![]()
Forget the laptop. With the right tools, your Android phone can become a portable multitool. Yes, even without root. Thanks to Termux and the clever termux-adb project, you can run ADB and Fastboot directly from your phone — no computer needed.
This guide breaks down how to install it, how it works, and practical use cases.
How to use ADB & fastboot in #Termux without root
— Mobile Hacker (@androidmalware2) June 16, 2025
You can use non-rooted Android to unlock bootloader, run ADB commands, remove bloatware, flash ROM, or even root another Androidhttps://t.co/T6ilwyuKxE pic.twitter.com/ZjCIo6wWFZ
Why Run ADB/Fastboot on Android?
Typically, ADB (Android Debug Bridge) and Fastboot are PC-based tools used for communicating with Android devices. They’re staples in the toolkit of security researchers, mobile testers, forensic analysts, and rooters.
Running these directly on a non-rooted phone offers advantages:
- No need for a second device (i.e., no laptop required).
- Find and remove bloatware
- Portable mobile forensics capability on the go.
- Use your daily driver to inspect, flash, or root other devices.
- A stealthier setup for security testing or emergency recovery.
How It Works
Termux runs in a limited Linux-like environment. The termux-adb project uses:
- Precompiled ARM adb/fastboot binaries.
- Symlinks and wrapper scripts to integrate with Termux.
- Android’s USB OTG support to connect and control external devices.
It’s a clever use of system permissions and user-space workarounds. No root. No kernel mods. Just smart Unix-style scripting.
Installation Guide
Here’s how to get adb and fastboot running on a non-rooted Android phone using Termux:
1. Install Termux and Termux:API
Download and install Termux and Termux:API apps from F-Droid.
2. Update Packages
pkg update && pkg upgrade
3. Install wget
pkg install wget
4. Run the Installer
curl -s https://raw.githubusercontent.com/nohajc/termux-adb/master/install.sh | bash
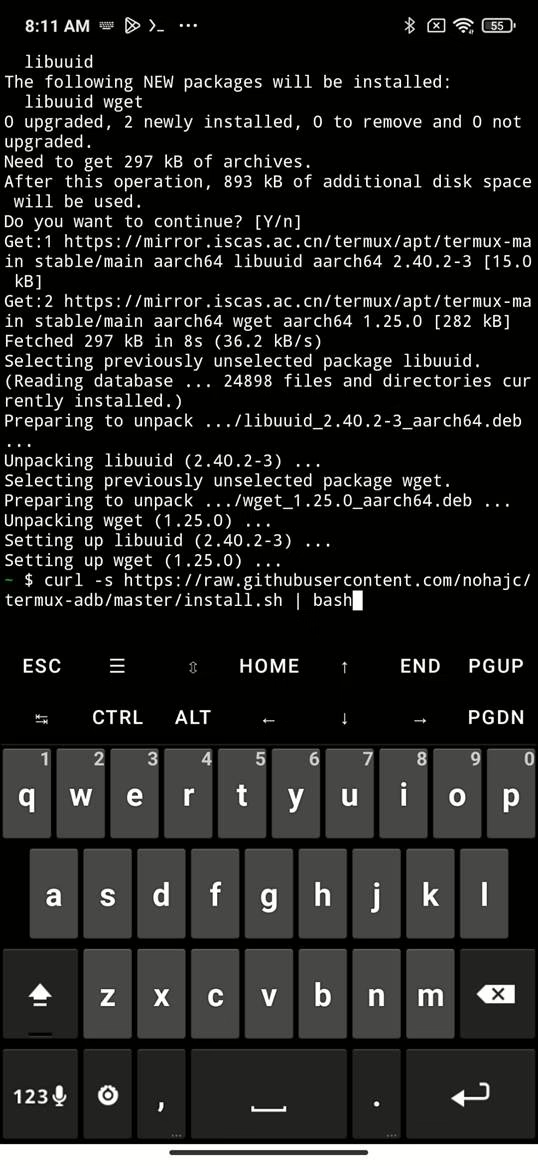
This downloads precompiled binaries and sets up symlinks for adb and fastboot.
Top 10 ADB Commands You Should Know
Whether you’re a hacker, pentester, or mobile analyst, these ADB commands are gold:
| Command | Description |
| adb devices | List connected devices |
| adb shell | Open remote shell on the device |
| adb pull <remote> <local> | Copy files from device to host |
| adb push <local> <remote> | Copy files from host to device |
| adb install <apk> | Install APK on the device |
| adb uninstall <package> | Uninstall an app |
| adb logcat | View system logs |
| adb reboot | Reboot the device |
| adb reboot bootloader | Reboot into bootloader mode |
| adb sideload <file.zip> | Flash ZIP via recovery |
(Source: awesome-adb)
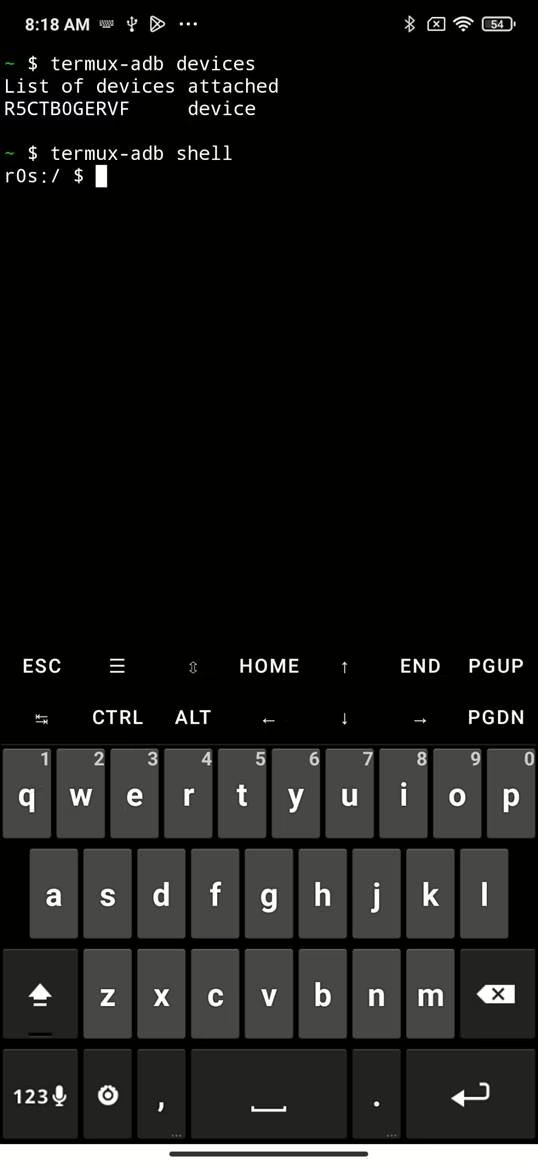
Real-World Use Cases
Identify and Remove Bloatware — No Root Needed
Using ADB, you can detect and disable or uninstall system-level bloatware on target devices. This is especially useful for de-googling, improving performance, or preparing devices for secure use.
Pair ADB with tools like:
adb shell pm list packagesadb shell pm uninstall --user 0 <package_name>adb shell pm disable-user --user 0 <package_name>
You can be inspired and search for unwanted preinstalled apps using Universal Android Debloater — an open-source command-line tool that provides a curated list of known bloatware packages from major OEMs and safely removes them. It contains a list of 2400 apps to find and either remove or disable on your smartphone. It supports debloating of various manufacturers and mobile carriers such as LG, Samsung, Xiaomi, Huawei, Oppo, Realme, Vivo, ZTE, OnePlus, Nokia, Sony, Asus, Google, Fairphone, Motorola, Tecno, Unihertz.

This kind of cleanup improves privacy, speeds up performance, and reduces attack surface — all without root.
On-the-Go Rooting
Use your phone to unlock bootloader, flash custom recovery such as TWRP and push Magisk to another phone. In between the commands you can also sideload custom ROMs. As a result, you can root other devices without needing a computer.
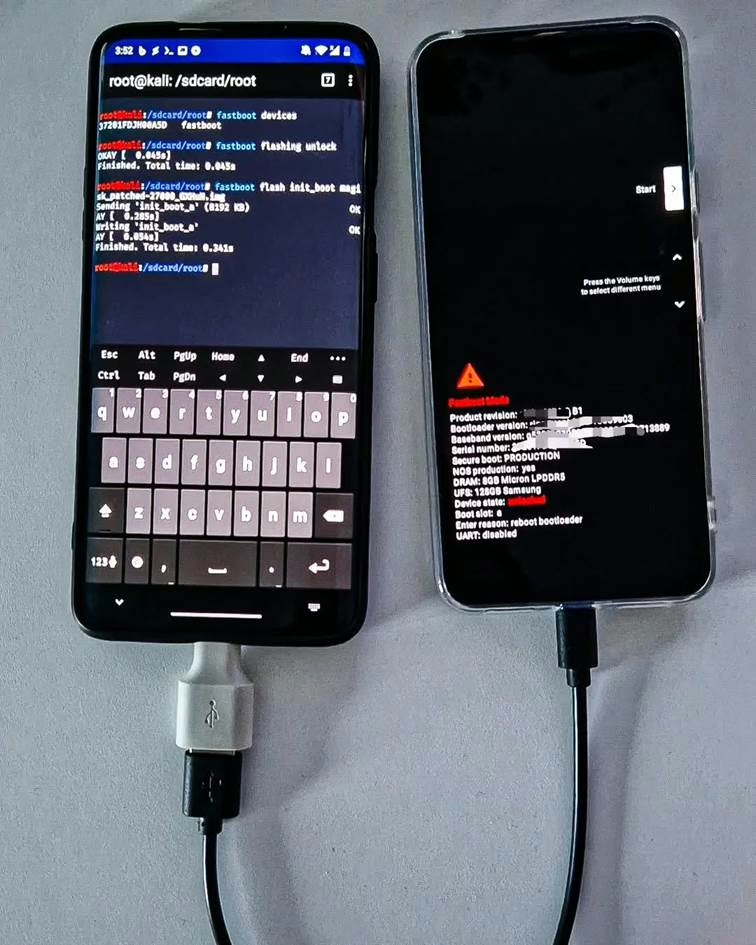
init_boot imagePentesting and bug hunting for low hanging fruit
It also has an exploitation surface when apps or systems are misconfigured. One common oversight is when developers forget to disable debug mode before releasing an app.
If an app’s AndroidManifest.xml file contains:
<application android:debuggable="true" />then that app can be directly accessed via ADB — no rooting required. This allows a pentester or bounty hunter to run commands as the app’s user with:
adb shell
run-as com.vulnerable.app
cd /data/data/com.vulnerable.app/The outcome? Full access to the app’s private storage — including databases, tokens, cached credentials, config files, or even offline user data.
Another common issue in AndroidManifest.xml is this flag:
<application android:allowBackup="true" />When enabled (which it is by default unless explicitly disabled), Android allows the app’s private data to be backed up via ADB — again, even on non-rooted devices. However, this applies only to apps targeting Android 11 and lower. The default behavior of adb backup changed in Android 12 to exclude app data by default for apps targeting that version or later. That means a user (or attacker) with USB debugging enabled can run:
adb backup -f backup.ab com.target.appThis silently dumps the app’s data into a backup file, which can then be converted to a tar archive and analyzed:
dd if=backup.ab bs=24 skip=1 | openssl zlib -d > backup.tar
tar -xf backup.tarFrom there, pentesters can extract databases, config files, internal preferences, or session information — all without needing to exploit the app directly.
ADB also played a key role in a recent real-world exploit: CVE-2024-0044, a vulnerability affecting Android 12 and 13. Researchers used ADB to exfiltrate sensitive data from WhatsApp, exploiting improperly protected content providers and IPC endpoints. This exploit didn’t require root — just an ADB session with basic permissions. It’s a textbook case of how powerful even “limited” ADB access can be when chained with app-level flaws. Read the full breakdown.
Misconfigurations like debuggable="true" and allowBackup="true" are often overlooked, yet they can turn even a hardened Android device into a leaky vault — especially when ADB is accessible. For pentesters and bug bounty hunters, these are low-effort, high-reward findings that can lead to deep app compromise.
Mobile Forensics
Extract dumpsys logs, installed apps, running apps, presence of root binaries and packages, last modified or created files on external storage, etc. One of the forensic tools that relies on ADB is Mobile Verification Toolkit.
Toolkits That Leverage ADB
Once you’ve got ADB running, a whole world of tools becomes available:
- Frida — A dynamic instrumentation toolkit. Inject scripts into running apps via adb shell, perfect for reversing and testing.
- HacknDroid — A Termux-based toolkit offering dozens of mobile hacking utilities including MITM attacks, payload generation, and more.

- PhoneSploit Pro — An ADB-based exploit tool with a web UI that lets you control connected devices, retrieve sensitive data, and execute remote commands.

A Note on Limitations
- Not all phones support OTG well. Test before relying on it.
- Target device must have developer mode and USB debugging enabled. This tool leverages USB debugging and not bypassing it.
- Some operations (like full image backups) may still require elevated permissions or rooted targets.
But for most everyday tinkering tasks — this setup is more than enough.
Final Thoughts
Running ADB and Fastboot from a non-rooted Android phone isn’t just cool — it’s practical. It enables pentesting, recovery, bloatware removal, mobile forensics, and even rooting or flashing another Android phone without ever touching a PC.

