full Kali Linux environment accessible on device, also locally accessible via HDMI cable, VNC or SSH from a computer
- Kernel support for some internal and external Wi-fi, Bluetooth, SDR, HID devices
Cons:
- Require rooting device that would void device warranty
- For some devices, users might need to compile a NetHunter image
Conclusion
The different variations of Kali NetHunter offer users flexibility and options based on their specific needs and preferences.
Rootless NetHunter provides a lightweight and portable option for users who prefer to avoid rooting their devices. With this version, you can still access a range of essential security tools and perform various network assessments without the need for full device control. It’s a convenient choice for those who want to maintain the integrity of their device’s operating system while still having access to powerful hacking capabilities. Lite NetHunter is designed for users who want a streamlined version of NetHunter with a reduced footprint. This variant offers a balance between functionality and resource usage, making it ideal for devices with limited storage or processing power. Rooted, on the other hand, offers the most comprehensive and feature-rich experience. By rooting your device, you gain full control over the operating system, allowing you to unlock advanced capabilities and access a vast range of Kali Linux tools. This version provides the most extensive functionality, giving you the power to perform in-depth security assessments, exploit vulnerabilities, and conduct advanced penetration testing.
Ultimately, the choice between Rootless, Lite, and Rooted NetHunter depends on your specific requirements and comfort level with modifying your device. Each variant offers unique advantages and trade-offs, enabling users to tailor their NetHunter experience to their individual needs.
Whether you are a security professional, a growing ethical hacker, or simply curious about the capabilities of Kali NetHunter, the NetHunter Hacker series will empower you to explore the depths of mobile security testing and enhance your understanding of cybersecurity.
So, join me on this exciting journey as we unravel the mysteries of Kali NetHunter and unlock its full potential. Stay tuned for upcoming blog posts in this series, each packed with valuable insights and practical guidance to take your mobile penetration testing skills to new level. Get ready to embark on a thrilling adventure into the world of Kali NetHunter!


I use nethunter only with root as my device doesn’t have nethunter compatible kernel. sometimes he gets discouraged, because he would like to take advantage of all the knowledge that is passed on here. but I will follow, I hope I can make the most of it anyway.
I am sure this series will help you to get most out of your Nethunter device
Pixel 4 with custom kernel….I’ve been waiting for someone to post some content on nethunter… Looking forward to all of this
There should be an subscribe button so ,we can notify by an e-mail that you posted new blog👍.
I have a oneplus 7 pro, but it cannot install the kernel for oxygen os 11 published on the official page of kali nethunter, when trying to disable dm-verity encryption I get an error, I could only install a kernel for android 10, I hope that With your help I can install a more updated version of the kernel for Android 11, thank you very much for your contribution
Poco f1 with custom kernal
waiting for your videos❤️
I am using Samsung galaxy s7edge rooted my mobile install KaliNethunter not working Hid and wifite😭😭😭😭😭
I will be glad to see the outcome of this Nethunter
So. That was a good read. But I don’t know if I missed something. Can I use my iOS device to hack a another iOS
I do believe all the ideas you’ve presented for your post. They are really convincing and will certainly work. Nonetheless, the posts are too short for novices. May just you please lengthen them a little from subsequent time? Thanks for the post.