![]()
Shizuku is an Android app that acts as a powerful bridge, allowing other applications to use system APIs with elevated privileges, all without requiring full root access. It’s basically a way to grant special permissions, like writing secure settings, through ADB (Android Debug Bridge), making a ton of awesome modifications and features accessible on your phone.
In this post, we’ll explore what Shizuku is, how it works, what it enables, and how not just cybersecurity enthusiasts – with elevated Termux privileges – can use it to improve their Android experience. I will mainly focus on running it on non-rooted Android smartphone.
What is Shizuku?
Shizuku is an Android application designed to allow other “normal” apps to use system APIs. It achieves this by starting a Java process with app_process using either ADB for non-rooted devices or root privileges for rooted devices. Its primary purposes are to offer a method for apps to use system APIs and to enable the development of applications that only require ADB permissions. In short, it means that you can execute ADB commands directly on device with escalated privileges.
How Does Shizuku Work?
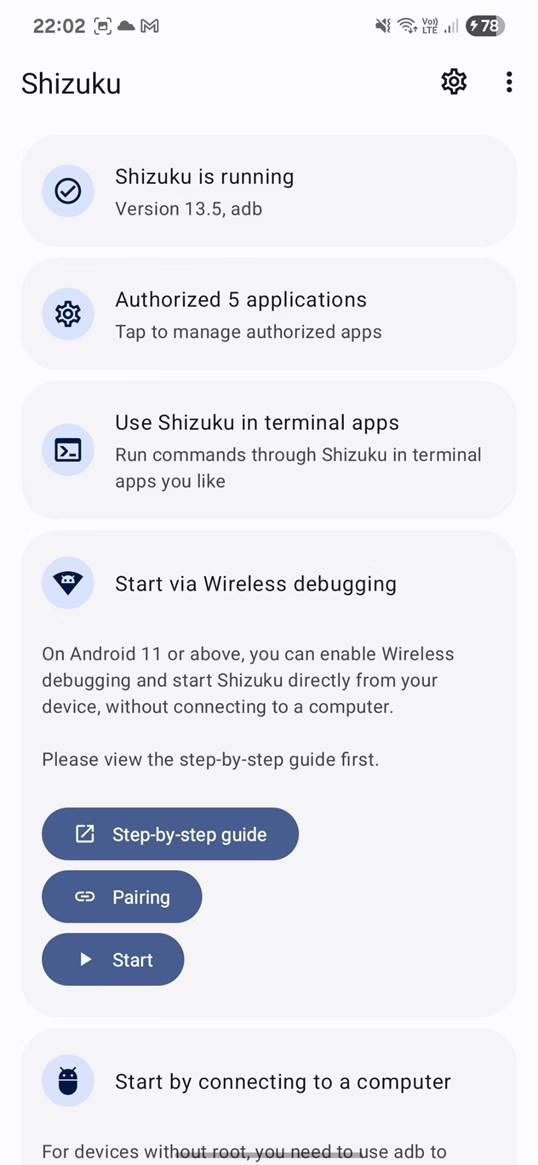
Shizuku runs a background service that apps can connect to and leverage its escalated privileges.
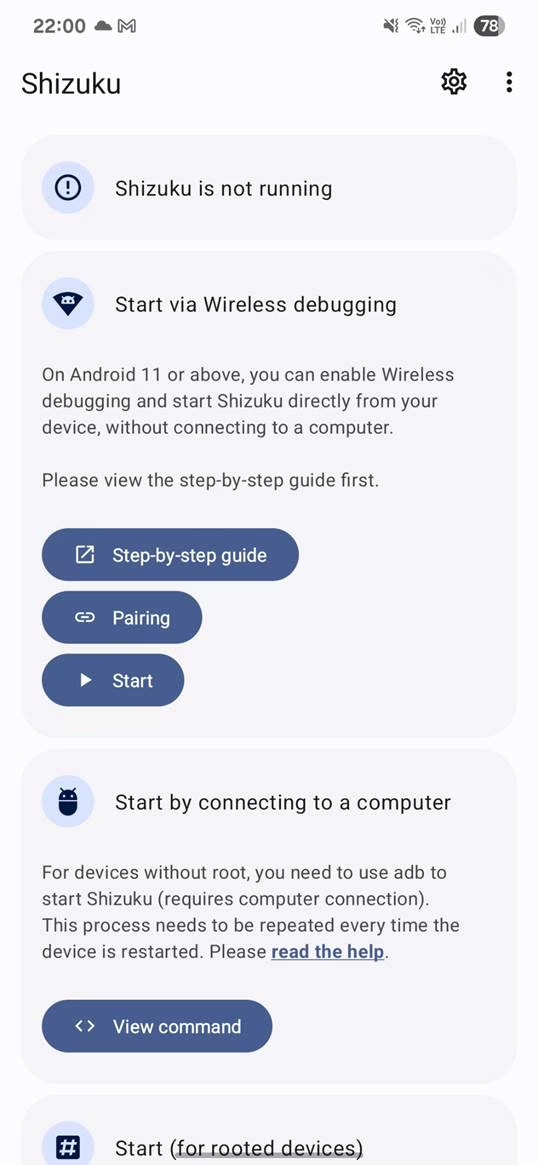
This service is started using either:
- Wireless ADB: Available on Android 11 or higher, this method is convenient as it does not require a computer. However, due to system limitations, you’ll need to re-perform the setup steps after each device reboot. This involves enabling
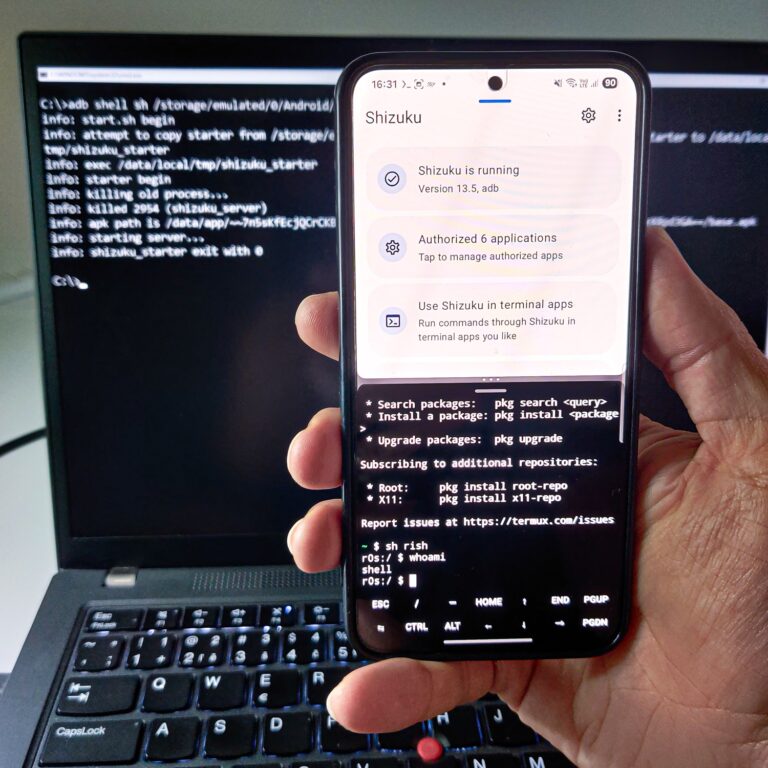
Developer optionsandWireless debuggingon your device, then pairing with a code provided by Shizuku. Full setup details you can find here. - Using PC: Temporarily grants elevated privileges until the device is rebooted. This option is for unrooted devices. It requires setting up ADB (Android Debug Bridge) on a computer, connecting your device, and executing a command by running executing Shizuku script using command:
adb shell sh /storage/emulated/0/Android/data/moe.shizuku.privileged.api/start.sh 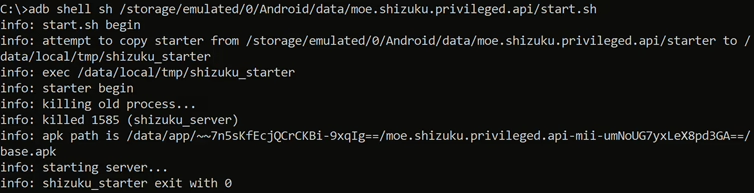
- Root (if available): For rooted devices, just start directly.
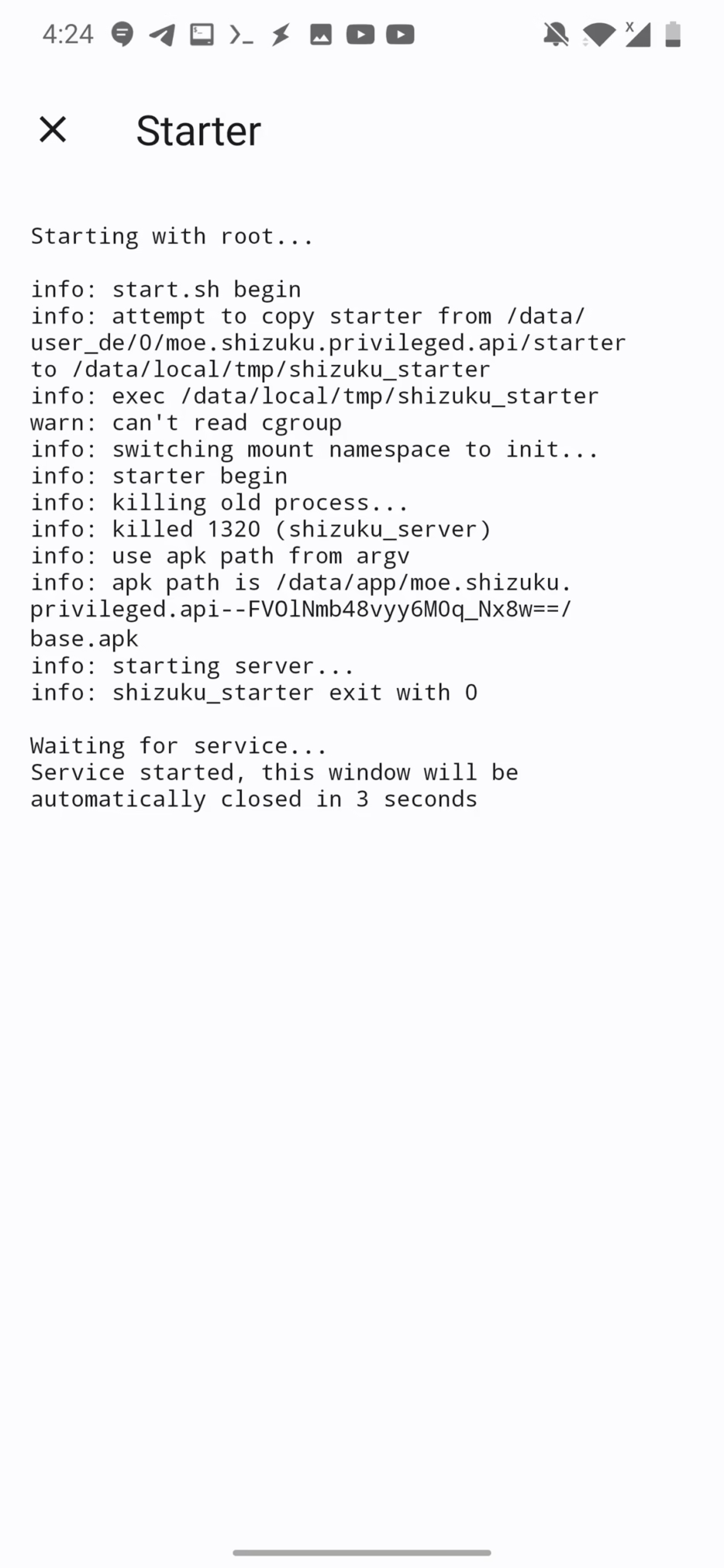
Once running, Shizuku allows apps to call privileged APIs using ADB permissions, bypassing the need for root while still maintaining a high level of control.
Popular Apps That Work with Shizuku
Several powerful apps integrate with Shizuku to unlock advanced features:
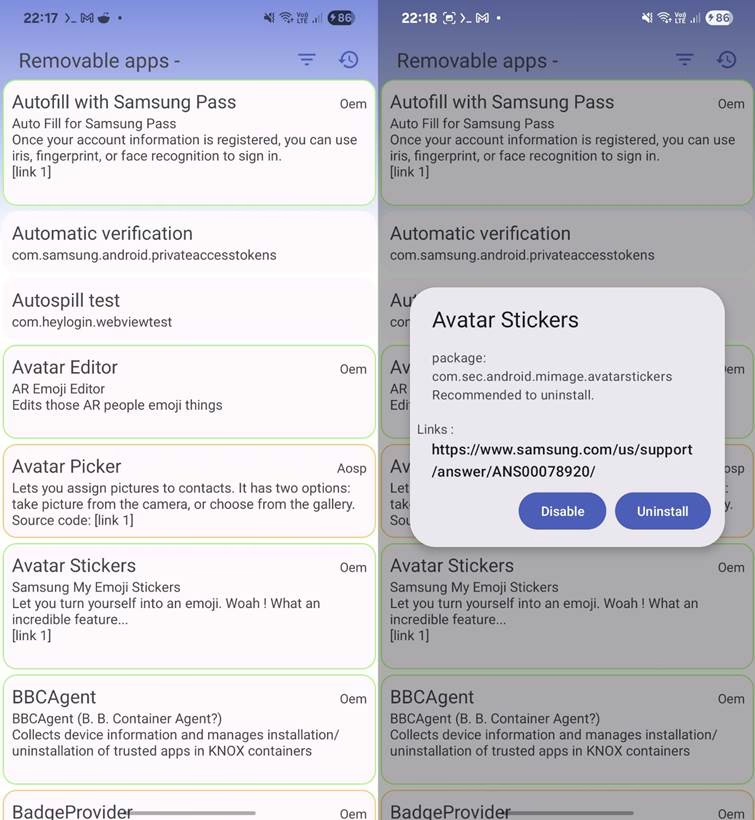
- Android Debloater (UAD): Identify and remove bloatware. It is part of ShizuTools app or you can use Canta.
- VolumeManager – Control each app’s volume independently.
- PhoneProfilesPlus – Allows automatic or one-click configuration of your device for specific life situations.
- AAAD IAP – Downloads popular Android Auto 3rd party apps and installs on Android Auto.
- AutoDark – A small Android app to let you schedule dark mode On/Off.
- TapTap – Port of the double tap on the back of the device feature from Android 12 to any Android 7.0+ device.
- Grayscaler – Keep your phone mostly monochrome, but allow apps like camera to be in color.
- shappky – A simple app to boost performance by stopping background apps.
- LSPatch – A non-root Xposed framework extending from LSPosed.
- NaiveproxyForAndroid – A simple application to run Naiveproxy on Android MIT. Unfortunately, it is not compatible with my Android 15.
- PrivateDNSAndroid – Quick settings tile to switch active private DNS server.
- Blocker – Enable/disable Android components such as activities, services, receivers, and providers.
BOOT broadcast
- File Management: Popular file managers like MiXplorer, MT Manager, Solid Explorer, Total Commander, and X-Plore can access Android’s data and obb folders.
- Termux: A terminal emulator and Linux environment for Android.
For more apps, here is a list with over 170 supported apps and 30 unlisted apps.
Setting Up Termux with Shizuku Using rish
To unlock the full potential of Termux with Shizuku, you need to use a tool called rish—a shell interface that runs commands with elevated ADB-level privileges. Rish allows you to interact with the system as if you were using ADB, all without rooting your device. When Shizuku is launched using ADB privileges, rish inherits those privileges, allowing you to run commands in a high-elevated shell environment.
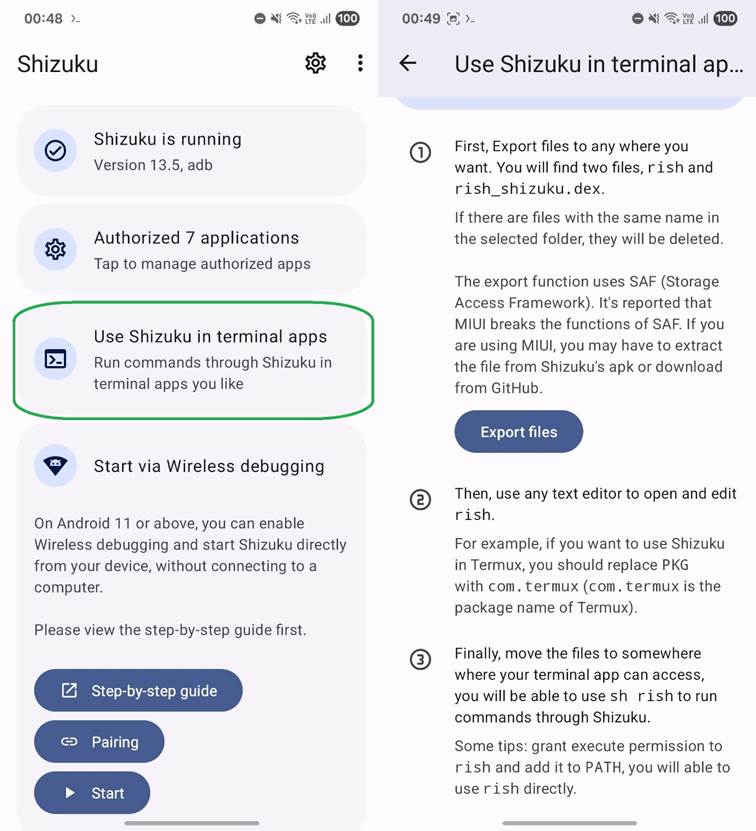
To enable Terminal Access, in Shizuku, go to Use Shizuku in terminal apps and follow the instructions to download and set up rish.
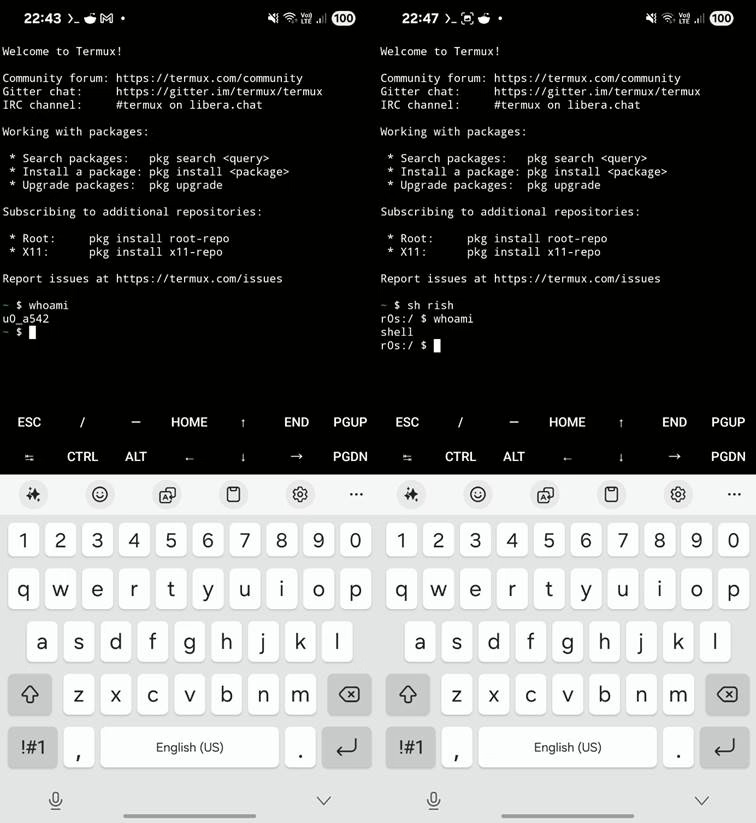
In Figure 9. is a comparison of running Termux as default user and with elevated shell privileges leveraging Shizuku.
Cybersecurity Tools & Use Cases with Shizuku
Listing Running Processes
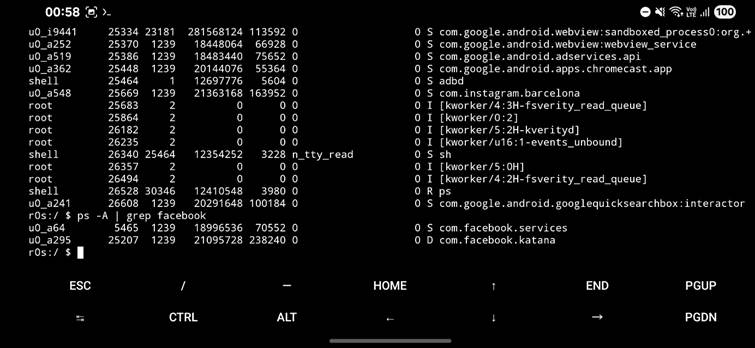
With rish, you can execute shell commands with ADB privileges. This allows you to run the ps (process status) command to list running processes on your non-rooted Android device by running commands like:
ps -AThis lists all processes and allows monitoring running apps.
Network Monitoring with Netstat
Use Termux to run:
netstat -tuln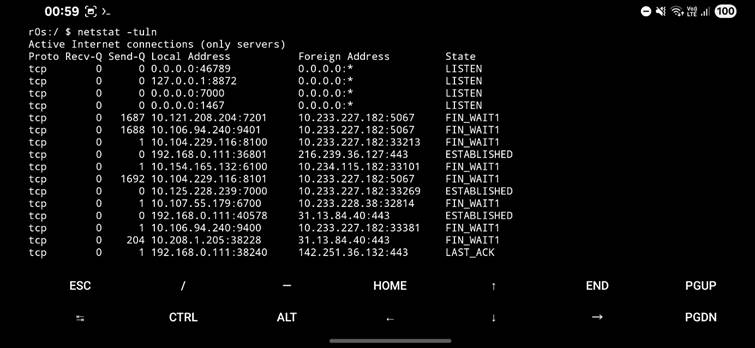
This shows open ports and listening services. On rooted devices, you can even map:
- PID (Process ID)
- Package name of the app using the port
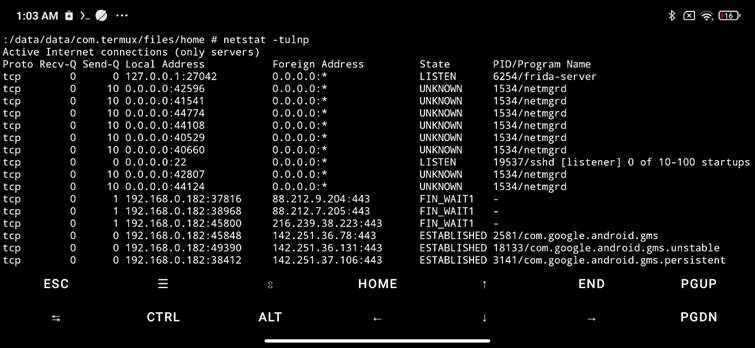
This is invaluable for identifying suspicious network activity. In the same way it is possible to identify an open port vulnerability in ES File Explorer app (CVE-2019-6447).
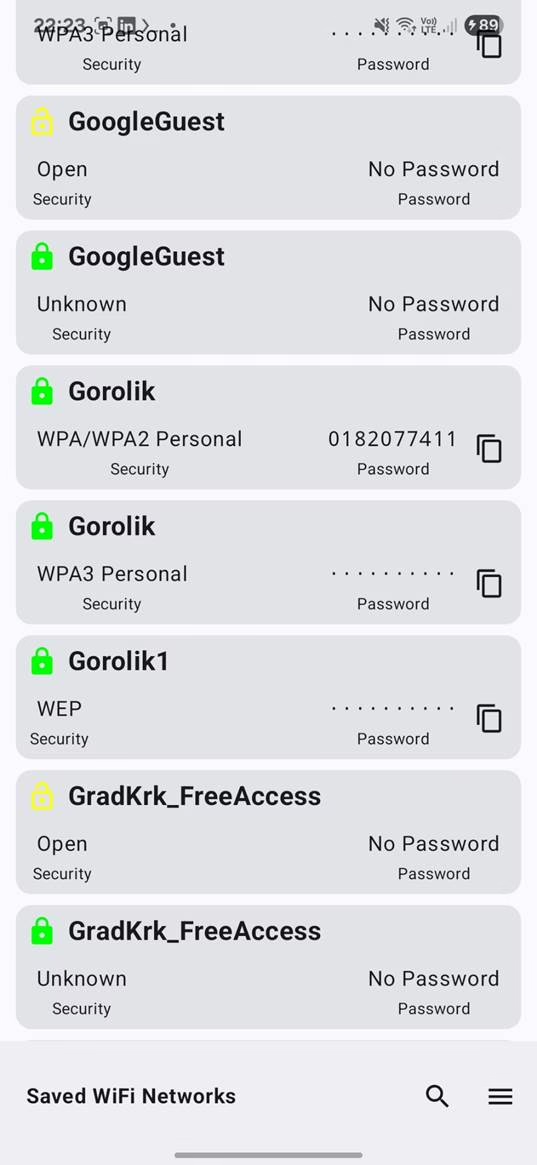
View Stored Wi-Fi Passwords
The WiFiList app, when used with Shizuku, can allow you to view your saved Wi-Fi passwords on Android 11 and later devices without needing root. This can be useful for assessing your network connections or recovering forgotten passwords.
Logcat Access
In Termux you can run:
logcat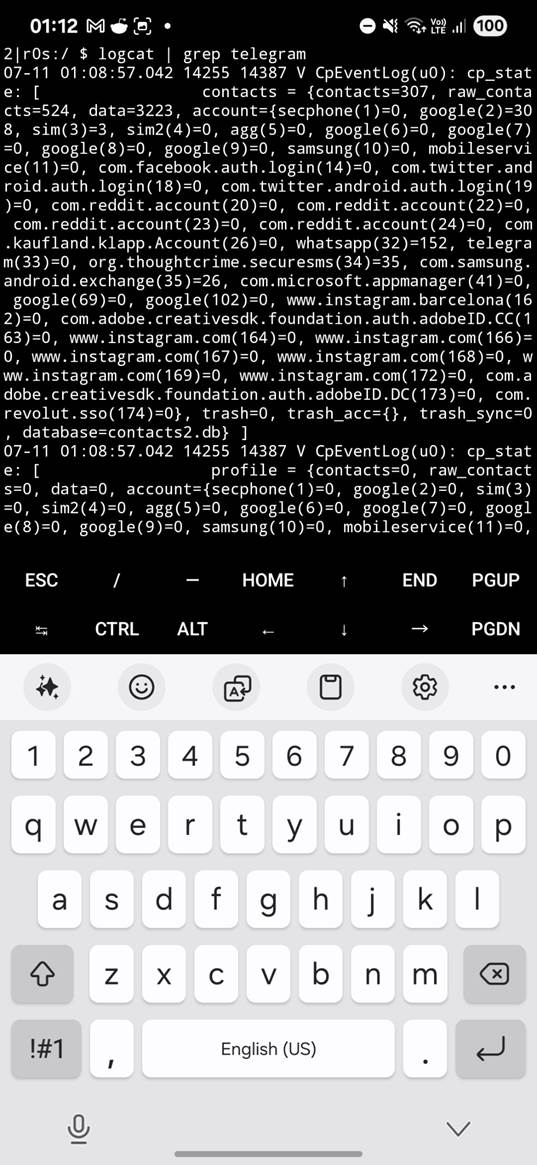
However, the output is difficult to read. For a better and clearer Logcat output I advise using LogFox app with string filtering option.
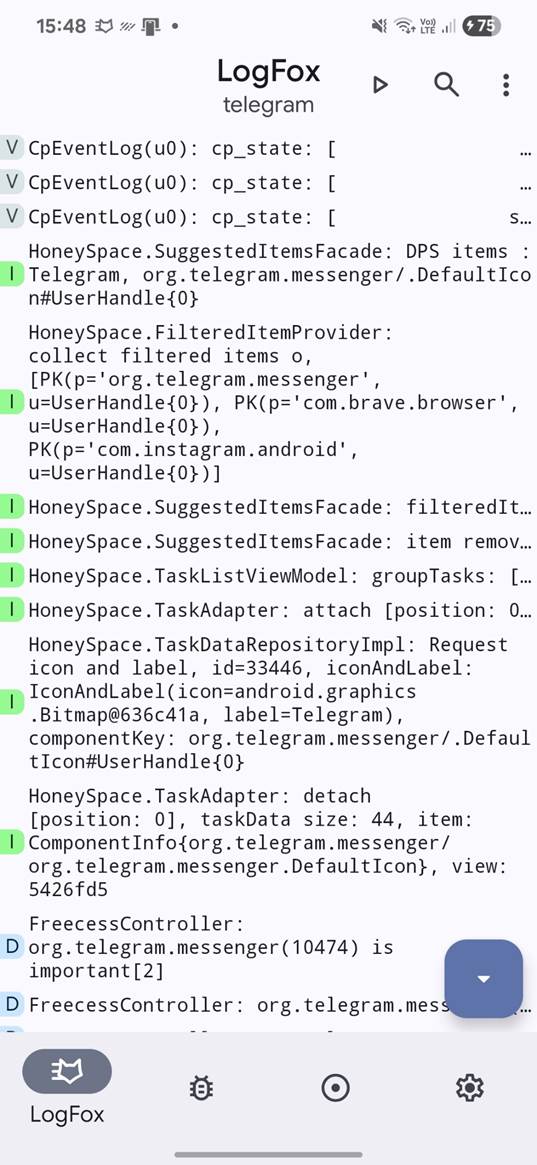
With Shizuku, you can see logs from other apps, which is useful for:
- Debugging
- Monitoring app behavior
- Detecting anomalies
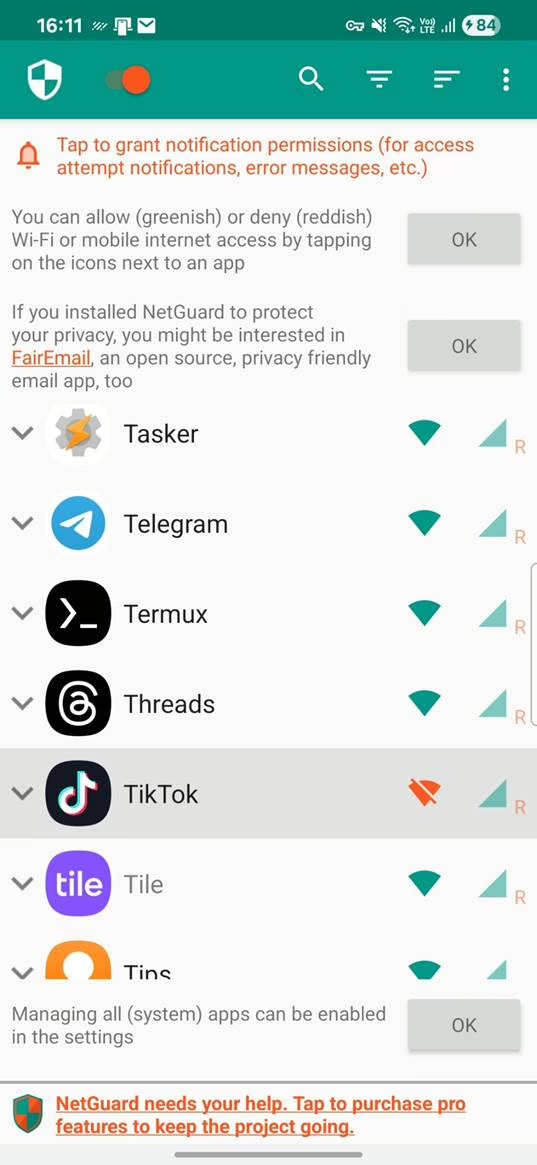
Firewall
NetGuard is a firewall solution for Android that allows you to control internet access on a per-app basis for non-rooted devices. It offers both simple and advanced options to block or allow network connections, giving you full control over which apps can access Wi-Fi and/or mobile data. Whether you’re looking to enhance privacy, reduce data usage, or prevent background activity, NetGuard provides an effective way to manage internet access for each app individually.
Conclusion
Shizuku is a game-changer for Android power users and cybersecurity enthusiasts. It bridges the gap between root and non-root access, enabling advanced functionality while keeping system integrity. Whether you’re debloating your phone, monitoring network activity, or exploring app internals, Shizuku allows you to do more—securely and efficiently.