![]()
What if someone could pinpoint your smartphone’s location and gather detailed device information without you ever installing a malicious app? This is precisely what the Seeker tool is designed to demonstrate, leveraging social engineering to accurately locate smartphones. In this post I will demonstrate how this tools appears to a potential targeted individual and how easy is for threat actor to set-it-up. I also included useful prevention tips to avoid becoming a victim.
What is Seeker and Its Purpose?
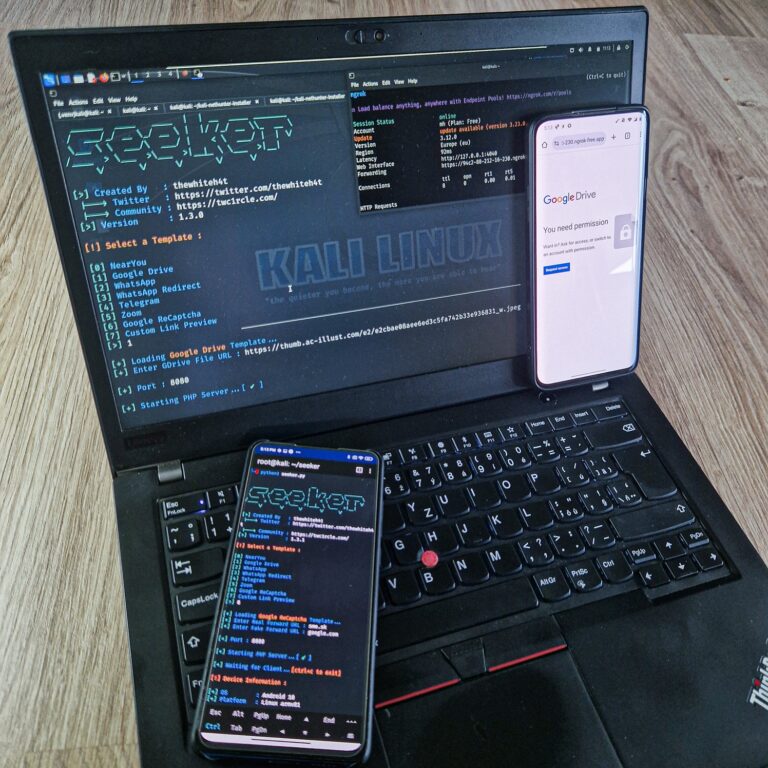
Seeker is a social engineering tool used for offensive security that allows users to accurately locate smartphones by simply having the target open a specially crafted link. Its core concept is straightforward: much like phishing pages are used to steal credentials, Seeker hosts a fake web page that requests location permission, similar to many popular legitimate location-based websites.

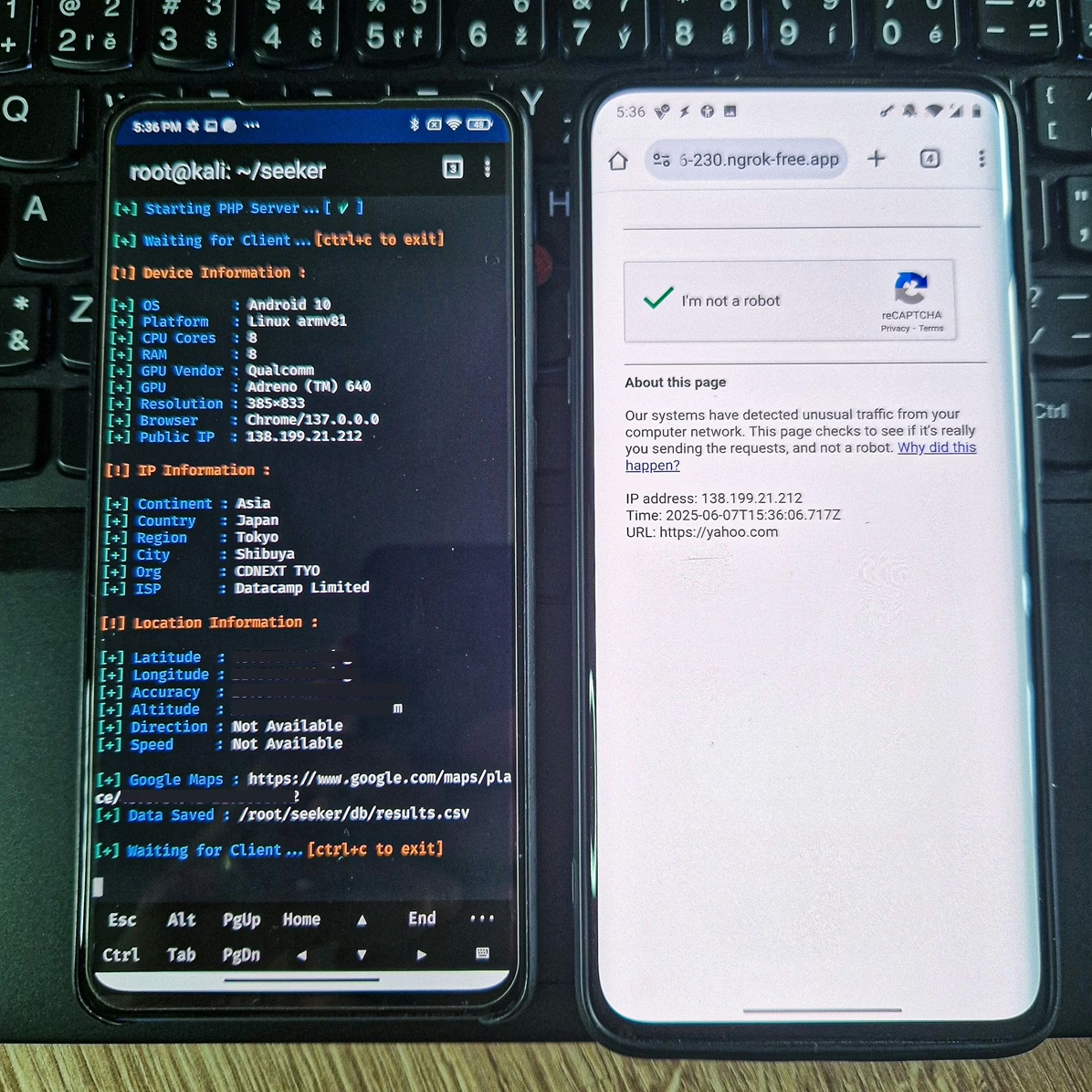
The primary purpose of Seeker is to obtain precise location data, including longitude, latitude, accuracy, altitude, direction (if moving), and speed. Crucially, it does this without requiring the installation of any application on the target device. Beyond location, Seeker can also gather a device information without any additional permissions, such as:
- Unique ID (via Canvas Fingerprinting)
- Device Model (if available)
- Operating System and Platform
- Number of CPU Cores (approximate) and Amount of RAM (approximate)
- Screen Resolution and GPU information
- Browser Name and Version
- Public IP Address and Local IP Address/Port
Automatic IP Address Reconnaissance is also performed after the initial information is received. This tool is presented as a proof of concept for educational purposes only, highlighting the kind of data a malicious website can collect from your devices and the risks of clicking on random links or granting critical permissions.
From Laptop to Smartphone
One of Seeker’s notable features is its versatility in operation. While it can be run from a laptop, it is also designed to be operated on the go via a smartphone from any Linux terminal, including Kali Nethunter or Termux. The sources indicate that Seeker has been tested on various Linux distributions like Kali Linux, BlackArch Linux, Ubuntu, Fedora, Parrot OS, and specifically mentions Kali Nethunter and Termux, as well as OSX.
How Seeker Works
The process relies heavily on social engineering and appears very natural to the target, minimizing “red flags” and the need for installing malicious software. Here’s a breakdown of how it operates:
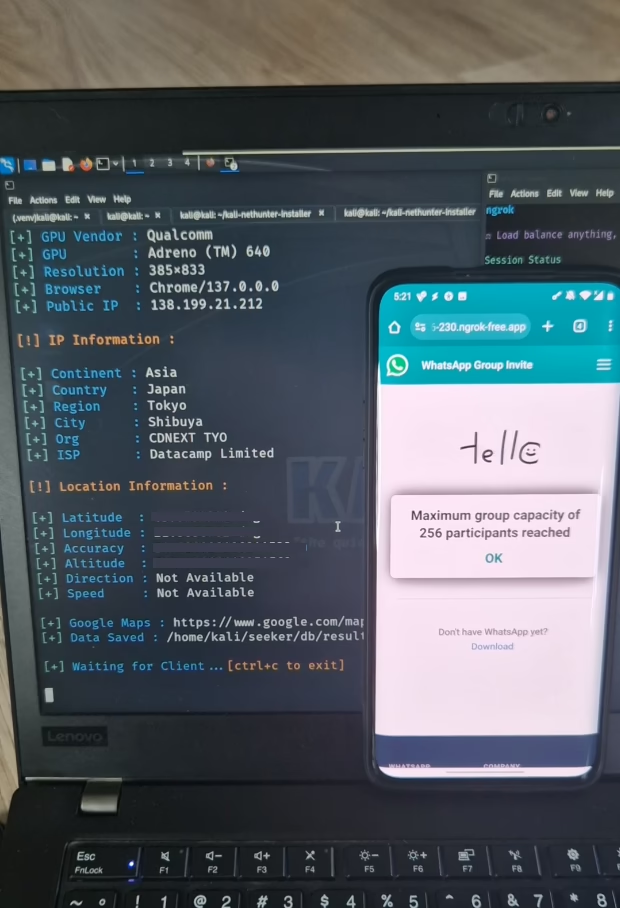
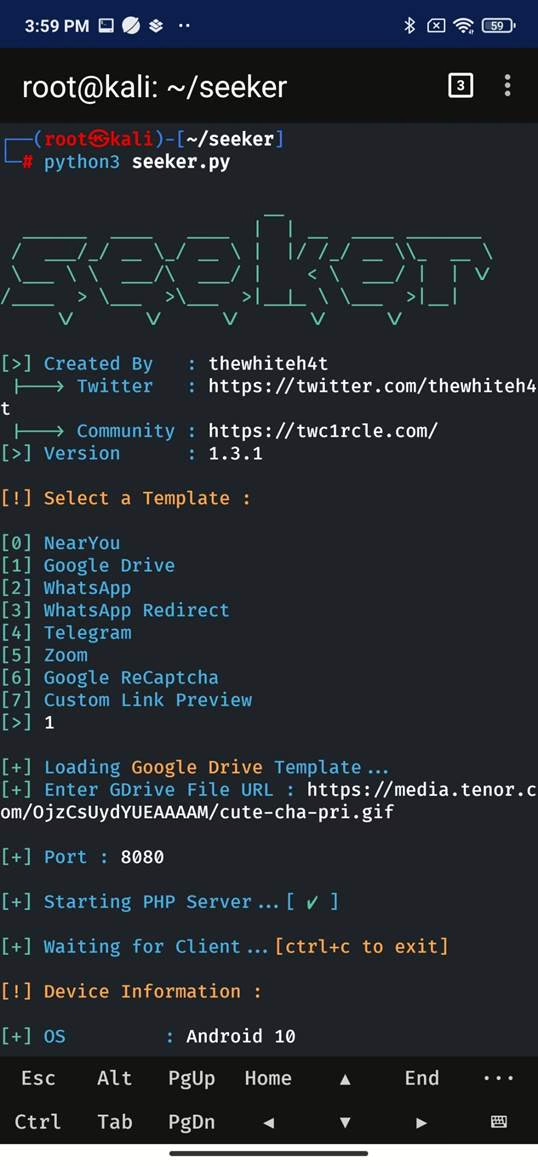
- Template Selection: The user first selects a template to serve as the lure for the fake website. Available predefined templates include “NearYou,” “Google Drive,” “WhatsApp,” and “Telegram,” among others. Users also have the option to create their own custom templates.
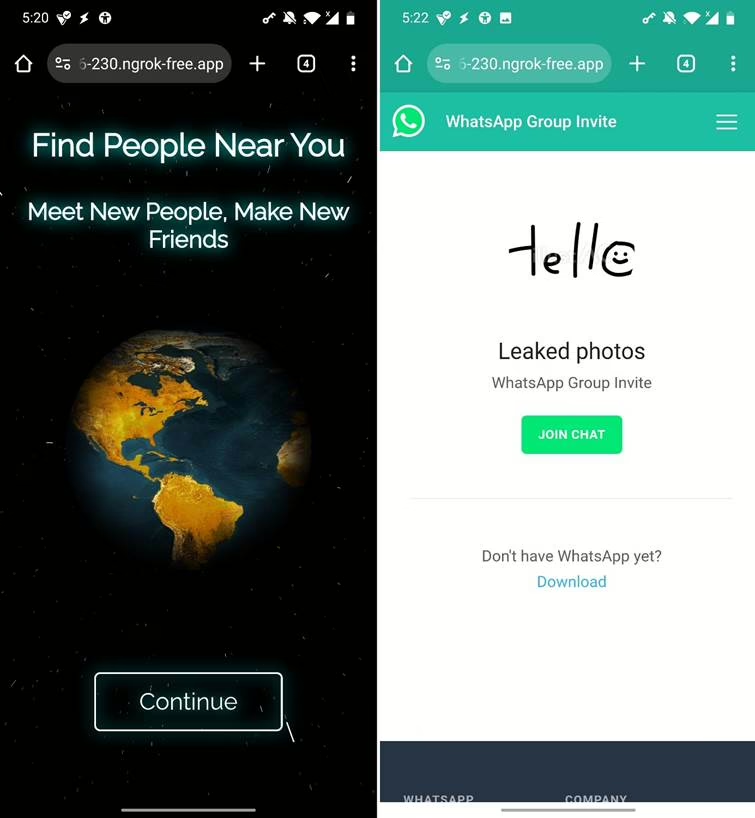
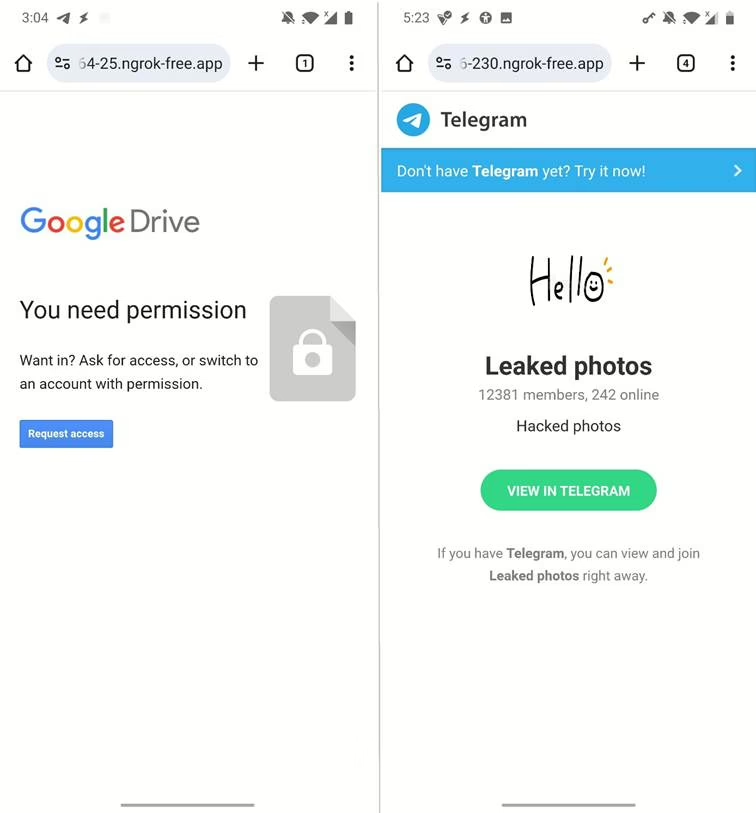
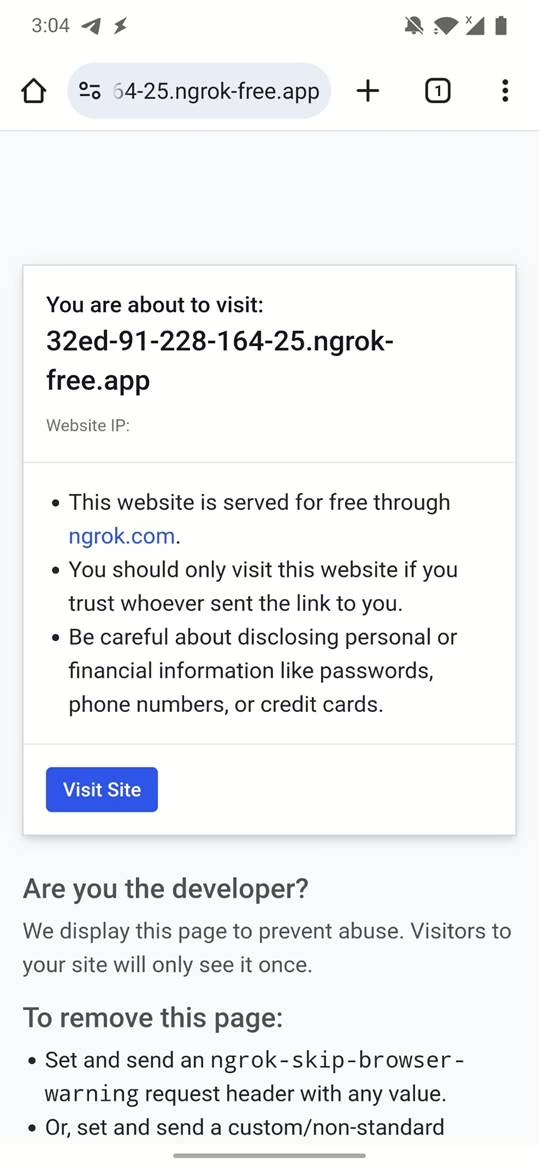
- Exposing the Local Server: Seeker runs a local PHP web server. To make this local server accessible from the internet, the user needs to start a tunneling service like ngrok. ngrok creates a secure tunnel, exposing the local server to the internet through a public URL. If users visit ngrok website for the first time, they are present with prevent abuse website, however it can be skipped by account owner.
- Sharing the Lure Link: Seeker generates a disguised link embedded with a geolocation script. This link is then shared with the target through communication channels like email, text messages, or other platforms. For added trustworthiness, this link can be obfuscated via link shorteners (a common practice in social engineering, though not explicitly tied to Seeker in the sources) to make it seem more legitimate.
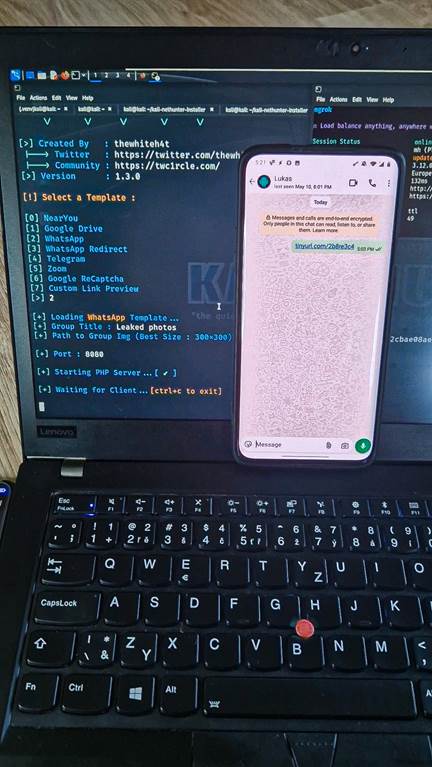
- Target Interaction and Location Acquisition: When the target opens the link in their web browser, the embedded script initiates the collection of location data.
- If the browser already has location permissions enabled for the specific site or generally, the location information (from GPS, Wi-Fi triangulation, or IP-based geolocation) will be automatically shared back to the Seeker server.
- If location permission is not already granted, the fake website will naturally prompt the user to enable location access on behalf of the lure (e.g., “Will you allow [URL] to access your location?”). This interaction appears very natural, without the suspicious indications of installing a malicious application.
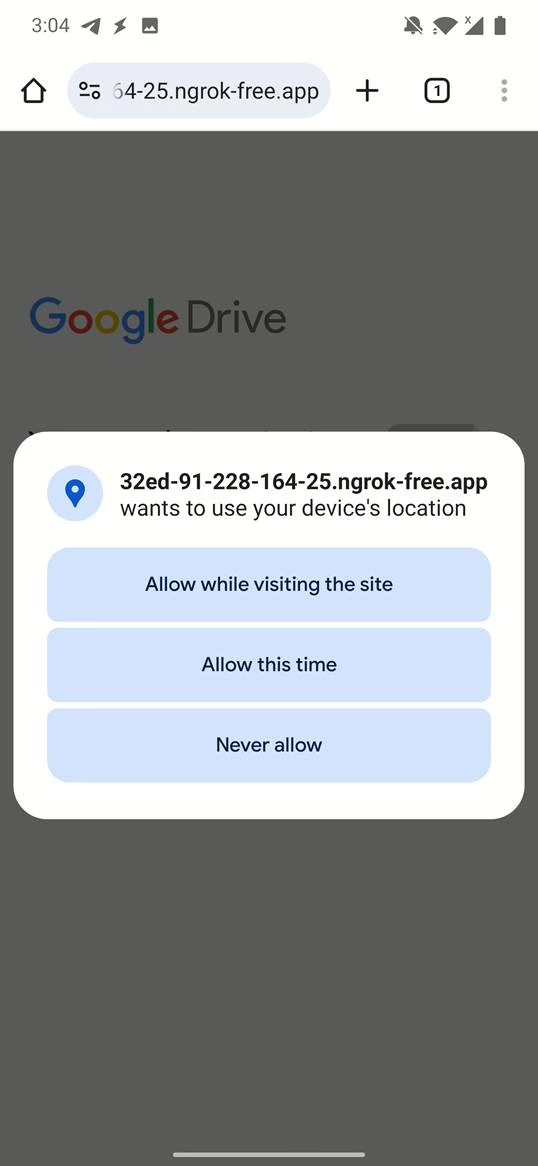
- Real-time Processing and Display: The collected data is processed in real-time, analyzed, and mapped using APIs like Google Maps to determine and display the device’s exact location on an intuitive interface, along with additional details like timestamps.
Prevention Tips: How to Avoid Becoming a Victim
Given how effective Seeker can be, understanding prevention is crucial. The tool itself underscores the importance of not clicking on random or unknown links and being cautious about allowing critical permissions such as location access.
To protect yourself:
- Be wary of unknown links: Always question the legitimacy of links received via email, text messages, or social media, especially if they seem unexpected or too good to be true.
- Review browser permissions: Regularly check and disable browser permissions that you don’t actively use or trust. Specifically, be mindful of which websites have access to your location.
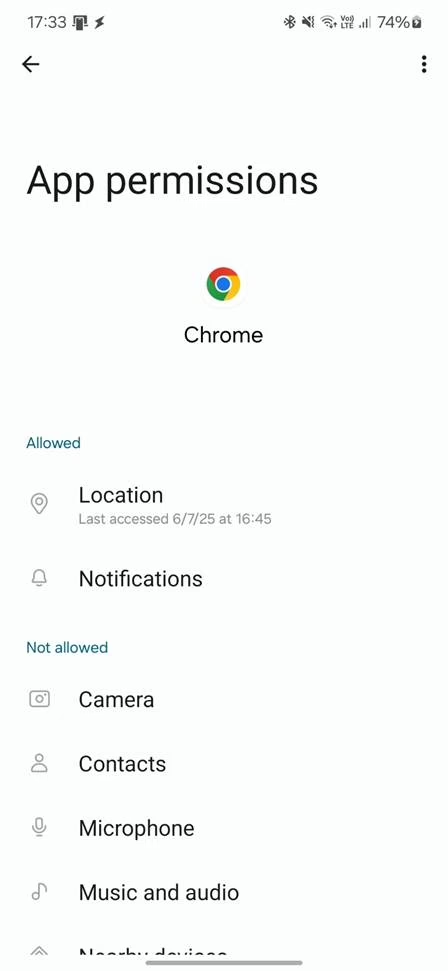
- Understand social engineering tactics: Recognize that attackers often craft convincing lures that appear natural and harmless, designed to trick you into granting permissions or providing information.
- Prioritize privacy: Be aware that even if you don’t grant explicit location permission, a malicious website might still gather other device information like your IP address, operating system, and browser details.
Conclusion
The Seeker tool illustrates how easily a smartphone’s precise location and other device information can be obtained through social engineering, simply by the target opening a link. The ease of setup, even on a smartphone using terminals like Termux or Nethunter, makes it accessible. If a browser’s location permission is already enabled for the site or generally, the location can be captured automatically without additional prompts. Therefore, prevention is crucial. Always use caution when encountering unknown links, and make it a habit to disable browser permissions that you do not genuinely use or require.