![]()
Bluetooth Human Interface Device (HID) profiles allow devices like keyboards, mice, and game controllers to communicate wirelessly with hosts like laptops, smartphones, TVs, and tablets. This functionality enhances user experience by eliminating the need for cables. However, this convenience might come with risks. Bad actors can leverage this technique to impersonate these devices and inject keystrokes that allows an attacker to open unwanted website, install malware or lockout user from the smartphone. Further I will explain how Bad Bluetooth attacks work, how they can be carry on by mobile gadgets such as Flipper Zero and rooted Android smartphone running NetHunter.
What Is a Bluetooth HID Attack
A Bad Bluetooth HID attack also known as Bad keyboard, operates by impersonating a legitimate HID device to trick the target host. By masquerading as a trusted keyboard or mouse, the attacker can inject keystrokes or mouse movements into the victim’s system, potentially triggering unauthorized commands. The attack can be executed by a device either its supported built-in Bluetooth chipset or using external Bluetooth adapter. Besides mobile devices such as rooted Android, Flipper Zero or Raspberry Pi, the attack can be accomplished from computer as well.
How it works
The attack vector typically involves the following steps:
Recon and impersonation: The attacker can scan Bluetooth devices within the range and impersonate any discovered device by using its name and even MAC address. In Figure 1 you can see an example of impersonating Beoplay P2 Bluetooth speaker using Flipper Zero and NetHunter at the same time. Having more devices having the same name creates a confusion for a user, which might result it connecting to attacker controlled device.
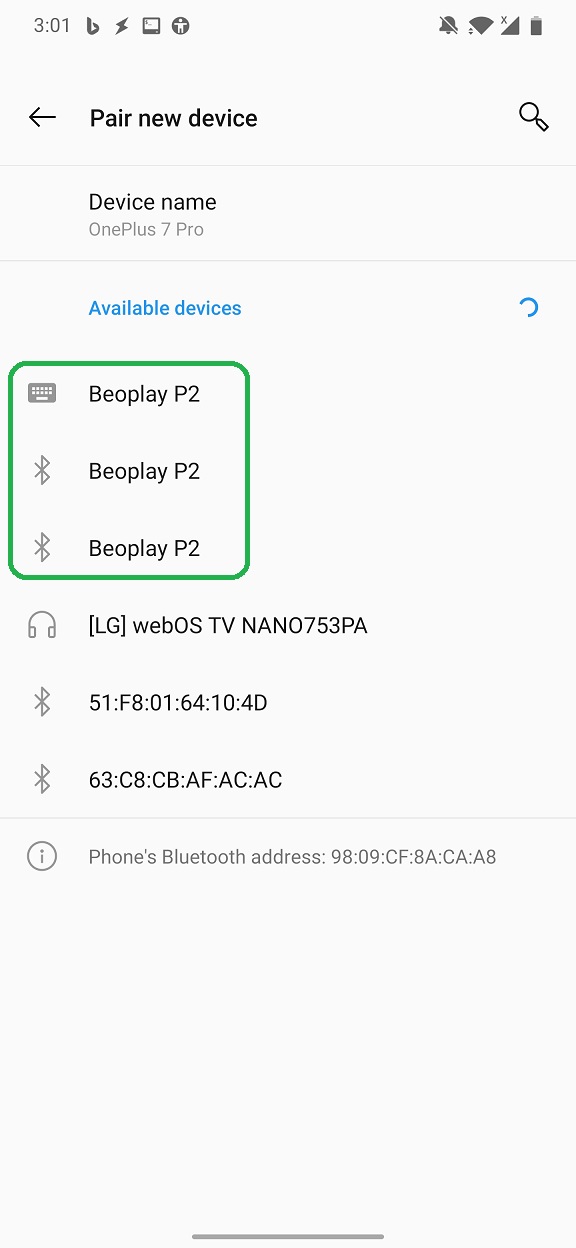
Bluetooth Pairing: Pairing process to cloned device is not requesting any authentication or PIN verification from user side. Once user connects to device, attacker is notified by knowing device Bluetooth visible name and MAC address, see Figure 2.
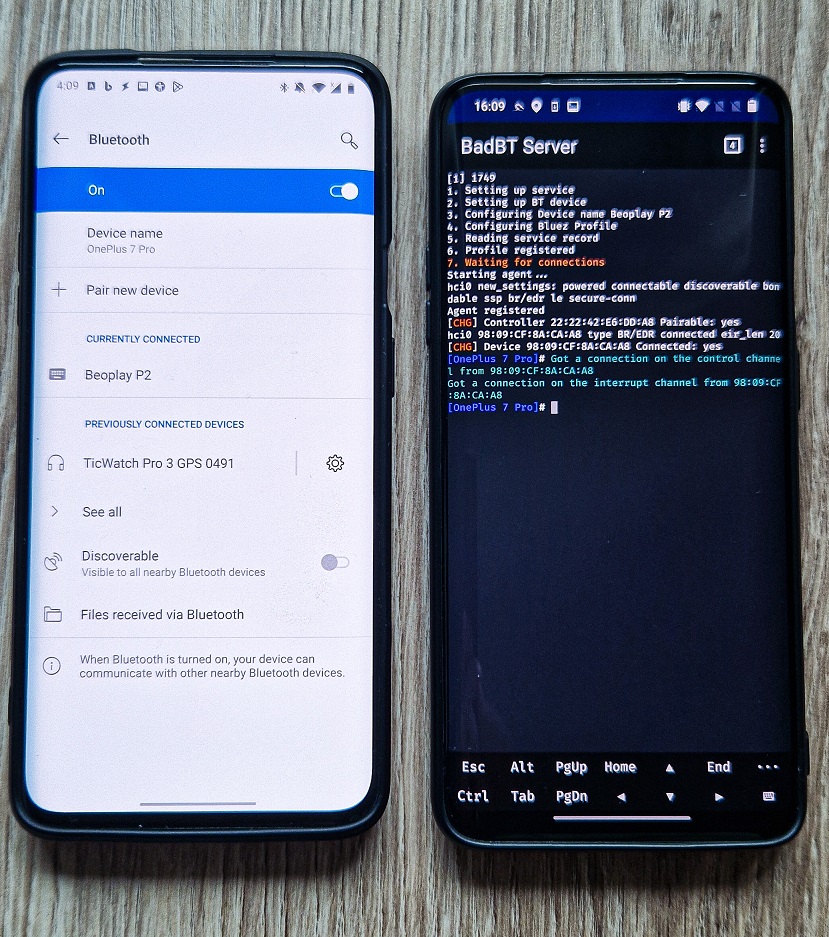
Keystroke Injection: With the connection established, the attacker can send keystrokes to the victim’s device. This allows an attacker to run BadUSB (Rubber Ducky) scripts over Bluetooth. Such scripts allows the attacker to execute predefined actions by emulating keyboard input. You can read more about Rubber Ducky scripts in Ultimate guide to HID attacks using Rubber Ducky scripts and Bad USB MITM attack post.
Bad Bluetooth using Flipper Zero
Using an additional gadget, such as Flipper Zero, that is running unofficial firmware, you can use BadBT app to inject Rubber Ducky script to paired device. You can read more about Rubber Ducky scripts in Ultimate guide to HID attacks using Rubber Ducky scripts and Bad USB MITM attack post. Below is a demo how such scenario might look like.
Bad Bluetooth using NetHunter
In December 2023, @yesimxev implemented Bad Bluetooth feature in NetHunter. This feature was last week officially announced and released as part of Kali NetHunter 2024.1 update. I already play around with it, and it works well. In the video below, I rickrolled Windows 10 machine after it connected to Evil Keyboard device.
@yesimxev pushed it even further and ported Bad Bluetooth to NetHunter variant for smartwatches, specifically TicWatch 3 pro. Which means that right now it is possible to inject keystrokes over Bluetooth from a wrist. Video by yesimxev is demonstrated below.
How to setup Bad Bluetooth using NetHunter
To make Bad Bluetooth work, you need to have custom NetHunter kernel flashed in rooted Android. This kernel needs to support either internal Bluetooth chipset or external adapter. On top of that, you need to run the latest version of NetHunter.
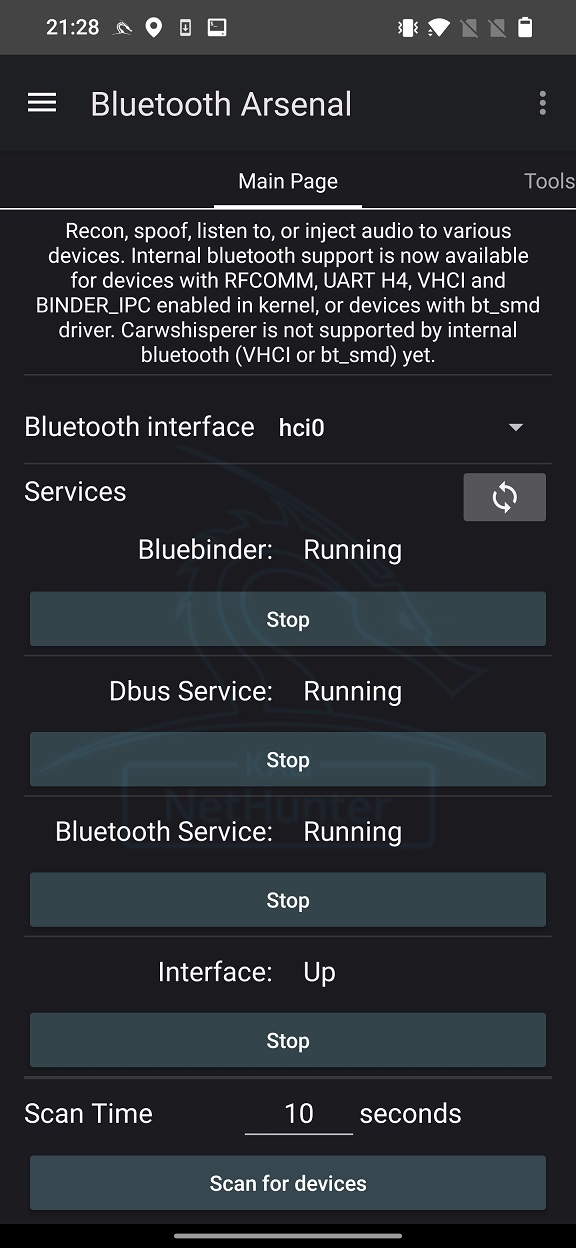
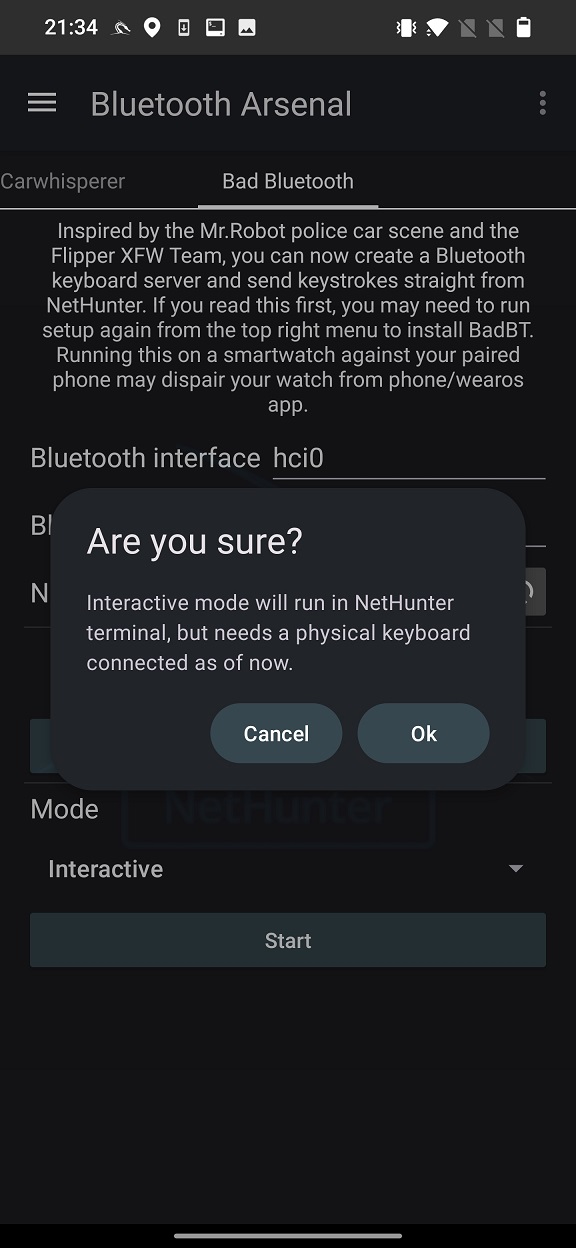
In order to start Bad Bluetooth server, we need to enable Bluetooth interface. Open NetHunter app, go to Bluetooth Arsenal, and start Bluebinder service. If your built-in chipset or external adapter is supported, then it will be recognized new Bluetooth interface, see Figure 3. Select the interface and start Dbus Service, Bluetooth Service, and Interface.
In Bad Bluetooth tab you can set Bluetooth MAC address and discoverable name.
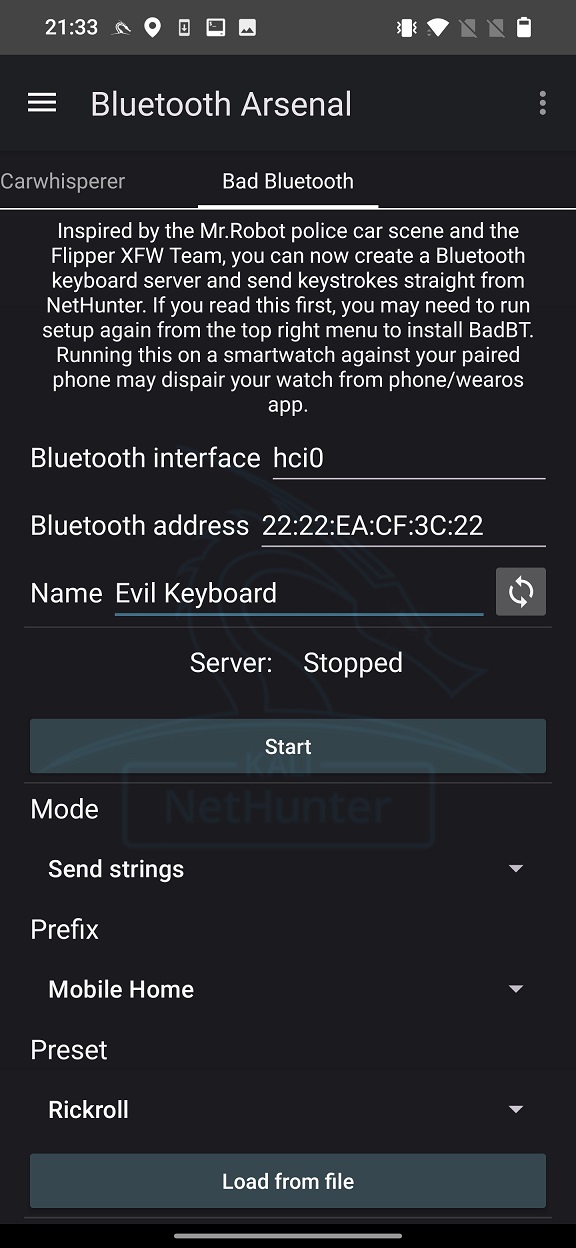
Start the server that will open NetHunter Terminal and executes a script that starts spoofing Bluetooth device. If everything works fine, you should see the same terminal output as in Figure 5.
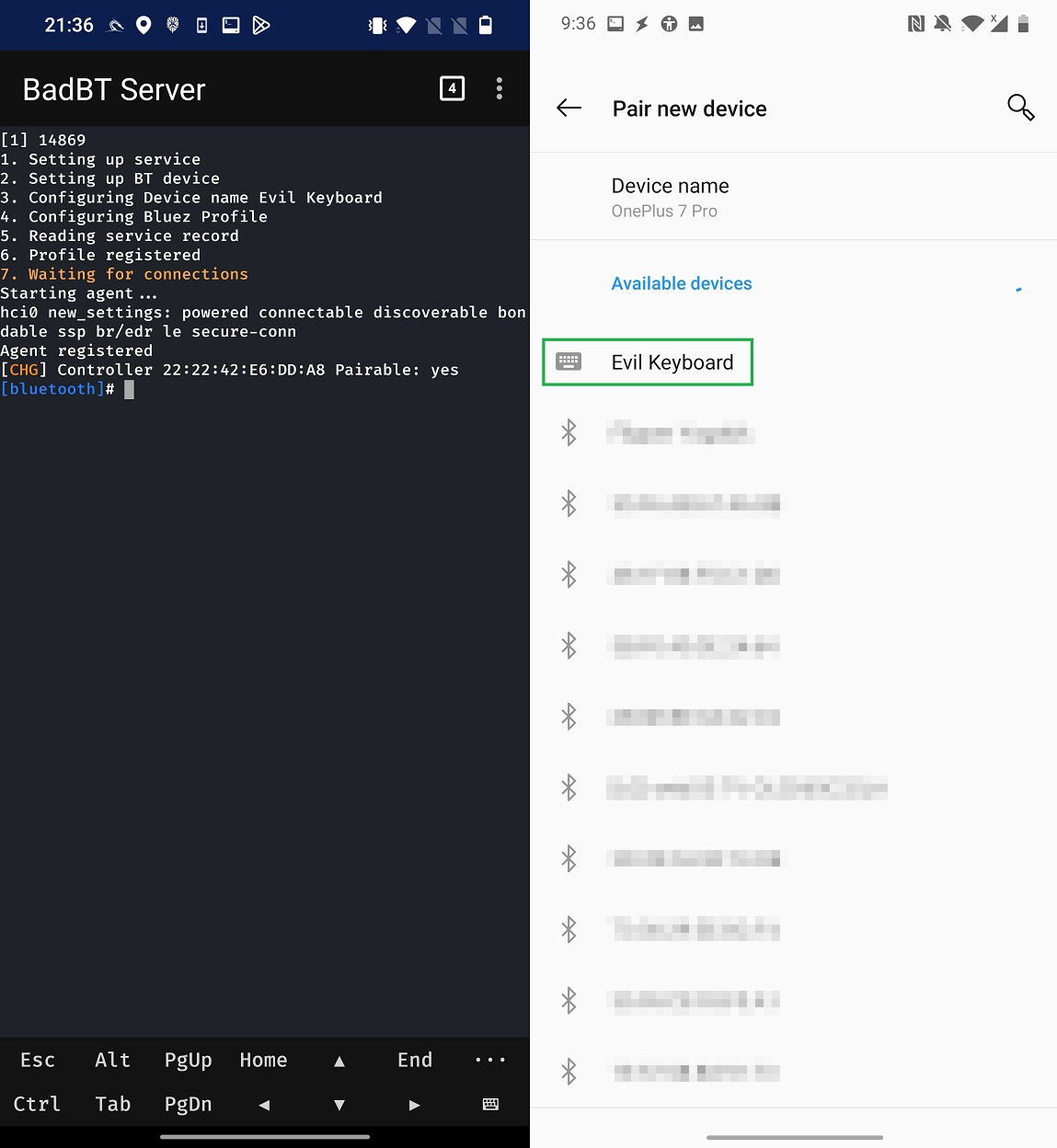
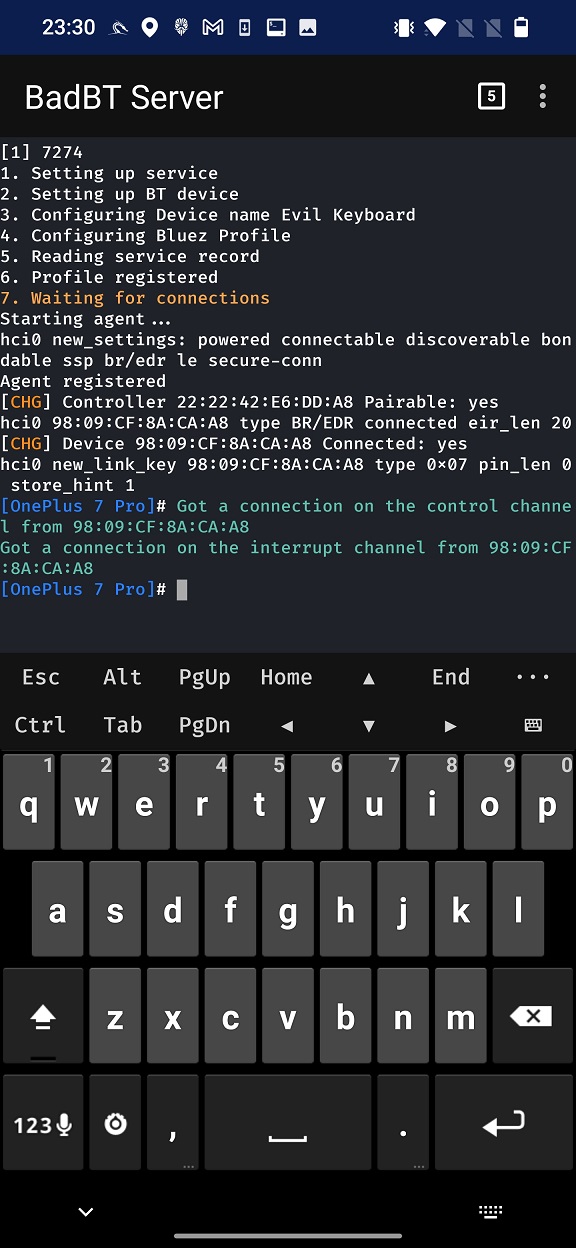
Other devices within the Bluetooth range can see Evil Keyboard device. When I connect to it using another smartphone (OnePlus 7 Pro), server recognizes the client, and we can continue with injecting keystrokes in NetHunter app.
Once we are connected with a device, we can send a keystrokes. We can select one of two Modes, Send strings or Interactive. Interactive mode requires physical keyboard that would be used to send keys. However, this mode for some reason wasn’t working for me. Send strings will forward predefined string.
Prefix allows you to select the target such as Mobile Home, Mobile Browser, Windows CMD, Mac Terminal, Linux Terminal or None.
Preset right now includes predefined Rubber Ducky scripts Rickroll, Fake Windows Update, and None. If you choose None, you can either Load from file strings to send or write them manually in String to inject edit box. When you tap on Start, keystrokes injection starts.
Change spoofed device appearance
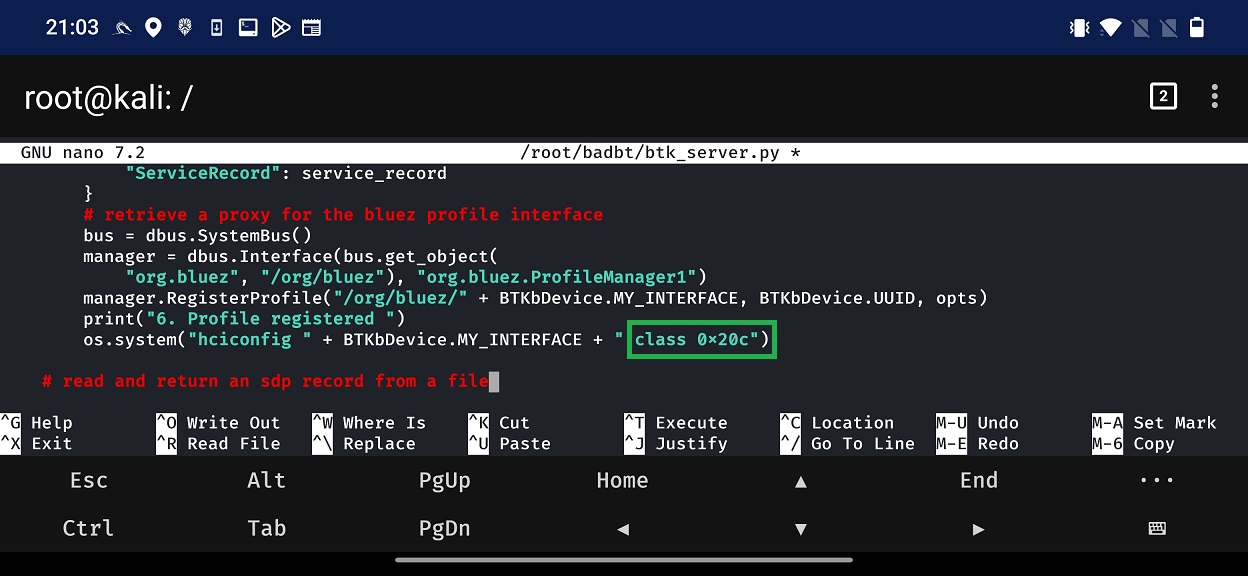
From the above Figure 5, spoofed device always appears as a keyboard. This is visible as an icon next to the device name. This icon is set based on the Bluetooth device class. Where different class ID represents different device type such as laptop, headset, smartphone etc. Device class value is hard-coded in the script that is responsible for starting Bad Bluetooth server. Because of that, it isn’t possible to change the class value from NetHunter app. If you would like to change the icon appearance, then you needs to edit /root/badbt/btk_server.py script and alter the class value represented as HEX. Specific line in a code and class are visible in Figure 8.
List of various Device classes are available online, for example here. On the website you can choose major and minor class, see Figure 9.
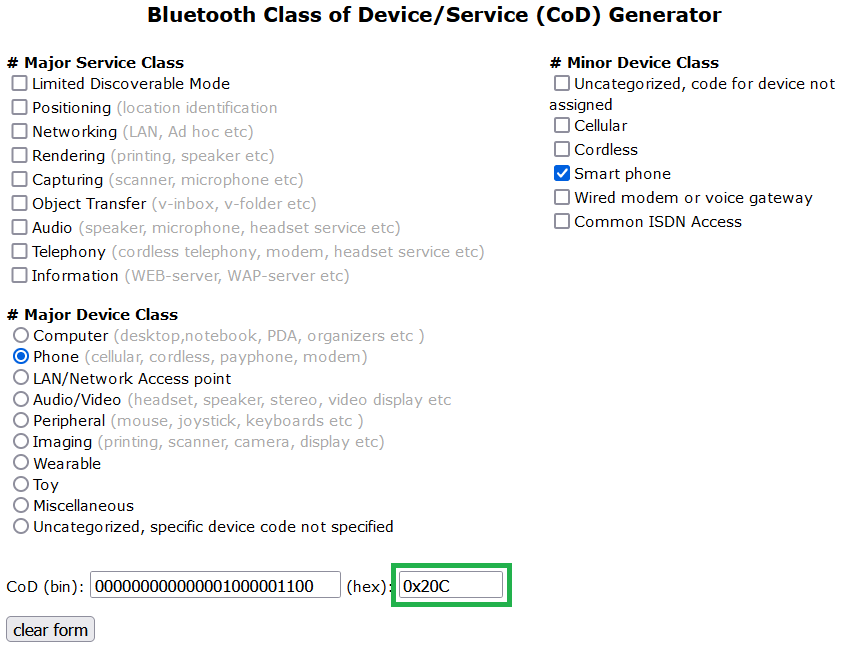
By changing IDs, you can make sure spoofed device will be visible as you want. Few examples are in Figure 10.
Bad Bluetooth using NetHunter without user interaction
Scenarios above requires user interaction – search and connect – to specific device. However, because of recently discovered 0-click Bluetooth vulnerability (CVE-2023-45866), these actions from user are not necessary anymore.
Critical Bluetooth vulnerabilities (CVE-2023-45866, CVE-2024-21306) allow keystroke injection without user confirmation. These affect Android, Linux, macOS, iOS, and Windows, posing a serious threat. Marc Newlin discovered these vulnerabilities and published proof-of-concept scripts. Using these scripts, attacker forces Bluetooth pairing without user confirmation to inject keystrokes into unpatched Android and Linux devices.
Prevention
Disable Bluetooth when not in use, especially in public places. Keep your devices updated with the latest security patches. Be cautious when pairing with new devices and verify their legitimacy.
Conclusion
In conclusion, Bad Bluetooth HID Attacks pose a significant threat to the security and privacy of Bluetooth-enabled devices. By exploiting HID profiles, attackers can execute keystroke injection attacks, compromising user data and system integrity. However, with proactive security measures and user awareness, the risk of exploitation can be significantly mitigated, ensuring a safer and more secure Bluetooth ecosystem for all users.

