![]()
A new browser attack vectors just dropped, and it’s called FileFix — an alternative to the well-known ClickFix attack. This method, discovered and shared by mrd0x, shows how attackers can to execute commands right from browser, without requesting target to open cmd dialog.
Quick Recap: What’s the ClickFix Attack?
First, let’s quickly recap ClickFix, the social engineering technique that hackers have been using to manipulate victims. At its core, ClickFix works by deceiving users into taking an action to “fix” a non-existent issue. This usually involves showing pop-ups with buttons like “Fix It” or “I am not a robot”.
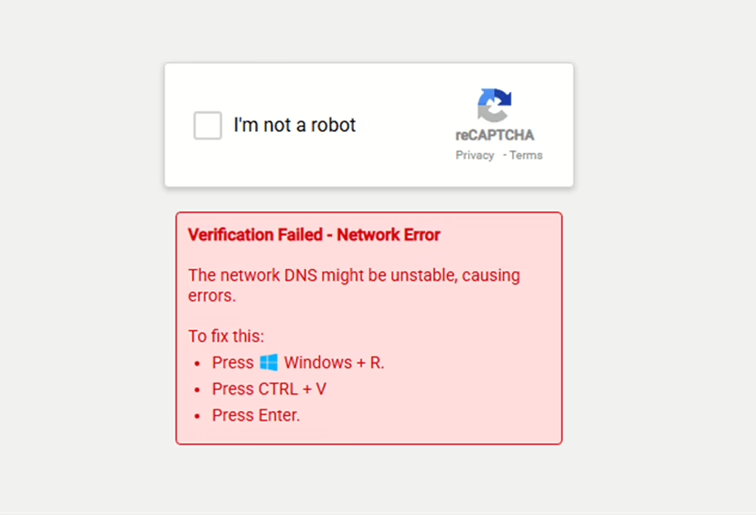
Once the user clicks, a malicious PowerShell script is automatically copied to their clipboard. Then, users are cunningly instructed to paste this script into their Windows Run dialog (by pressing Win + R and then Ctrl + V), thereby executing the malware themselves. This method is brilliant for attackers because it shifts the execution onto the user, avoiding some automated defenses. This technique was first detected around October 2023 and started gaining significant global adoption by late 2024, becoming quite popular by August 2024. It’s been widely adopted by various cybercriminals and even nation-state-sponsored APT groups. You might have seen it disguised as fake reCAPTCHA pages or bot protection prompts, pop-ups claiming browser issues, or even impersonating social media and cryptocurrency trading sites. In the wild, ClickFix has been spread through methods like spearphishing emails (including those with HTML attachments), malicious advertising (malvertising) on sites offering free content, phishing websites optimized for search results, compromised legitimate websites, and even spamming forums and social media. It’s often used to deliver infostealer malware like Lumma.
FileFix: Tricking the Browser into Launching Local Files
Now for the main event: FileFix! This is an alternative to the ClickFix attack. The main purpose of FileFix is to social engineer users into executing operating system commands without them ever needing to leave their browser window. Unlike ClickFix, which heavily relies on the Run Dialog, FileFix cleverly exploits the fact that the File Explorer Address Bar can actually be used to execute OS commands, and surprisingly, browsers don’t block this behavior.
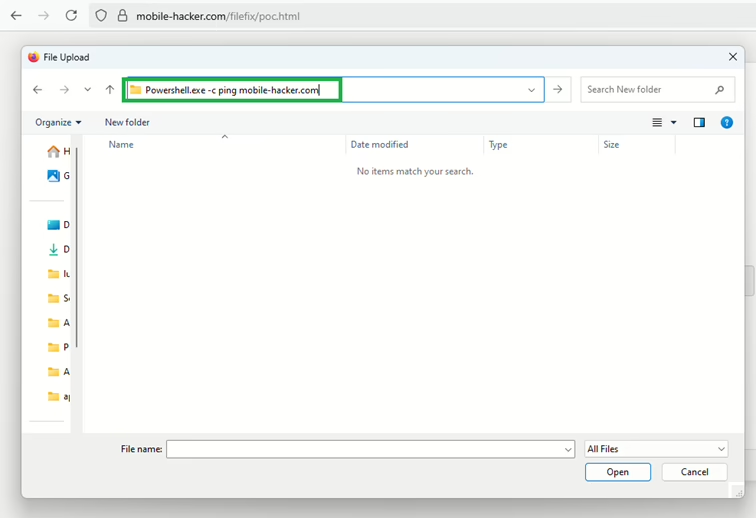
This means a malicious cmd.exe process can be spawned directly by a Chrome process, for example.
How does FileFix works?
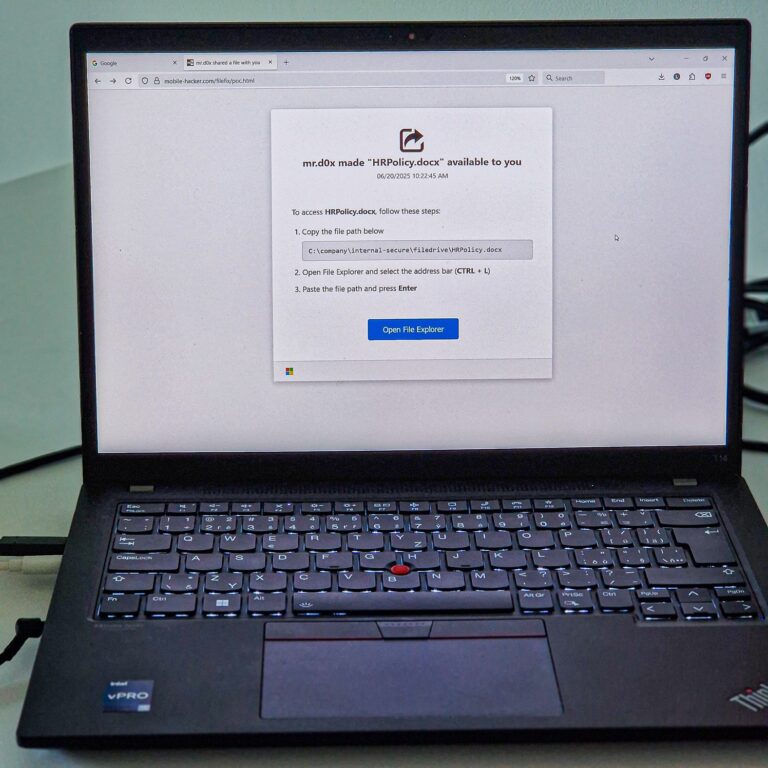
So, how would FileFix work in a real-world scenario? Imagine you’re browsing the web and land on a phishing page that looks like an internal company document sharing portal. The page might claim that HRPolicy.docx available to you, and tell you that to access this important document, you need to follow a few simple steps. It’ll instruct you to “Copy the file path below” which looks completely harmless, like C:\company\internal-secure\filedrive\HRPolicy.docx.

But here’s the trick: when you click on that “file path” or a button like Open File Explorer, the webpage actually copies a hidden malicious PowerShell command to your clipboard. This command is designed to look like the legitimate file path using a comment, for example: Powershell.exe -c ping example.com # C:\\company\\internal-secure\\filedrive\\HRPolicy.docx.
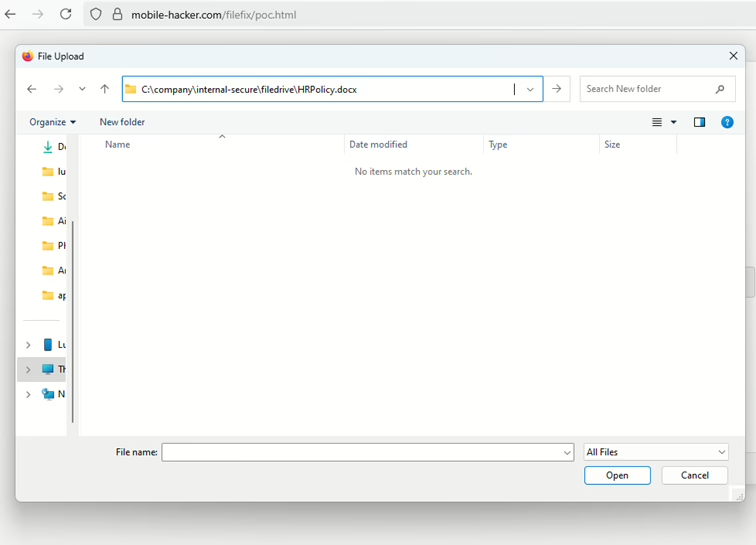
.docx)Next, the instructions tell you to Open File Explorer and select the address bar (CTRL + L) and then Paste the file path and press Enter. From your perspective, you’re just following instructions to open a document by pasting a file path into File Explorer. However, the moment you paste and hit Enter in the File Explorer’s address bar, you’re unknowingly executing that hidden PowerShell command.
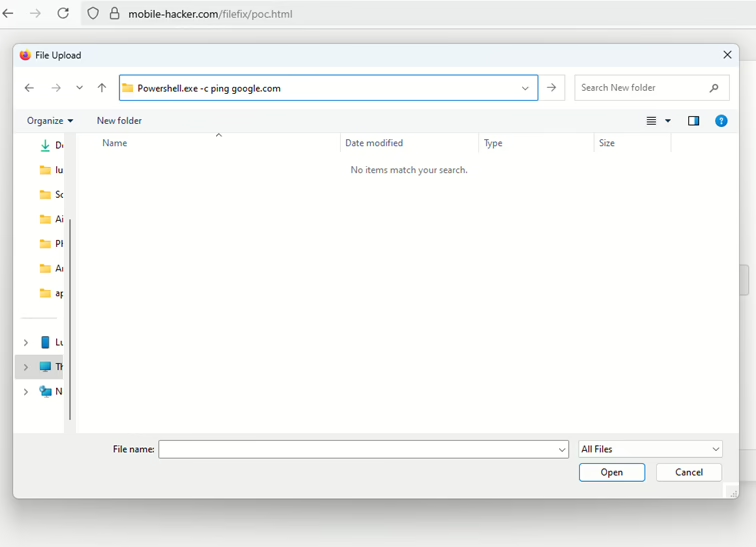
If you try to select a file for upload (since the attack leverages a file upload input), the script is designed to prevent it and tell you to “Please follow the stated instructions”.
Below is the whole text that is being automatically copied to clipboard:
Powershell.exe -c ping example.com # C:\\company\\internal-secure\\filedrive\\HRPolicy.docx Prevention
Alright, let’s talk about how to protect yourself and your company from these attacks:
- User Education is Key! This is paramount. Regularly train employees about social engineering tactics and new phishing schemes. Emphasize that any request for manual system manipulations is an alarming sign.
- Verify Links: Always verify the URI path, especially from unknown sources.
- Stay Informed: Keep up-to-date with the latest cyber threats and verify actions before execution. Blocking Indicators of Compromise (IOCs) from threat intelligence providers can also help.
In conclusion, FileFix represents an evolution in social engineering, taking a page out of ClickFix’s playbook but adapting it to exploit a different user interaction point: the File Explorer’s address bar via a browser’s file upload functionality. By seamlessly embedding malicious commands within seemingly legitimate file paths, it aims to trick users into executing malware without ever realizing they’re doing anything wrong.